|
1
|
The 4 Types of Binary Codes and Their Uses Master Binary Coding |

|
This article sheds light on the 4 types of binary code and their uses. Are you seeking a comprehensive understanding of the various binary codes and their utilization in computer technology? Continue to read to find out.
In total, there are 4 types ...
Author: Newton Waweru |
|
|
|
|
2
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
3
|
Binary Code vs. Gray Code [Master the Basics] |

|
Unlock the secrets of digital coding and get ahead with my comprehensive guide to Binary Code vs. Gray Code. I understand your need for clear, concise information and are here to help. Get ready to master the basics and gain confidence in your codin...
Author: Newton Waweru |
|
|
|
|
4
|
What Makes the Binary System Applicable to Computer Circuits? |

|
Discover the importance of the binary system in computer circuits. Are you eager to understand the inner workings of computers and the significance of the binary system?
The most important reason that makes the binary system applicable to Computer ...
Author: Newton Waweru |
|
|
|
|
5
|
Why Do We Use Binary Digits To Represent of Electronic Signals? |

|
Discover why binary digits are crucial for representing electronic signals in our technology-driven world. Join me as I explore the science behind this fundamental concept and why it is essential for seamless communication in the digital world.
As a...
Author: Newton Waweru |
|
|
|
|
6
|
Binary Code vs. Morse Code: A Head to Head Analysis |

|
Seeking to comprehend the difference between Binary Code and Morse Code? Your search ends here. In this write-up, I will delve into a side by side examination of these two codes and examine their specific features and uses.
As a whole, Binary Code a...
Author: Newton Waweru |
|
|
|
|
7
|
Binary code VS ASCII [Understanding the Differences] |

|
This piece delves into the differences between binary and ASCII coding methodologies. If you're seeking information and a thorough examination of these coding techniques, your search has come to an end. I understand the confusion that comes with comp...
Author: Newton Waweru |
|
|
|
|
8
|
Knowing Your Android Phone Model. |

|
Knowing Your Android Phone Model.
Introduction.
A phone model is a style or design of a smartphone that producers often release in a series; examples may include the Tecno Camon 11 and Tecno Spark 7p.
Why know your phone models?
Every phone rel...
Author: James Fleming |
|
|
|
|
9
|
What Binary Code for “I Love You”? Learn To Write in Binary |

|
Saying "I love you" is a phrase that holds great significance and emotion for many people. It is a phrase that is often spoken, written, and expressed through various means. In the digital age, it is also possible to write "I love you" in binary.
As...
Author: Newton Waweru |
|
|
|
|
10
|
Which Binary Code is Most Popular? Learn about Binary Code |

|
Are you curious about the most widely utilized binary code? Your search ends here! This article delves into various binary codes and their specific applications.
The most popular binary code is the American Standard Code for Information Interchange ...
Author: Newton Waweru |
|
|
|
|
11
|
System 32 Directory and its Importance |

|
System 32 Directory and its Importance
The average device user can run into problems figuring out which files to delete and which to save. While clearing unnecessary files on the hard drive can improve the speed and performance of your system, some ...
Author: James Fleming |
|
|
|
|
12
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
13
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
14
|
What the Best Game Console Repair Pros Do (and You Should Too) |

|
Are you looking for things that game console repair experts do and wish you could? Here is a full guide to help you get more skills in the console repair industry.
As a whole, game console repair pros do things like cleaning, maintenance, and game c...
Author: Caroline Chebet |
|
|
|
|
15
|
What Terms Everyone in the Game Console Repair Industry Should Know? |

|
The terms used in gaming consoles and their repair can be intimidating, but this guide explains them in simple terms.
On average, there are hundreds of terms used in games and consoles. The common ones include baking, badge, a bonus stage, AAA, AL,...
Author: Caroline Chebet |
|
|
|
|
16
|
How to Change the Default System Font on Windows 10 |

|
To personalize your Windows PC, you can change the default Windows user interface font to the desktop element font. This font, called Segoe UI, appears in window titles, application menus, and other parts of the Windows graphical interface. I have a ...
Author: Berts Njoroge |
|
|
|
|
17
|
How do I Know if My Video Card is Failing? |

|
Graphics card failure is a common problem with computers. When a graphics card fails, your computer operations come to a stand still. I have had my own share of video card problems, from which I discovered critical information which I am glad to shar...
Author: Gloria Mutuku |
|
|
|
|
18
|
Digital Storage: How Big Are Gigabytes, Terabytes, and Petabytes? |

|
Have you come across data storage units like Petabytes, Gigabytes, and Terabytes? What do they mean in the real world of data storage? The articles will make you comprehend the complexity of units of data storage and their actual sizes. Let us see ho...
Author: Faith Cheruiyot |
|
|
|
|
19
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
20
|
How Does a Computer Work: A Definitive Guide |

|
A computer is an electronic machine that acts as an information processor. It takes the raw information or data, stores it, works on it, and spits the result out. However, there is an entire process behind how the computer works.
A computer is desi...
Author: Tithi Raha |
|
|
|
|
21
|
Why does my computer keep freezing |

