|
1
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
2
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
3
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
4
|
Regaining Access to Your Android Phone: What to Do if You Forget Your PIN, Pattern, or Password |

|
Regaining Access to Your Android Phone: What to Do if You Forget Your PIN, Pattern, or Password
You use your Android phone to enter your PIN, pattern, or password like normal, but it doesn't work. After a few frustrating attempts, you realize you st...
Author: James Fleming |
|
|
|
|
5
|
A Complete Guide on How to Fax a Document from Your Smartphone |

|
A Complete Guide on How to Fax a Document from Your Smartphone
A fax document is a telephonic document made of ones and zeros sent over a telephone line associated with an output device like a printer. Today, we use "fax" as a synonym for FAX (facsi...
Author: James Fleming |
|
|
|
|
6
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
7
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
8
|
Tracking a Wi-Fi Password on Your Windows PC or Android Phone |

|
We need to have internet access to our devices, mostly smartphones and computers, to enjoy using them fully. This enables you to browse freely and interact with your friends on social media worldwide. One of the best ways to access the internet is ...
Author: James Fleming |
|
|
|
|
9
|
What Are Your Strategies To Avoid Being A Victim Of Cybercrime? |

|
Cybercrimes have been on the increase, with many unaware victims. When we hear about cybercrimes, we automatically think about hackers. But cybercrime is not just about hacking. It goes beyond that. Many people today use their devices, such as phones...
Author: James Fleming |
|
|
|
|
10
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
11
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Email Setup: How Can I Use Gmail as An SMTP Server? |

|
Did you know you can use your Gmail as na SMTP server? Well, now you know. One of the little-known freebies Gmail offers is a portable SMTP server that allows users to send mail to any email address from any network. You can use Google's SMTP server...
Author: Faith Cheruiyot |
|
|
|
|
13
|
How to Configure Email Client To Send Mail Through My Own SMTP Server? |

|
SMTP is the internet standard for sending and receiving emails. Email clients use SMTP to send messages to a mail server, while email servers use it to forward messages to their recipients. You need to enter your SMTP settings to use the email from a...
Author: Faith Cheruiyot |
|
|
|
|
14
|
Email Setup: How Do I Configure My ISP's SMTP Server? |

|
ISPs represent a necessary step for any sending of messages through STMP servers. It's impossible to connect to the network without the permission of one of them hence the need for an ISP's SMTP server configuration.
There are several ways you can c...
Author: Faith Cheruiyot |
|
|
|
|
15
|
Email Setup: How To Set Up a Mail Server On Windows or Mac OS X |

|
Do you want to send and receive emails with your windows or Mac OS X and connect to it using a smartphone or PC? This guide is for you.
There are several ways you can set up a mail server on Mac OS X. For example, you can use server setting prefere...
Author: Faith Cheruiyot |
|
|
|
|
16
|
What Are The Precautions To Consider When Backing Up Your Data? |

|
Did you know that backing up your data is essential to protect yourself from losing critical files? Backing up your data means making copies of your data and storing them in a safe place.
There are many ways to back up your data, and your best metho...
Author: Faith Cheruiyot |
|
|
|
|
17
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
18
|
How Can I Hack Someone's Wireless Network? |

|
Wireless networks or Wi-Fi are usually accessible to everyone who is within the transmission radius. You can use the hotspots in public places like restaurants, airports, parks, etc. This makes them more vulnerable to cyber-attacks. In fact, cracking...
Author: Tithi Raha |
|
|
|
|
19
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
20
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
21
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
22
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
23
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
24
|
What should you do to a computer before you sell it? |

|
People sell or donate their computers every day, but most don't know what they should do to their computers before selling them. It's not always about backing up your data and selling it. There are so many factors to consider, precautions to take, an...
Author: Janet Kathalu |
|
|
|
|
25
|
How to Unlock Computer Screen Windows 10? |

|
Upon leaving your computer unattended, the windows screen automatically turns off after a while, and you would need to unlock it for further access and resume working. There are several methods to unlock Windows 10 regardless you know the passw...
Author: Tithi Raha |
|
|
|
|
26
|
Windows 10: How to login to Windows 10 without password? |

