|
1
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
2
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
3
|
How Is Binary Converted to Electrical Signals? |

|
Uncover the mystery of binary code and delve into the conversion process to electrical signals. If you're seeking knowledge on binary-electrical signal conversion, this article offers a comprehensive and user-friendly examination of the topic. Expand...
Author: Newton Waweru |
|
|
|
|
4
|
Why Are Binary Numbers Used in Electronics? |

|
Discover the fascinating world of electronics. Ever curious about the significance of binary numbers in this industry? This article will uncover the key role of binary in electronics and examine its use for data communication and processing. Get read...
Author: Newton Waweru |
|
|
|
|
5
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
6
|
What Are The Best Backup Services Strategies You Should Try? |

|
Are you aspiring to perform data recovery in your organization or want to hire someone? Before starting over, it is a wise idea that you understand the best backup services strategies.
There are several important backup services strategies users in ...
Author: Faith Cheruiyot |
|
|
|
|
7
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
8
|
What Are The Basic Rules to Design a Theater? |

|
Designing a theatre comes with its own set of unique challenges and considerations. From the size and shape of the space to the type of seating, there are many factors to consider when creating a theatre.
There are some basic rules in designing a th...
Author: Faith Cheruiyot |
|
|
|
|
9
|
What Are The Best Ways To Organize files on a New Computer? |

|
Did you just buy a computer and wonder how to organize your files? While it's not the most glamorous activity, organizing computer files is essential. They often build up without your knowledge until, one day, you turn on your computer to find a des...
Author: Caroline Chebet |
|
|
|
|
10
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
11
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
12
|
What Android Repair Experts/Technician Want You to Know |

|
When it comes to android repair, with many guides on social media, many people think it's a do-it-yourself task, forgetting they need expert services and advice. It would be great to learn more about android repair from an expert's perspective. This ...
Author: Nancy Museo |
|
|
|
|
13
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
14
|
How to repair windows 10 automatic repair loop? |

|
An automatic repair loop in Windows 10 appears when you try to boot your computer but can’t and having an endless circle to try repair itself. If Windows 10 can’t repair itself, it will reboot and continues with the same circle.
This can be not ver...
Author: Berts Njoroge |
|
|
|
|
15
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
16
|
How to create an invisible folder on your Windows 10 Computer |

|
How to create an invisible folder on your Windows 10 Computer
Do you have questions on how to create a hidden folder on your Windows 10 computer? Worry no more. With this informative piece, we will be sharing with you a step-by-step guide on this. F...
Author: Gloria Mutuku |
|
|
|
|
17
|
How do I change the default destination for my downloads? |

|
The default destination for downloads on computers running Microsoft Windows Operating System (Windows 7, Windows 8, or Windows 10) is the C:/drive. The C:/drive is also the windows system drive where the operating system is located. For a computer ...
Author: Ujunwa Chibuzor |
|
|
|
|
18
|
How to connect two Windows 10 computers wirelessly? |

|
Connecting two computers is so important to share files. If you want to share files with your colleagues or friends, you will need to connect their computers with yours.
There are several ways you can connect two windows 10 computers wirelessly, whi...
Author: Berts Njoroge |
|
|
|
|
19
|
Is my computer worth fixing? |

|
Constant computer breakdowns can be frustrating, and if you are a frequent visitor to the repair shop you might start thinking of buying a new computer. However, a computer technician can advise you on the condition of your machine and if it is likel...
Author: Gloria Mutuku |
|
|
|
|
20
|
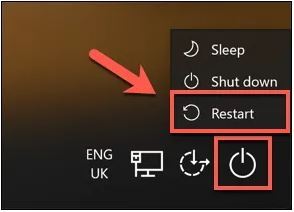
How to Factory Reset Windows 10 Without Logging In? |
|
Sometimes a factory reset on your Windows 10 system is necessary. Perhaps, you want to wipe off the data before selling it. Or, maybe your system is too sluggish and continuously showing an error message. A factory reset is a solution to all these is...
Author: Tithi Raha |
|
|
|
|
21
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
22
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
23
|
How does Chromecast work technically? |

|
Chromecast is a small disc-shaped device from Google that plugs into the High-Definition Multimedia Interface (HDMI) port of your television. It streams content through the Wi-Fi connection of your mobile device or computer, from streaming services s...
Author: Ujunwa Chibuzor |
|
|
|
|
24
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
25
|
What is the Internet of Things IoT |
|
The Internet of things (IoT) is a general term for the increasing number of electronics that are not conventional computer equipment but connected to the Internet to send information, receive instructions, or both.
Tech analyst company IDC forecasts...
Author: Collins Okoth |
|
|
|
|
26
|
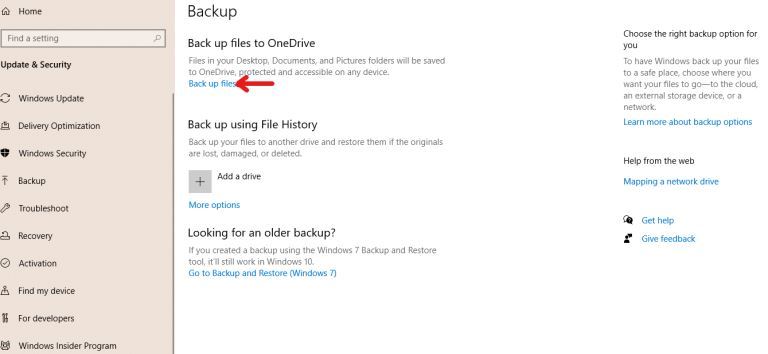
How to Backup Computer Windows 10? |
|
Backing up your computer windows 10 isn’t optional but a necessity.
The process starts by clicking on the “start” button on your Windows 10 system, navigating to the “setting” page, then to the “update & security” section, clicking on “backup,” and...
Author: Tithi Raha |
|
|
|
|
27
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
28
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
29
|
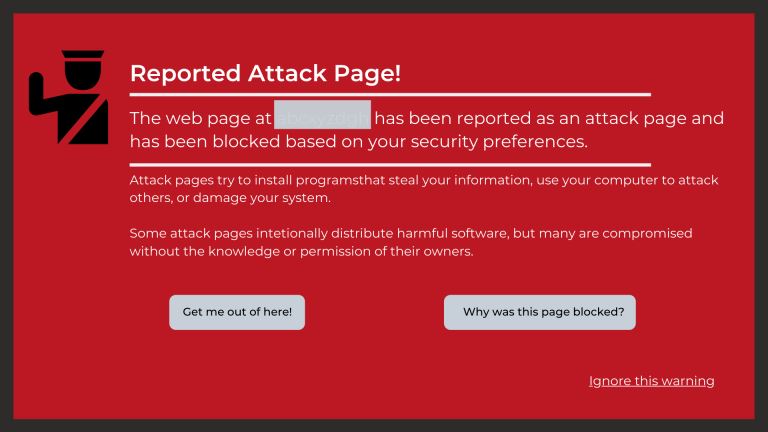
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
30
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
31
|
How to Get Rid of Computer Pop-Ups |

|
If you have had the chance to encounter pop-ups when working with your computer, you understand how frustrating and irritating it can get. They will slow down your device and even create a gateway for other malware to infect your computer. No compute...
Author: Cate Greff |
|
|
|
|
32
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|
|
33
|
How To Reinstall Windows 10 |

|
If your computer's performance has taken a nosedive recently, reinstalling Windows 10 - also known as a PC reset - might be the perfect solution. This is a somewhat extreme way of spring cleaning your hard drive, but it's certainly effective. If you'...
Author: Trey Williams |
|
|
|
|
34
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|