|
1
|
How Does Biometrics Change the Face of Security Enhancing Security |

|
Navigating the world of security can seem like a daunting task. With new technologies like biometrics rising, feeling curious and overwhelmed is normal. This article will guide you through how does biometrics change the face of security, providing in...
Author: Newton Waweru |
|
|
|
|
2
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
3
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
4
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
5
|
The Danger of Mixing Cyberwarfare with Cyber Espionage |

|
Are you concerned about the potential hazards of combining cyber warfare and cyber espionage? You're not alone. As someone who has delved deep into this critical issue, I understand your concerns and am here to help. This article will explore the ris...
Author: Newton Waweru |
|
|
|
|
6
|
How Can an Intrusion Detection System Protect Your Company |

|
Concerned about your company's cybersecurity? An Intrusion Detection System (IDS) might be your perfect solution. I understand how critical it is to protect sensitive data, and I've delved into the topic to provide the guidance you need.
An intrusi...
Author: Newton Waweru |
|
|
|
|
7
|
How to Protect Yourself from Cyberstalking Stay Safe Online |

|
Are you concerned about cyberstalking and your online safety? You're not alone. As an individual who delved into this issue, I empathize with your worries. In this article, I'll discuss practical steps to protect yourself from cyberstalking, so you c...
Author: Newton Waweru |
|
|
|
|
8
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
9
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
10
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
11
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
12
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
13
|
Is it Cheaper to Repair or Replace a Computer |

|
It's certain that no computer will last forever. But, to yield the best benefits out of your investment, you would want to stretch the life out as long as possible. And, computer repairs can really help you stretch out the life of your devices. Yet, ...
Author: Tithi Raha |
|
|
|
|
14
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
15
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
16
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
17
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
18
|
What Are The Precautions To Consider When Backing Up Your Data? |

|
Did you know that backing up your data is essential to protect yourself from losing critical files? Backing up your data means making copies of your data and storing them in a safe place.
There are many ways to back up your data, and your best metho...
Author: Faith Cheruiyot |
|
|
|
|
19
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
20
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
21
|
Why is NETFLIX Download Slow On iPhone & Android? |

|
Netflix has been the most popular video streaming application all over the globe. Since its inception, it has grown massively and attracted millions of viewers. Not only it allows you to stream a video but also to download it. But what if the downloa...
Author: Tithi Raha |
|
|
|
|
22
|
Quick Steps on how to set Google Chrome as a Default Browser |

|
The whole process of setting Chrome as your PC's default browser varies depending on the PC operating system. So it is right for us to say that different operating systems have different ways in which you can customize your computer to achieve Chrome...
Author: James Fleming |
|
|
|
|
23
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
24
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
25
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
26
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
27
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
28
|
How to connect two Windows 10 computers wirelessly? |

|
Connecting two computers is so important to share files. If you want to share files with your colleagues or friends, you will need to connect their computers with yours.
There are several ways you can connect two windows 10 computers wirelessly, whi...
Author: Berts Njoroge |
|
|
|
|
29
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
30
|
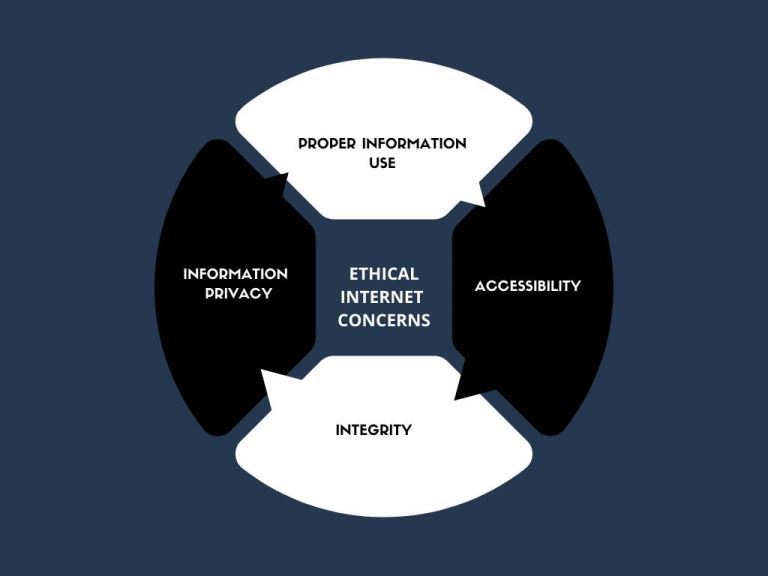
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
31
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
32
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
33
|
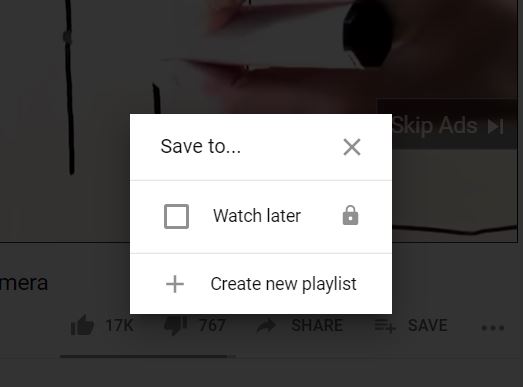
How Do I Download or Save a YouTube Video to My Computer? |
|
The YouTube design is such that users only get the chance to view the videos on their webpage. If you are the type of person who is always on the run or in situations with little or no internet connection, this might not be ideal for you. Many people...
Author: Delilah Daut |
|
|
|
|
34
|
Password Protecting Folders and Files |

|
If you share a computer login, it might be in your best interest to use a password to keep private files safe from prying eyes. Of course, this won't protect you from malware or online security breaches, but it is an easy way to safeguard your privat...
Author: Trey Williams |
|
|
|
|
35
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|