|
1
|
How Much Would it Cost to Fix Your iPhone |

|
It's common for the screen, charging port, or back screen of your iPhone to break. And when this happens, you only have two options; to repair or replace. Purchasing a new iPhone comes with standard prices that are easily verifiable online. But for r...
Author: Eunice Njuguna |
|
|
|
|
2
|
Why Do You Need a Computer Repair Technician in Topeka Kansas |

|
For a regular computer user, motherboards, processors, servers, or any other computer parts seem nothing more than just a pile of hardware and wires. However, a technician for Computer Repair Topeka, KS, or any other area can check these parts, diagn...
Author: Tithi Raha |
|
|
|
|
3
|
What Does a Computer Repair Topeka KS Technicians Do |

|
Computer Repair Topeka, KS technicians perform all the necessary steps to repair the malfunctioning computer software and hardware. Upon calling a technician, they will first diagnose the issues with your computer system and ensure all are returned t...
Author: Tithi Raha |
|
|
|
|
4
|
What Are The Duties of a Computer Repair Technician in Topeka KS |

|
From diagnosing initial issues to finding a solution, a computer repair technician in Topeka or any other area is responsible for all phases of the entire repair process. Moreover, the primary duty of a repair technician is to leave your device funct...
Author: Tithi Raha |
|
|
|
|
5
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
6
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
7
|
Data Restore: How to conduct data recovery on Windows |

|
Data recovery on Windows is a simple process. There are several steps you follow to achieve your desired results. Many Windows users face issues when conducting data recovery on their devices. Data recovery is not that hard, all you need is to follow...
Author: Faith Cheruiyot |
|
|
|
|
8
|
How to Recover Deleted Files from Hard Drive |

|
Do you want to recover some deleted files from your hard drive, or do you want to start a data recovery business? When you want to restore data from a hard drive, it's not that hard. You need to follow several steps after knowing the cause of the dat...
Author: Faith Cheruiyot |
|
|
|
|
9
|
What Are The Precautions To Consider When Backing Up Your Data? |

|
Did you know that backing up your data is essential to protect yourself from losing critical files? Backing up your data means making copies of your data and storing them in a safe place.
There are many ways to back up your data, and your best metho...
Author: Faith Cheruiyot |
|
|
|
|
10
|
How Soon After Damage Can I Get My Iphone Fixed? |

|
iPhone users face different problems when using their phones. It forces them to take them to repair to resolve the issues. The duration taken depends on the level of damage. You must be careful when using your iPhone to prevent issues, as they can lo...
Author: Faith Cheruiyot |
|
|
|
|
11
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
12
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
13
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
14
|
How to Fix a Tablet That Won't Connect to Wi-Fi |

|
Most WI-FI connection issues result from different issues which are fixable. One must follow several steps and perform different actions to fix the issues. Troubleshooting WIFI issues are common amongst tablet users. If it's a software cause, you can...
Author: Faith Cheruiyot |
|
|
|
|
15
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
16
|
Things You Didn't Know About Backup Services [What Are They?] |

|
A good backup service is crucial for ensuring all your data is safe from hardware failure or accidental deletion. Backup services offer companies and individuals the protection they need to keep their data safe. With backup services, companies can co...
Author: Faith Cheruiyot |
|
|
|
|
17
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
18
|
Internet Connection: Why Is My Internet So Slow |

|
We all have experienced slow internet speeds in our homes. I will guide you on the best way you can speed up your home internet, how different factors affect your speeds, and getting the best internet plans for your home or office. I will also guide ...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
20
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
21
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
22
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
23
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
24
|
How to stop a computer from overheating when playing games? |

|
As an avid gamer, you've probably spent thousands of dollars on a high-end gaming rig. So imagine your disappointment when your Desktop PC freezes or even shuts down abruptly mid-game.
The culprit here is most likely to be overheating. While modern ...
Author: Ujunwa Chibuzor |
|
|
|
|
25
|
What Are Ethical and Unethical Practices Related to Internet Use? |
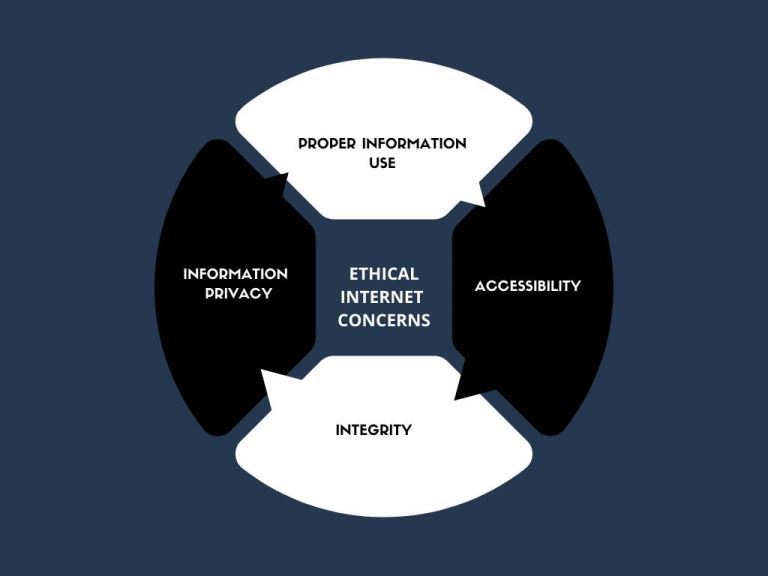
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
26
|
How to Backup Computer Windows 10? |
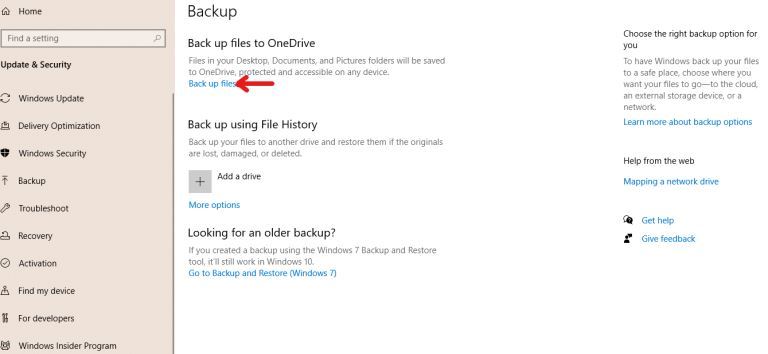
|
Backing up your computer windows 10 isn’t optional but a necessity.
The process starts by clicking on the “start” button on your Windows 10 system, navigating to the “setting” page, then to the “update & security” section, clicking on “backup,” and...
Author: Tithi Raha |
|
|
|
|
27
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
28
|
A Detailed Guide to Removing Ransomware in Windows 10 |
|
One of the main problems faced by internet companies today is Ransomware. For this reason, cybersecurity has continued to grow as an industry in general. Unfortunately, players on both sides can easily be described as the bad guys and the good guys. ...
Author: Collins Okoth |
|
|
|
|
29
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
30
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
31
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
32
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
33
|
How to Get Rid of Computer Pop-Ups |

|
If you have had the chance to encounter pop-ups when working with your computer, you understand how frustrating and irritating it can get. They will slow down your device and even create a gateway for other malware to infect your computer. No compute...
Author: Cate Greff |
|
|
|
|
34
|
How Do Computer Hard Drive Works |

|
A reliable and high-performance hard drive is essential. How? It acts as storage for your documents, videos, music, and more. Not only that. It also allows you to run your operating system, games, and other applications fast.
What you need to know i...
Author: James Fleming |
|
|
|