|
1
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
2
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
3
|
How To Prevent Automatic Turning Off Of Your iPhone Screen |

|
iPhones are the most prestigious devices in the technological market today. They mainly symbolize class since only the people with money can afford them. Many people are obsessed with iPhones due to the many features that this phone has that other ...
Author: James Fleming |
|
|
|
|
4
|
What causes the download to be slow? The Practical Ways to Fix It |

|
Have you ever faced a scenario where you're waiting for an hour just to load your favorite movie on Netflix? If you're having a slow download speed, then it can be pretty common. People wonder about the scenario despite having a decent connection. If...
Author: Tithi Raha |
|
|
|
|
5
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
6
|
What Are The Best Backup Services Strategies You Should Try? |

|
Are you aspiring to perform data recovery in your organization or want to hire someone? Before starting over, it is a wise idea that you understand the best backup services strategies.
There are several important backup services strategies users in ...
Author: Faith Cheruiyot |
|
|
|
|
7
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
8
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
9
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
10
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
11
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
12
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
13
|
Why is my download speed so slow when I have fast internet? |

|
If your internet connection is fast but your internet download speed is slow, you can follow the workarounds below to resolve the issue.
There are several reasons why the internet may seem slow even if you have a high-speed internet connection. Re...
Author: Fay Kokri |
|
|
|
|
14
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
15
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
16
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
17
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
18
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
19
|
Computer Repair: How to Detect Crypto Mining Malware |

|
The vast growth of the cryptocurrency market has been something to marvel at over the past few years. However, the concept of anonymous payouts has given cybercriminals a reason to be part of the game. They have developed crypto-mining malware that c...
Author: Ian Musyoka |
|
|
|
|
20
|
How to create an invisible folder on your Windows 10 Computer |

|
How to create an invisible folder on your Windows 10 Computer
Do you have questions on how to create a hidden folder on your Windows 10 computer? Worry no more. With this informative piece, we will be sharing with you a step-by-step guide on this. F...
Author: Gloria Mutuku |
|
|
|
|
21
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
22
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
23
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
24
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
25
|
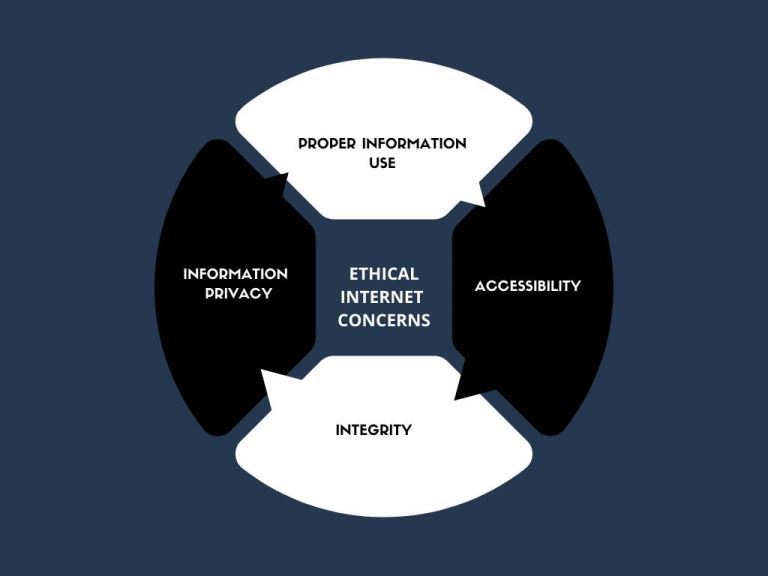
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
26
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
27
|
Are Windows Computers better than Mac |