|
We all have faced a situation where you are using your computer at work, office, or school, and it happens- your computer randomly freezes. Your computer becomes useless, and you lose all the information on the projects at hand. I will guide you on h...
Author: Berts Njoroge |
|
|
|
|
22
|
How computers work: why is the processor important? |

|
We have prepared this article with the sole aim of informing you what a processor is, it's components and how they function together in transforming data and instructions into useful information.
,
A CPU or processor is an electronic circuit found ...
Author: Gloria Mutuku |
|
|
|
|
23
|
Computer Repair: How to Detect Crypto Mining Malware |

|
The vast growth of the cryptocurrency market has been something to marvel at over the past few years. However, the concept of anonymous payouts has given cybercriminals a reason to be part of the game. They have developed crypto-mining malware that c...
Author: Ian Musyoka |
|
|
|
|
24
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
25
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
26
|
How do you fix a computer that won't turn on? |

|
It is annoying when your computer can’t turn on, and it’s even more hectic to know how to fix it. The first and important step is to troubleshoot. It will help you understand the problem, fix it, and go back to using your computer.
Modern compute...
Author: Berts Njoroge |
|
|
|
|
27
|
How does Chromecast work technically? |

|
Chromecast is a small disc-shaped device from Google that plugs into the High-Definition Multimedia Interface (HDMI) port of your television. It streams content through the Wi-Fi connection of your mobile device or computer, from streaming services s...
Author: Ujunwa Chibuzor |
|
|
|
|
28
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
29
|
What Are Ethical and Unethical Practices Related to Internet Use? |
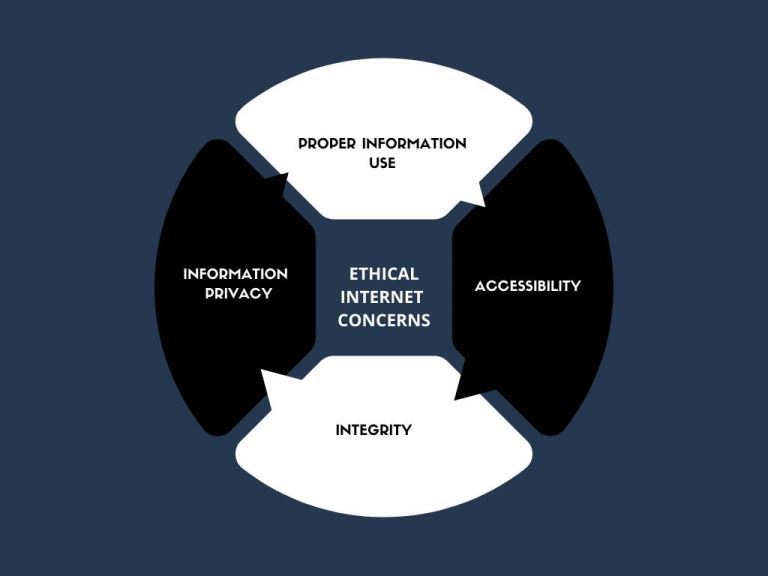
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
30
|
How to Enter the BIOS or the CMOS setup |
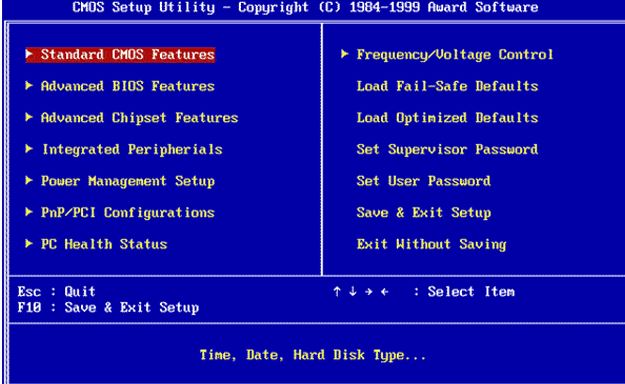
|
There is a long list of computing terms that have repeatedly confused novice computer users. Practically, the BIOS's confusion and the CMOS is one of the tops in this list. Unfortunately, I often hear people referring to the BIOS and CMOS interchange...
Author: Collins Okoth |
|
|
|
|
31
|
How Much Voltage Is Required for a Computer |
|
Have you ever wondered what really happens inside your computer power supply? A power supply is the most vital component when it comes to the operation of a computer. Without a power supply, a computer is just a random box full of metallic and plasti...
Author: Delilah Daut |
|
|
|
|
32
|
Who Invented the Computer? |

|
Who invented the computer? It doesn't seem like such a complicated question. We know who invented the steam engine, the flushing toilet, and many other things that changed the world. Why then is it so difficult to determine who invented the computer?...
Author: Trey Williams |
|
|
|
|
33
|
What Is Processor Virtualization Technology? |

|
In computing, many things can be made virtual, and there are various types of virtualization: network, desktop, and application virtualization. There are some challenges involved in the virtualization of modern processors (i.e., those built on x86 ar...
Author: Trey Williams |
|
|
|
|
34
|
What Is a Computer Processor Thread |
|
The brief answer to this question is that, in computer processing, a thread is a short sequence of programmed instructions or code.
But that’s not very helpful all by itself.
So, to properly understand what a computer processor thread is and what ...
Author: Trey Williams |
|
|
|