|
1
|
Ways you Could Be Exposing Yourself to a Cybersecurity Attack |

|
Are you concerned about cybersecurity? You're not alone! As we increasingly rely on technology, protecting ourselves from cyber threats is crucial. I've researched this topic extensively, so I'm here to help. In this article, I'll explore ways you mi...
Author: Newton Waweru |
|
|
|
|
2
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
3
|
What Is Cloud Computing as a Form of Technology Today |

|
In a nutshell, this article explains how Cloud Computing Is being used Today, as well as It's benefits.
As a whole, Cloud Computing Is the ability to access Information on the Internet with ease ,via the different applications enabled by the cloud b...
Author: Rahab Nyambura |
|
|
|
|
4
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
5
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
6
|
Why Was Binary Code Invented? Discover the History of Binary Code |

|
Discover the origin of binary code in this informative article. Have you ever wondered why binary code was invented and how it has revolutionized the way we process and store data?
As a whole, the invention of binary code was born as a solution for ...
Author: Newton Waweru |
|
|
|
|
7
|
Ways To Free Up Disk Space on Your Mac Hard Drive |

|
Ways To Free Up Disk Space on Your Mac Hard Drive
Introduction
Running out of storage space on a mac is more common than most people may think. 80% of Mac users will experience these issues at one point. Therefore, to keep these problems from unnec...
Author: James Fleming |
|
|
|
|
8
|
A Complete Guide on How to Fax a Document from Your Smartphone |

|
A Complete Guide on How to Fax a Document from Your Smartphone
A fax document is a telephonic document made of ones and zeros sent over a telephone line associated with an output device like a printer. Today, we use "fax" as a synonym for FAX (facsi...
Author: James Fleming |
|
|
|
|
9
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
10
|
The Easiest Way to Copy Text Messages from One Android Device to Another |

|
The Easiest Way to Copy Text Messages from One Android Device to Another
It's natural to question whether and how text messages may be transferred from one Android smartphone to another in case of a device swap. It takes a few minutes to copy your t...
Author: James Fleming |
|
|
|
|
11
|
Copying & Pasting On a Mac Computer |

|
Any computer user needs to be able to copy and paste. Copying and pasting make it simpler to move information from one place to another, whether working on a paper or browsing the web. The procedure is significantly easier if you use a Mac. Apple c...
Author: James Fleming |
|
|
|
|
12
|
Give Your iPhone a Unique Appearance |

|
Give Your iPhone a Unique Appearance.
Have you grown tired of your iPhone's default screen? Are you trying to find ways to give it a unique appearance? The iPhone's home screen is highly adjustable, allowing you to add widgets and icons for a more p...
Author: James Fleming |
|
|
|
|
13
|
The Need For iMessages, When And How to Turn Off iMessages on Mac |
|
The Need For iMessage, When And How to Turn Off iMessage on Mac
Introduction
The need for iMessage on Mac is becoming increasingly apparent as the uses of Macs expand, and with it, so does our dependence on communication both in work and leisure. W...
Author: James Fleming |
|
|
|
|
14
|
Steps for transferring data from a hard disk drive to a solid state drive on a Windows 10 or 11 comp |
|
Steps for transferring data from a hard disk drive to a solid state drive on a Windows 10 or 11 comp
Introduction
Transferring data from a hard disk drive (HDD) to a solid-state drive (SSD) can be a great way to improve the performance of your comp...
Author: James Fleming |
|
|
|
|
15
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
16
|
What are the Data Recovery Tips & Tricks? |

|
There is a lot of evolution around data recovery, with many individuals starting data recovery businesses. We have many tricks and tips that make the whole process efficient. Data loss happens in different situations, and it can be very frustrating. ...
Author: Faith Cheruiyot |
|
|
|
|
17
|
What Are The Best Backup Services Strategies You Should Try? |

|
Are you aspiring to perform data recovery in your organization or want to hire someone? Before starting over, it is a wise idea that you understand the best backup services strategies.
There are several important backup services strategies users in ...
Author: Faith Cheruiyot |
|
|
|
|
18
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
19
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
20
|
My C Drive Is Full Without Reason, Ways to Solve It |

