|
1
|
How have Online Scams Evolved Cybersecurity and Digital Deception |

|
Understanding the evolution of online scams is essential in this digital age. As someone who has thoroughly studied this issue, I share your concerns about this complex and ever-changing problem. This article is here to help, presenting a detailed lo...
Author: Newton Waweru |
|
|
|
|
2
|
How To Protect Children from Predators and Online Grooming |

|
As a caring parent, guardian, or educator, ensuring children's safety, especially from online predators and grooming, is a pressing concern. We understand your worries, and you're not alone. In this article, we're exploring key strategies to protect ...
Author: Newton Waweru |
|
|
|
|
3
|
What Does a VPN Do Securing Digital Privacy |

|
Navigating the digital world can feel like walking through a minefield. Leveraging years of research, we'll unravel how VPNs safeguard your online presence, preserving your privacy and security. Brace yourself for an informative journey into what a V...
Author: Newton Waweru |
|
|
|
|
4
|
What are the 10 Commandments of Computer Ethics |

|
Navigating the digital world with respect and integrity is essential. As an expert in computer ethics, I've delved into the 10 Commandments of Computer Ethics, the cornerstone of responsible digital behavior. This article aims to help you better und...
Author: Newton Waweru |
|
|
|
|
5
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
6
|
What Is a Burner Phone, and When Should You Use One |

|
I have been wondering how a burner phone can be used or if it is necessary to have one. I am sure I'm not the only one with such questions, so I did my research and wrote this article on burner phones and in which instances they can be helpful to bot...
Author: Janet Kathalu |
|
|
|
|
7
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
8
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
9
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
10
|
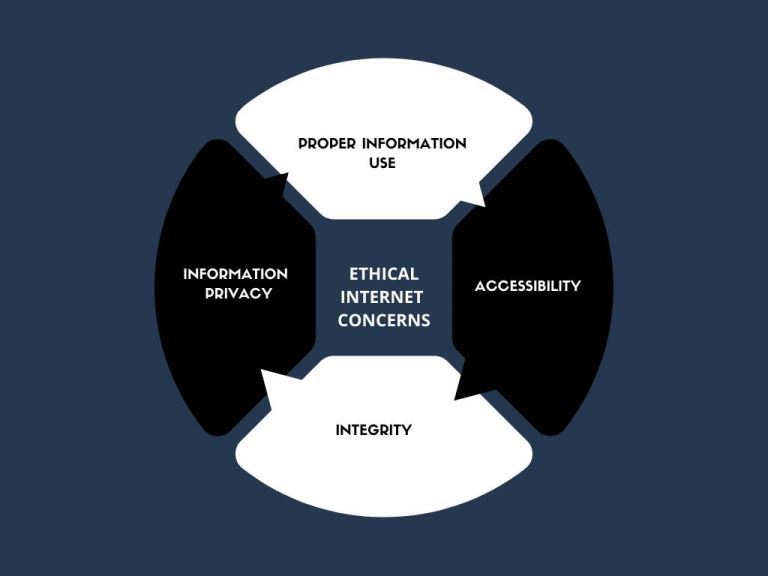
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
11
|
A Detailed Guide to Removing Ransomware in Windows 10 |
|
One of the main problems faced by internet companies today is Ransomware. For this reason, cybersecurity has continued to grow as an industry in general. Unfortunately, players on both sides can easily be described as the bad guys and the good guys. ...
Author: Collins Okoth |
|
|
|
|
12
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
13
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|