|
1
|
The 4 Types of Binary Codes and Their Uses Master Binary Coding |

|
This article sheds light on the 4 types of binary code and their uses. Are you seeking a comprehensive understanding of the various binary codes and their utilization in computer technology? Continue to read to find out.
In total, there are 4 types ...
Author: Newton Waweru |
|
|
|
|
2
|
Why Should You Hire a Qualified Computer Repair Technician |

|
When you run into an issue with your computer system, it's of utmost importance that you avoid the temptation of handling the situation all by yourself, especially without technical knowledge and education. Also, you should avoid handing over the iss...
Author: Tithi Raha |
|
|
|
|
3
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
4
|
What is The Difference Between Computer Repair Technicians & Help Desk |

|
When it comes to the help desk analyst and computer repair Topeka, KS technician, people often need clarification on these two. Regardless of how similar these two sound, they have significant differences. However, both of them are designed to help c...
Author: Tithi Raha |
|
|
|
|
5
|
Binary Code vs. Gray Code [Master the Basics] |

|
Unlock the secrets of digital coding and get ahead with my comprehensive guide to Binary Code vs. Gray Code. I understand your need for clear, concise information and are here to help. Get ready to master the basics and gain confidence in your codin...
Author: Newton Waweru |
|
|
|
|
6
|
Binary Code vs. Morse Code: A Head to Head Analysis |

|
Seeking to comprehend the difference between Binary Code and Morse Code? Your search ends here. In this write-up, I will delve into a side by side examination of these two codes and examine their specific features and uses.
As a whole, Binary Code a...
Author: Newton Waweru |
|
|
|
|
7
|
Binary code VS ASCII [Understanding the Differences] |

|
This piece delves into the differences between binary and ASCII coding methodologies. If you're seeking information and a thorough examination of these coding techniques, your search has come to an end. I understand the confusion that comes with comp...
Author: Newton Waweru |
|
|
|
|
8
|
Knowing Your Android Phone Model. |

|
Knowing Your Android Phone Model.
Introduction.
A phone model is a style or design of a smartphone that producers often release in a series; examples may include the Tecno Camon 11 and Tecno Spark 7p.
Why know your phone models?
Every phone rel...
Author: James Fleming |
|
|
|
|
9
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
10
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
11
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Why Does My Download Slow on Xbox & How Do You Fix It? |

|
Are you waiting for hours just to finish a game download on your Xbox? Well, you're not the only one suffering from slow download speeds. There are thousands of people facing the same issue and there are countless reasons behind this. So, is there an...
Author: Tithi Raha |
|
|
|
|
13
|
How To Turn off Touch Screen Vibration on Android |

|
You are in the right place to learn how to turn off touch screen vibration on Android. Imagine our phone vibrating anytime you interact with it. It's a nuisance, right? This is something that you would love to do away with. However, there are ways to...
Author: Berts Njoroge |
|
|
|
|
14
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
15
|
What are the 5 Computer Problems and Their Solution? |

|
Are you experiencing a problem with your computer? Has your computer ever stopped operating abruptly? Fortunately, these issues may only require simple solutions to fix. You do not need an IT expert or engineer to solve them. Try some quick fixes to ...
Author: Faith Cheruiyot |
|
|
|
|
16
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
17
|
What are the essential Android repair Smartphone Apps |

|
Many people don't know the essential android repair apps to download on their android phones or their functions. If you are reading this article now, it means you are looking for answers, and I encourage you to keep on reading as this is one of our b...
Author: Nancy Museo |
|
|
|
|
18
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
19
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
20
|
I can’t see my wireless network in the list? |