|
You won’t want to go through a password recovery process if you lose your password, which can be tiresome and hectic.
We will look at the best four poss
Use Microsoft website to set login preferences
Use advanced password managers- recommended...
Author: Fay Kokri |
|
|
|
|
27
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
28
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
29
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
30
|
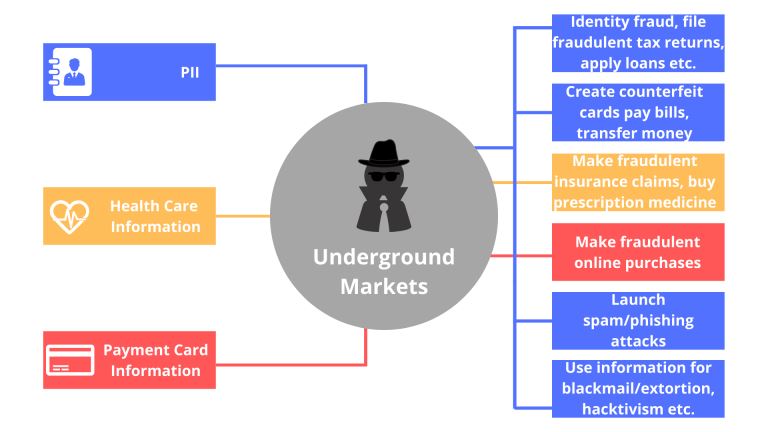
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
31
|
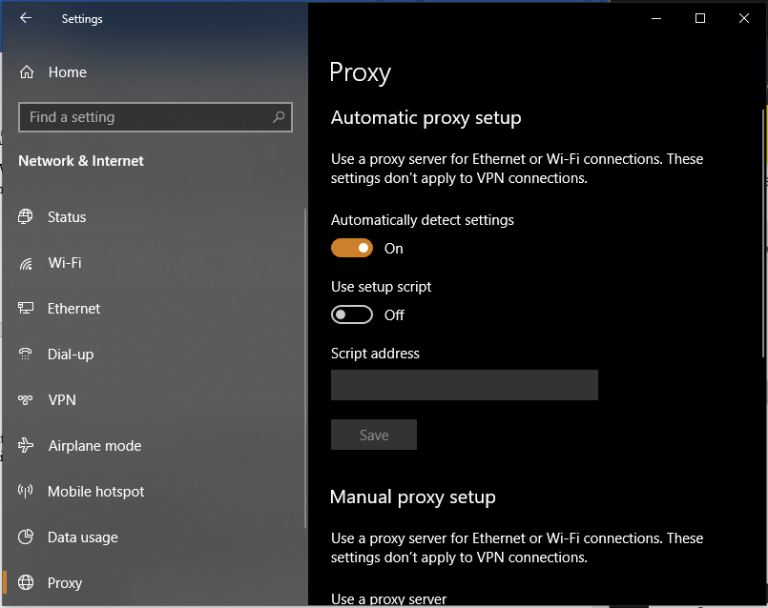
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
32
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
33
|
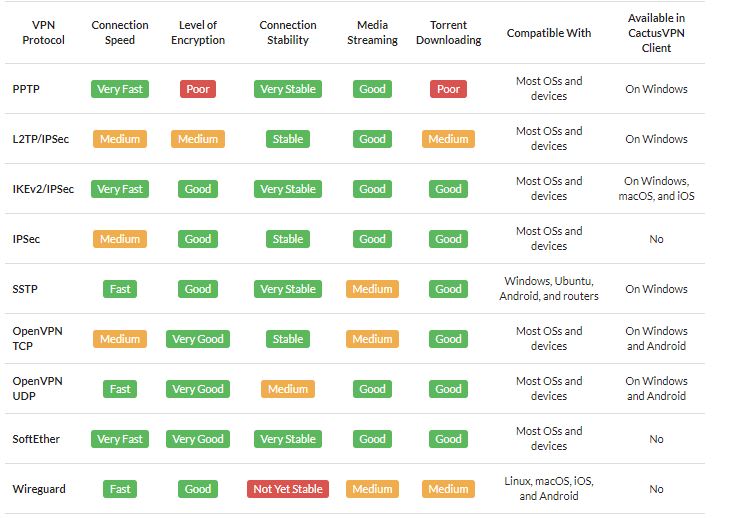
What Is a VPN? |
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|
|
34
|
Password Protecting Folders and Files |

|
If you share a computer login, it might be in your best interest to use a password to keep private files safe from prying eyes. Of course, this won't protect you from malware or online security breaches, but it is an easy way to safeguard your privat...
Author: Trey Williams |
|
|
|