|
1
|
Is it Cheaper to Repair a TV or Replace it |

|
At some point in life, you must think about repairing or replacing your TV. This may be due to the common wear and tear in TVs or a breakdown. Whatever the case, the cost and extent of damage should determine whether you repair or purchase another TV...
Author: Eunice Njuguna |
|
|
|
|
2
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
3
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
4
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
5
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
6
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
7
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
8
|
How to Create Resume for Computer Repair Technician in Topeka, KS |

|
Computer repair technicians in Topeka, Kansas, are deemed responsible not only for repairing computer networks and systems but also maintaining them to avoid possible errors in the future. Although a lot of you may want to be a repair technician, you...
Author: Tithi Raha |
|
|
|
|
9
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
10
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
11
|
Tracking a Wi-Fi Password on Your Windows PC or Android Phone |

|
We need to have internet access to our devices, mostly smartphones and computers, to enjoy using them fully. This enables you to browse freely and interact with your friends on social media worldwide. One of the best ways to access the internet is ...
Author: James Fleming |
|
|
|
|
12
|
How Can I Access My Router Setting & Optimize It? |

|
Sometimes you need to know how to access the router's settings in order to have full advantage of some of the most advanced features of your high-end router. Because you might not be aware of these many features without accessing the settings page of...
Author: Tithi Raha |
|
|
|
|
13
|
Can Downloading & Playing Games Slow Down My Internet? |

|
As your bandwidth limit gets shared while downloading large-sized files like your favorite games, it may slow down your internet speed. But, the most annoying thing that you may face is being defeated at the hands of a disrupting connection while pla...
Author: Tithi Raha |
|
|
|
|
14
|
How Do You Identify The Cause And Fix Slow Download Speeds? |

|
A slow internet connection not only leaves everyone frustrated but also interrupts your work. Since there are so many problems that can cause the slowdown, it becomes difficult to identify the root cause of this disruption. However, you must find out...
Author: Tithi Raha |
|
|
|
|
15
|
Is Download Slower Than Upload? Why & How to Fix it? |

|
In today's age, it's inevitable to have a good internet connection not only for gamers but also for ordinary people. So, you opt for a suitable plan from your internet service provider, each offering a variety of upload and download speeds. But, your...
Author: Tithi Raha |
|
|
|
|
16
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
17
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
18
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Email Setup: How To Set Up a Mail Server On Windows or Mac OS X |

|
Do you want to send and receive emails with your windows or Mac OS X and connect to it using a smartphone or PC? This guide is for you.
There are several ways you can set up a mail server on Mac OS X. For example, you can use server setting prefere...
Author: Faith Cheruiyot |
|
|
|
|
20
|
What Are The Modern Rules of In-home Computer Service? |

|
In the olden days, if your computer crashed or stopped working, you had to take it in for servicing. But now, with so many people working remotely and relying on their computers, there are new rules for when and how you should get your computer servi...
Author: Faith Cheruiyot |
|
|
|
|
21
|
Is My IP Public? How to Find Your Public IP? |

|
All IP addresses can be divided into two groups—first, an external or public IP address is used on the Wide Area Network or WAN. Second is a local or private address used in the LAN or Local Area Network. A lot of people wonder whether their ISP has ...
Author: Tithi Raha |
|
|
|
|
22
|
How Can I Hack Someone's Wireless Network? |

|
Wireless networks or Wi-Fi are usually accessible to everyone who is within the transmission radius. You can use the hotspots in public places like restaurants, airports, parks, etc. This makes them more vulnerable to cyber-attacks. In fact, cracking...
Author: Tithi Raha |
|
|
|
|
23
|
Can You Log Into a WI-FI Network That Does Not Have Internet Access? |

|
Imagine you're working on an important project online that has a strict deadline, and all of a sudden, your internet connection goes off!! How would you feel? Well, we know, it can be one of the most frustrating things to deal with. But, the truth is...
Author: Tithi Raha |
|
|
|
|
24
|
What Are The Numbing Facts About TV Repair |

|
TV Repairs have become common, and so have TV issues; there are numbing TV repairs facts everyone should know about; some will shock you because you will find out that you knew nothing about TV repair. And because we want you to have all the necessar...
Author: Nancy Museo |
|
|
|
|
25
|
How to Hard Refresh Your Web Browser (to Bypass Your Cache) |

|
How to Hard Refresh Your Web Browser (to Bypass Your Cache) is a wide topic. You must have come across a person who requests you to consider clearing the browser cache. If this is the case, you need this specific diagnostic, especially in the case w...
Author: James Fleming |
|
|
|
|
26
|
What to Do When You Forget Your Wi-Fi Password |

|
Forgetting WiFi passwords is common. However, tracing them is one hard task. I have detailed proven methods that will work on your device to view the WiFi passwords you forgot. Go through each one of them to see the one will give you the best results...
Author: Berts Njoroge |
|
|
|
|
27
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
28
|
Windows 10: How to login to Windows 10 without password? |

|
You won’t want to go through a password recovery process if you lose your password, which can be tiresome and hectic.
We will look at the best four poss
Use Microsoft website to set login preferences
Use advanced password managers- recommended...
Author: Fay Kokri |
|
|
|
|
29
|
How to Change your Wi-Fi Password |
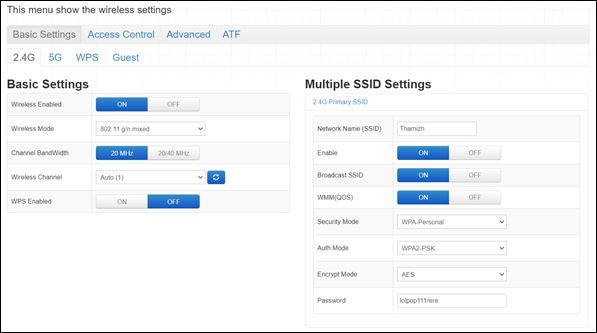
|
Abstract: Log into your router's web interface using your IP address in the address bar of your preferred browser. Once inside, access the "wireless" tab (or a tab of a similar name) and navigate the options to locate the Wi-Fi settings. Once there, ...
Author: Charz |
|
|
|
|
30
|
Do I Really Need To Care About My Privacy Online? |
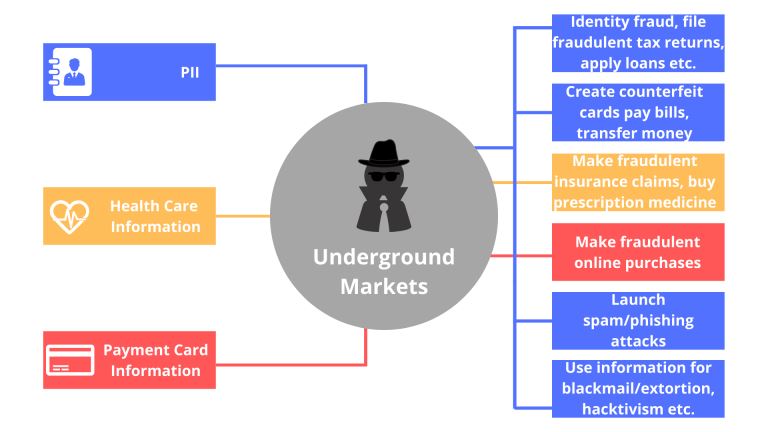
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
31
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
32
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
33
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
34
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|
|
35
|
Password Protecting Folders and Files |

|
If you share a computer login, it might be in your best interest to use a password to keep private files safe from prying eyes. Of course, this won't protect you from malware or online security breaches, but it is an easy way to safeguard your privat...
Author: Trey Williams |
|
|
|