|
Computers store the system files within the drive C, and there are some instances when your device may give you a warning that this part of your hard drive is filled up. While it can fill up from file storage, in other cases, it could be due to other...
Author: Gloria Mutuku |
|
|
|
|
21
|
What are the backup best practices using the cloud? |

|
Have you ever imagined what you would do if you lost all your crucial data? Of course, you cant imagine. Well, there is only one way to be sure of data safety and longevity- data backup. And the best thing is; cloud backup is here to make it easy to ...
Author: Faith Cheruiyot |
|
|
|
|
22
|
What to do when CCTV cameras power supply stop working? |

|
It has been a major issue among people when it comes to how to handle CCTV cameras. The major puzzle is how to tell if the power supply is the issue and what to do, how to detect the problem, why you are getting uncolored pictures, why your footage a...
Author: Janet Kathalu |
|
|
|
|
23
|
What should you do to a computer before you sell it? |

|
People sell or donate their computers every day, but most don't know what they should do to their computers before selling them. It's not always about backing up your data and selling it. There are so many factors to consider, precautions to take, an...
Author: Janet Kathalu |
|
|
|
|
24
|
Unlock PDF: How to Remove a Password From a PDF File |

|
The greatest frustration is when you want to access or print a PDF document, only to find out it has restrictions, and you are clueless about its original password. I am about to make you rest easy and enjoy removing the permission passwords from you...
Author: Fay Kokri |
|
|
|
|
25
|
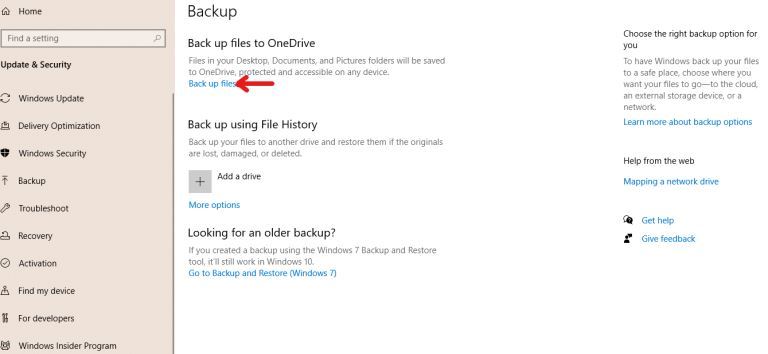
How to Backup Computer Windows 10? |
|
Backing up your computer windows 10 isn’t optional but a necessity.
The process starts by clicking on the “start” button on your Windows 10 system, navigating to the “setting” page, then to the “update & security” section, clicking on “backup,” and...
Author: Tithi Raha |
|
|
|
|
26
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
27
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
28
|
System Restore Not Working |
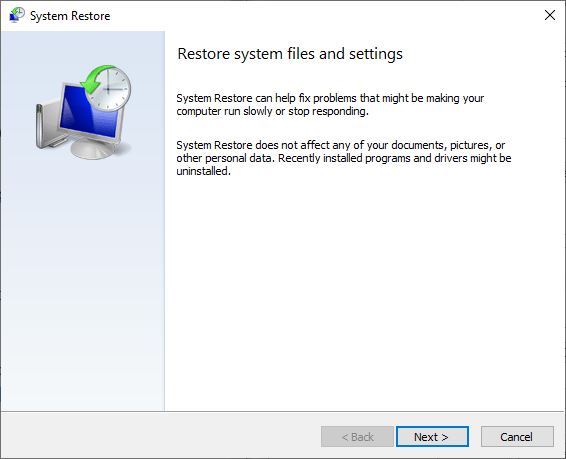
|
A newly installed update or program might cause your computer to malfunction. You have probably wondered if there is a way you can undo everything and restore previous settings. Fortunately, there is one called System Restore. It is a tool designed f...
Author: Ian Musyoka |
|
|
|
|
29
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
30
|
How Do I Destroy a Hard Drive? |

|
You can never be too careful when it comes to protecting your sensitive information, and you wouldn't be alone in thinking that just wiping a hard drive clean might not be taking things far enough. Whatever your reasons for wanting to completely dest...
Author: Trey Williams |
|
|
|