|
1
|
The 4 Types of Binary Codes and Their Uses Master Binary Coding |

|
This article sheds light on the 4 types of binary code and their uses. Are you seeking a comprehensive understanding of the various binary codes and their utilization in computer technology? Continue to read to find out.
In total, there are 4 types ...
Author: Newton Waweru |
|
|
|
|
2
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
3
|
Is it Cheaper to Repair or Replace a Computer |

|
It's certain that no computer will last forever. But, to yield the best benefits out of your investment, you would want to stretch the life out as long as possible. And, computer repairs can really help you stretch out the life of your devices. Yet, ...
Author: Tithi Raha |
|
|
|
|
4
|
Can Humans Read Binary Code Unlock the Secrets of Binary |

|
Have you ever wondered if humans can read binary code? If you're like many others, you may have encountered binary code in your computer science studies or even in your daily use of technology, but never quite understood how to read it. Well, you're ...
Author: Newton Waweru |
|
|
|
|
5
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
6
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
7
|
How to Become a Technician For Computer Repair in Topeka, KS? |

|
A computer technician is responsible for repairing and maintaining all the computer equipment. Further, they repair hardware, update software, and troubleshoot any computer networks if required. However, becoming a technician for Computer Repair Tope...
Author: Tithi Raha |
|
|
|
|
8
|
Characteristics of a Good Computer Repair Technician in Topeka, KS |

|
Professional technicians for Computer Repair in Topeka, Kansas are certainly responsible for maintaining, testing, and installing computer networks as well as software. However, these aren't the only skills required to succeed in this field. A techni...
Author: Tithi Raha |
|
|
|
|
9
|
Binary Code vs. Gray Code [Master the Basics] |

|
Unlock the secrets of digital coding and get ahead with my comprehensive guide to Binary Code vs. Gray Code. I understand your need for clear, concise information and are here to help. Get ready to master the basics and gain confidence in your codin...
Author: Newton Waweru |
|
|
|
|
10
|
What Is Binary Also Known As? Discover the Different Names for Binary |

|
Uncover the secret of binary and its various names. Delve into the unique labels used to describe binary thoroughly. Embark on an enlightening journey to grasp this concept effortlessly with simple yet comprehensive information. Rely on my extensive ...
Author: Newton Waweru |
|
|
|
|
11
|
How Do Computers Recognize Digital Signals? |

|
How do computers translate digital signals? Have you ever wondered how computers can understand and respond to digital signals? My comprehensive article delves deep into the technicalities and highlights the essential components that make computer re...
Author: Newton Waweru |
|
|
|
|
12
|
What Makes the Binary System Applicable to Computer Circuits? |

|
Discover the importance of the binary system in computer circuits. Are you eager to understand the inner workings of computers and the significance of the binary system?
The most important reason that makes the binary system applicable to Computer ...
Author: Newton Waweru |
|
|
|
|
13
|
Is Binary Worth Learning? Know the Benefits of Learning Binary Code |

|
Are you wondering if learning binary is worth your time and effort? Discover the benefits of binary and see how it can enhance your career opportunities.
As a whole, learning binary can bring a multitude of benefits for individuals looking to en...
Author: Newton Waweru |
|
|
|
|
14
|
Binary Code vs. Morse Code: A Head to Head Analysis |

|
Seeking to comprehend the difference between Binary Code and Morse Code? Your search ends here. In this write-up, I will delve into a side by side examination of these two codes and examine their specific features and uses.
As a whole, Binary Code a...
Author: Newton Waweru |
|
|
|
|
15
|
Why Was Binary Code Invented? Discover the History of Binary Code |

|
Discover the origin of binary code in this informative article. Have you ever wondered why binary code was invented and how it has revolutionized the way we process and store data?
As a whole, the invention of binary code was born as a solution for ...
Author: Newton Waweru |
|
|
|
|
16
|
Binary code VS ASCII [Understanding the Differences] |

|
This piece delves into the differences between binary and ASCII coding methodologies. If you're seeking information and a thorough examination of these coding techniques, your search has come to an end. I understand the confusion that comes with comp...
Author: Newton Waweru |
|
|
|
|
17
|
How To Incorporate Theater Elements for a Better Experience |

|
Did you know that theater services can help to improve your experience? There are many reasons why theater is so popular, but one of the main reasons is that it offers an immersive experience that you can rarely find anywhere else.
There are various...
Author: Faith Cheruiyot |
|
|
|
|
18
|
What Are The Basic Rules to Design a Theater? |