|
In everyday life, we often come across the term PC, which stands for a personal computer. This is the most direct definition of a PC; however, the term is also commonly used to refer to all other computers except Mac. Similarly, in this article, we w...
Author: Collins Okoth |
|
|
|
|
28
|
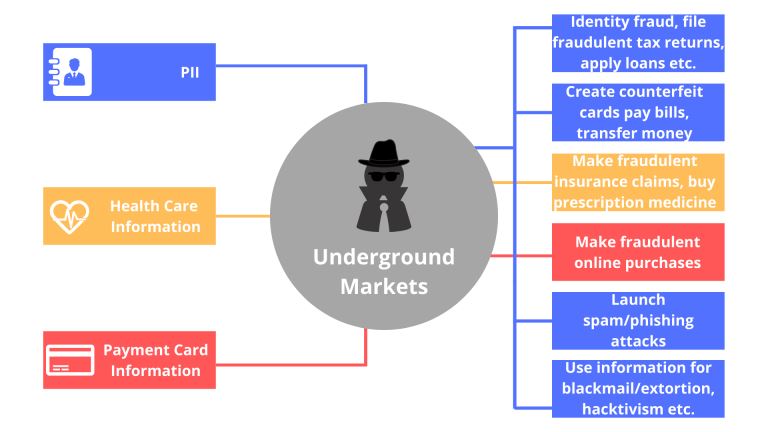
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
29
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
30
|
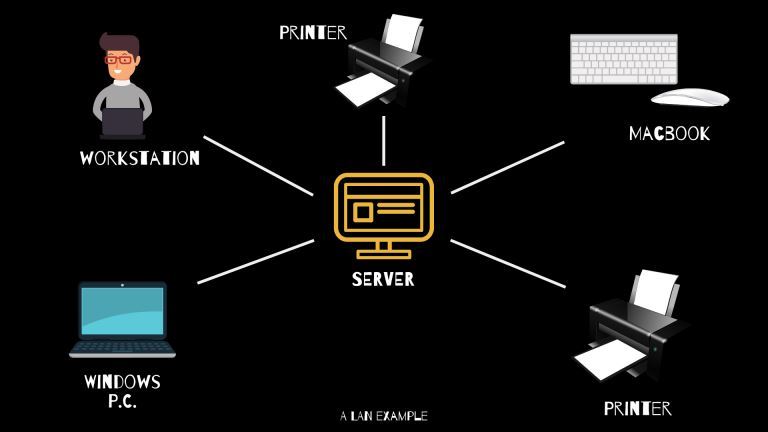
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
31
|
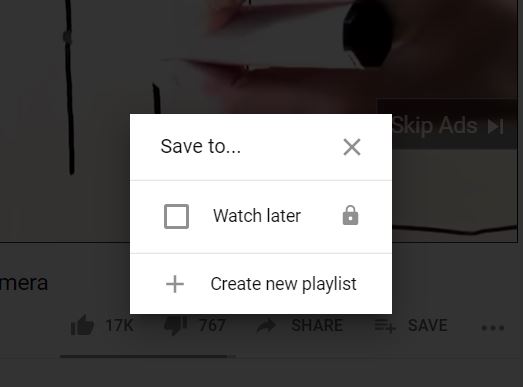
How Do I Download or Save a YouTube Video to My Computer? |
|
The YouTube design is such that users only get the chance to view the videos on their webpage. If you are the type of person who is always on the run or in situations with little or no internet connection, this might not be ideal for you. Many people...
Author: Delilah Daut |
|
|
|
|
32
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
33
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
34
|
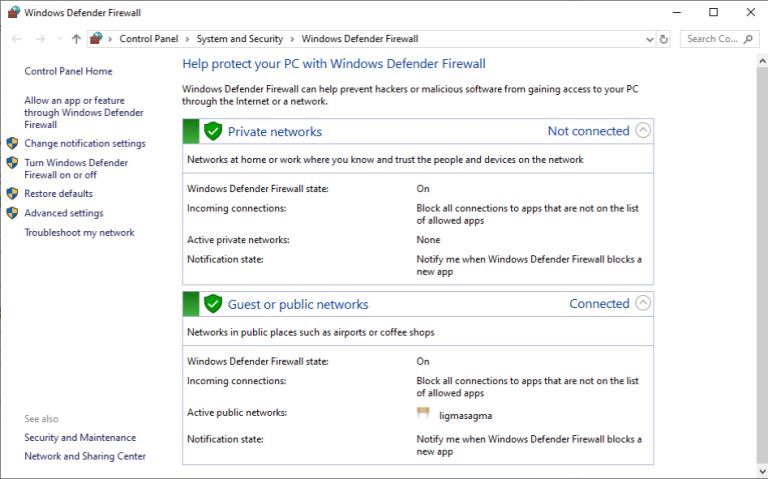
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
35
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|