|
1
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
2
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
3
|
The Top 5 Best Drawing and Animation laptops Under 1000 Dollars |

|
The Top 5 Best Drawing and Animation laptops Under 1000 Dollars
When choosing the best drawing and animation laptop, there are crucial factors to consider for effective work results. These activities are intensive and require a computer with a quick...
Author: James Fleming |
|
|
|
|
4
|
What causes the download to be slow? The Practical Ways to Fix It |

|
Have you ever faced a scenario where you're waiting for an hour just to load your favorite movie on Netflix? If you're having a slow download speed, then it can be pretty common. People wonder about the scenario despite having a decent connection. If...
Author: Tithi Raha |
|
|
|
|
5
|
How Can I Fix a Cracked or Broken Screen On My iPad? |

|
If you're like most people, your iPad is a vital part of your life. It's probably your go-to device for checking email, browsing the web, watching videos, and more. So what do you do if your screen cracks or breaks? Don't worry - we'll show you how t...
Author: Faith Cheruiyot |
|
|
|
|
6
|
How Soon After Damage Can I Get My Iphone Fixed? |

|
iPhone users face different problems when using their phones. It forces them to take them to repair to resolve the issues. The duration taken depends on the level of damage. You must be careful when using your iPhone to prevent issues, as they can lo...
Author: Faith Cheruiyot |
|
|
|
|
7
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
8
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
9
|
How to Fix a Tablet That Won't Connect to Wi-Fi |

|
Most WI-FI connection issues result from different issues which are fixable. One must follow several steps and perform different actions to fix the issues. Troubleshooting WIFI issues are common amongst tablet users. If it's a software cause, you can...
Author: Faith Cheruiyot |
|
|
|
|
10
|
Why is My Ping So High All Of a Sudden? Check Out The Reasons! |

|
Ping latency is a crucial thing to maintain especially when it comes to gaming that requires fast responsiveness from your end. For any online gaming, you need a lower ping to better experience everything. High ping can negatively alter the gaming ex...
Author: Tithi Raha |
|
|
|
|
11
|
Will A Better Router Improve Your Ping? What Are Other Benefits? |

|
You have waited so long for your favorite game to release online and now you've downloaded it to play and suddenly you notice aggressive lagging on your PC. Isn't that annoying? In most cases, lagging while playing games occur due to a higher ping. A...
Author: Tithi Raha |
|
|
|
|
12
|
How Do You Get A Zero Ping? Check Out The Ways! |

|
A ping is referred to the total amount of time taken by your computer and server for sending out and receiving data packets. The higher the ping is, the poorer the performance gets. While a lower ping typically indicates a smooth online experience. B...
Author: Tithi Raha |
|
|
|
|
13
|
How Do You Locate Someone's IP Address? 4 Ways to Apply! |

|
An IP address is a simple numeric address used for identifying unique devices in a network. You can easily find the IP address of your own, but there are times when you may need to locate someone's IP address. Maybe you want to blacklist them or you ...
Author: Tithi Raha |
|
|
|
|
14
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
15
|
Is It Worth Repairing a Computer Monitor? |

|
When a computer monitor stops working, it can be tempting to toss it and buy a new one. But is it really worth buying a new monitor when the old one could potentially be repaired?
There are several factors to consider before repairing your computer ...
Author: Faith Cheruiyot |
|
|
|
|
16
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
17
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
18
|
Internet Connection: Why Is My Internet So Slow |

|
We all have experienced slow internet speeds in our homes. I will guide you on the best way you can speed up your home internet, how different factors affect your speeds, and getting the best internet plans for your home or office. I will also guide ...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
20
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
21
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
22
|
How Do Search Engines Work? |

|
You’re in the kitchen making your mom’s favorite pizza. To get topping ideas, you open your web browser to perform a search. You type ‘topping ideas’ in the search box, hit ‘Enter,’ and get eighty-nine million results in about half a second. For th...
Author: Ian Musyoka |
|
|
|
|
23
|
How does Chromecast work technically? |

|
Chromecast is a small disc-shaped device from Google that plugs into the High-Definition Multimedia Interface (HDMI) port of your television. It streams content through the Wi-Fi connection of your mobile device or computer, from streaming services s...
Author: Ujunwa Chibuzor |
|
|
|
|
24
|
What are the F1 through F12 keys? |

|
The F Keys have always remained a mystery to many regular computer users. The truth is, several basic computer tasks can be achieved without using these F Keys. However, for a relatively experienced or advanced computer user, these F keys become esse...
Author: Collins Okoth |
|
|
|
|
25
|
I Can't Open Email Attachments |

|
Email attachments are the files you receive alongside your email messages. The files come in different formats. The most common and widely used are the .pdf, .doc, .zip, or .html.
There are various other forms, and each requires specific computer p...
Author: Eunice Njuguna |
|
|
|
|
26
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
27
|
Computer Maintenance: How Do I Keep My Laptop Battery in Good Health? |