|
Designing a theatre comes with its own set of unique challenges and considerations. From the size and shape of the space to the type of seating, there are many factors to consider when creating a theatre.
There are some basic rules in designing a th...
Author: Faith Cheruiyot |
|
|
|
|
19
|
What Are The Principles of Theatrical Design? |

|
Do you have a performance or a drama that you would like to perform? One follows many things when preparing a stage for a performance. It is difficult as it involves different professionals performing various tasks to ensure success.
There are diffe...
Author: Faith Cheruiyot |
|
|
|
|
20
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
21
|
What Is Overclocking? Beginner's Guide to Speeding up PCs |

|
Overclocking is essentially an act of manually increasing the clock speeds of the CPU, RAM, or GPU. It is common among computer geeks, IT professionals, and heavy computer users like Gamers interested in maximizing their processor's potential. To suc...
Author: Collins Okoth |
|
|
|
|
22
|
How to Use Google Docs: The Beginner's Guide to Google Docs |

|
The old way of storing documents on a hard disk is a thing of the past. The cloud-based solution is the new way to handle files. Google Docs is one of the best ways to create, edit and share word documents. You don't have to carry storage devices to ...
Author: Faith Cheruiyot |
|
|
|
|
23
|
Internet Connection: Why Is My Internet So Slow |

|
We all have experienced slow internet speeds in our homes. I will guide you on the best way you can speed up your home internet, how different factors affect your speeds, and getting the best internet plans for your home or office. I will also guide ...
Author: Faith Cheruiyot |
|
|
|
|
24
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
25
|
How to create an invisible folder on your Windows 10 Computer |

|
How to create an invisible folder on your Windows 10 Computer
Do you have questions on how to create a hidden folder on your Windows 10 computer? Worry no more. With this informative piece, we will be sharing with you a step-by-step guide on this. F...
Author: Gloria Mutuku |
|
|
|
|
26
|
Why My Computer Shuts Down Randomly When Gaming? |

|
Computer shutting down when gaming can be caused by many several hitches. In this article, we will reasons why your computer shuts down when you are playing games, and how to fix it.
The methods, we will discuss here, can be used to fix issues in Wi...
Author: Faith Cheruiyot |
|
|
|
|
27
|
What is the Internet of Things IoT |
|
The Internet of things (IoT) is a general term for the increasing number of electronics that are not conventional computer equipment but connected to the Internet to send information, receive instructions, or both.
Tech analyst company IDC forecasts...
Author: Collins Okoth |
|
|
|
|
28
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
29
|
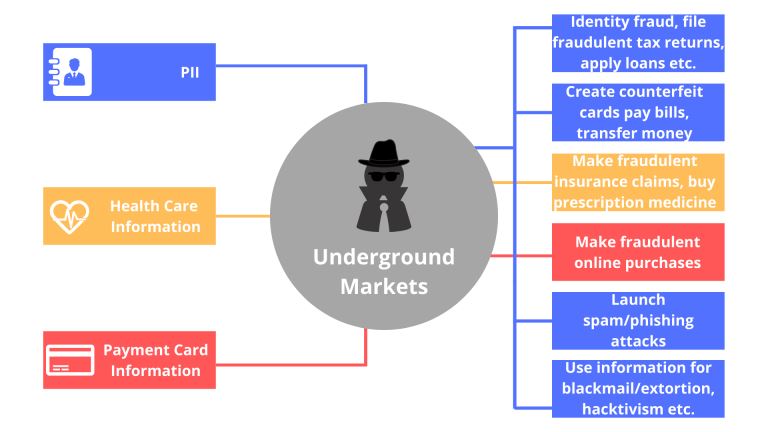
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
30
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
31
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
32
|
What is Memory in a Computer |

|
Computer memory can be defined as a physical device to store information either temporarily or permanently in a computer. Computer memory is a generic term used to describe all the different forms of technology that a computer may use. These forms of...
Author: Collins Okoth |
|
|
|
|
33
|
What Is USB 3.0 |

|
USB is short for Universal Serial Bus. A USB is a plug-and-play interface that enables a computer to interact or communicate with other devices (Peripheral devices). There exists a wide range of USB-connected devices such as mice, keyboards, flash d...
Author: Collins Okoth |
|
|
|
|
34
|
My Computer Won't Connect To the Internet but Others Will |

|
There's nothing more frustrating than when your device won't connect to the internet, and you don't know why, especially when others don't seem to have a problem! But before you give up and throw it out or spend hours on the phone with your ISP, take...
Author: Trey Williams |
|
|
|