|
It’s frustrating when you can’t find your Wi-Fi network in the list. There are several reasons why you can’t see your wireless network, which we will help you fix.
Why Is My WIFI Not Showing Up on My Laptop?
In general terms, these are the reason...
Author: Berts Njoroge |
|
|
|
|
21
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
22
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
23
|
What is the Internet of Things IoT |
|
The Internet of things (IoT) is a general term for the increasing number of electronics that are not conventional computer equipment but connected to the Internet to send information, receive instructions, or both.
Tech analyst company IDC forecasts...
Author: Collins Okoth |
|
|
|
|
24
|
A Detailed Guide to Removing Ransomware in Windows 10 |
|
One of the main problems faced by internet companies today is Ransomware. For this reason, cybersecurity has continued to grow as an industry in general. Unfortunately, players on both sides can easily be described as the bad guys and the good guys. ...
Author: Collins Okoth |
|
|
|
|
25
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
26
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
27
|
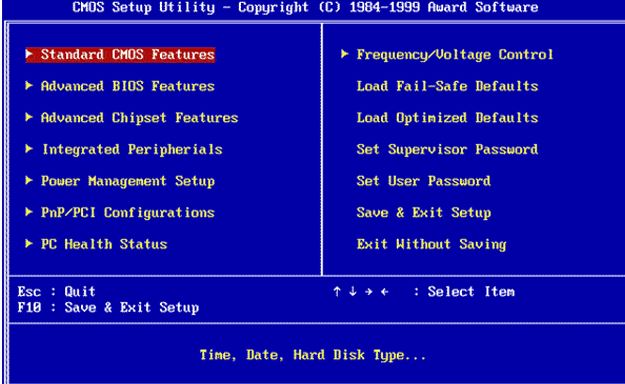
How to Enter the BIOS or the CMOS setup |
|
There is a long list of computing terms that have repeatedly confused novice computer users. Practically, the BIOS's confusion and the CMOS is one of the tops in this list. Unfortunately, I often hear people referring to the BIOS and CMOS interchange...
Author: Collins Okoth |
|
|
|
|
28
|
How do Wi-Fi Hotspots Work |

|
A hotspot can be described as a locale or area that has an accessible wireless network. Wi-Fi hotspot is commonly used to refer to the available wireless connections in public places such as airports, restaurants, and coffee shops. Depending on your ...
Author: Collins Okoth |
|
|
|
|
29
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
30
|
How to Get Rid of Computer Pop-Ups |

|
If you have had the chance to encounter pop-ups when working with your computer, you understand how frustrating and irritating it can get. They will slow down your device and even create a gateway for other malware to infect your computer. No compute...
Author: Cate Greff |
|
|
|
|
31
|
How Much Voltage Is Required for a Computer |
|
Have you ever wondered what really happens inside your computer power supply? A power supply is the most vital component when it comes to the operation of a computer. Without a power supply, a computer is just a random box full of metallic and plasti...
Author: Delilah Daut |
|
|
|
|
32
|
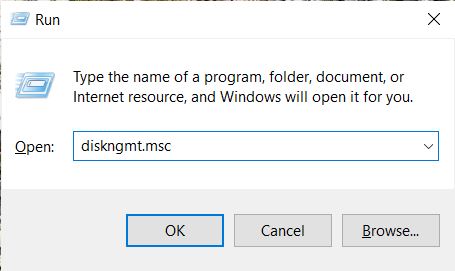
My Computer Can't Find the Hard Drive |
|
A common problem that occurs when operating a computer is the system not detecting a hard drive. It is a common occurrence related to the device not locating the default drive it uses to load in a new, old, internal, or external hard drive. For each ...
Author: Eunice Njuguna |
|
|
|
|
33
|
What Is SATA 6GB/s |

|
The abbreviation SATA stands for Serial ATA (Advanced Technology Attachment), a modern generation drive interface preceded by the traditional wide and inconvenient Parallel ATA or PATA, also known as IDE. These technologies, PATA and SATA, describe t...
Author: Collins Okoth |
|
|
|
|
34
|
How Do Computer Hard Drive Works |

|
A reliable and high-performance hard drive is essential. How? It acts as storage for your documents, videos, music, and more. Not only that. It also allows you to run your operating system, games, and other applications fast.
What you need to know i...
Author: James Fleming |
|
|
|
|
35
|
How to Update Graphics Drivers on Windows 10 |

|
In today’s world, computers have become an essential part of our lives. From work to leisure, the relevance of computers in our lives cannot be negated. This, therefore, necessitates the need to take excellent care of these devices. When it comes to ...
Author: Gloria Mutuku |
|
|
|