|
Image: A Laptop and Its Battery
The health of all batteries decreases over time with repeated charging and use, but this does not happen at the same speed. If you are given the same brand-new laptop on the exact day as someone else, the battery li...
Author: Ian Musyoka |
|
|
|
|
28
|
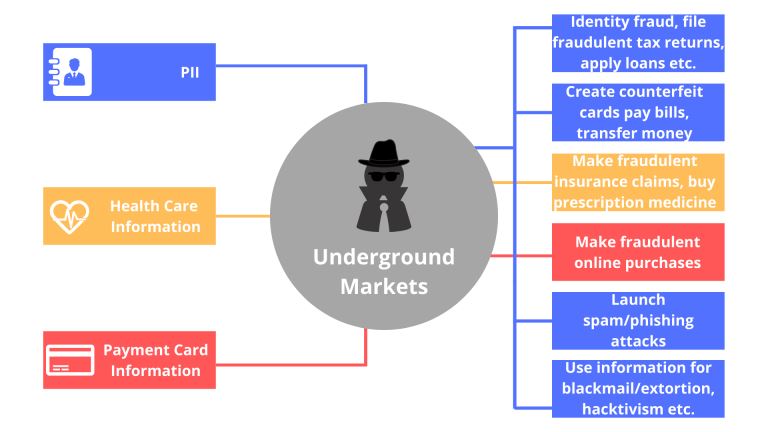
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
29
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
30
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
31
|
What Is an On-board Video Chipset |

|
A chipset refers to a complex set of components in an integrated circuit. A chipset's main purpose is to manage data flow sequentially between the processor, memory, and all other computer components. Normally, all chipsets are mounted on the motherb...
Author: Collins Okoth |
|
|
|
|
32
|
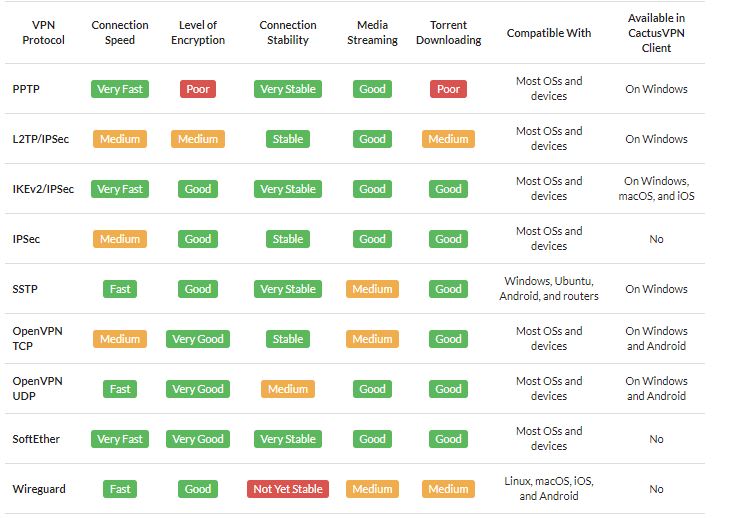
What Is a VPN? |
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|
|
33
|
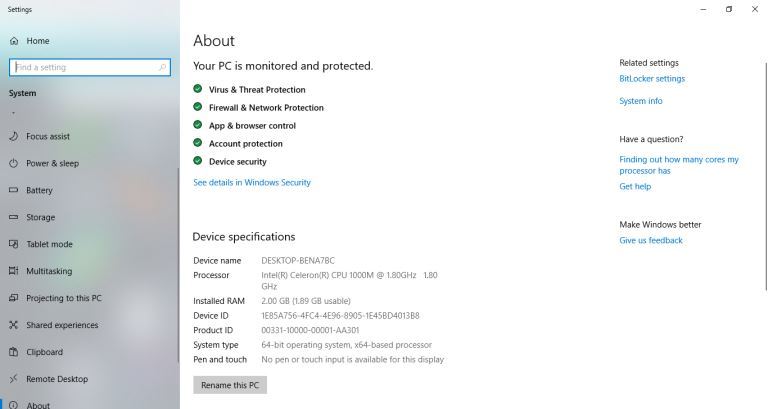
Does Adding RAM Increase Computer Speed? |
|
When purchasing a computer, one of the specifications to look out for is the amount of RAM it possesses. The system memory of your computer consists of two types of memory: virtual memory and physical memory (also called Random Access Memory). Unli...
Author: Ian Musyoka |
|
|
|
|
34
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|
|
35
|
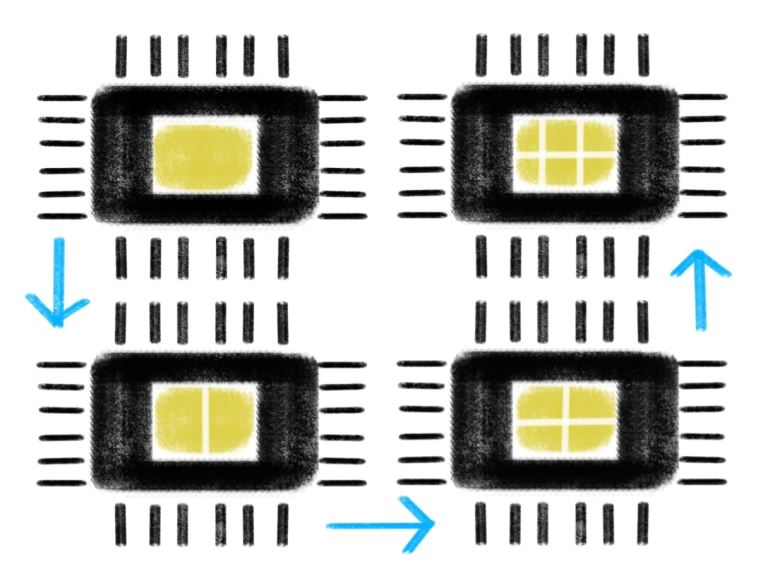
What Is a Processor Core |
|
What Is a Processor Core?
The Central Processing Unit (CPU) is considered the brain of a computer. The processor’s core is the part of the CPU that does the processing. In the days of early computing, a CPU would have been comprised of only one core...
Author: Trey Williams |
|
|
|