|
1
|
What is The Difference Between Computer Repair Technicians & Help Desk |

|
When it comes to the help desk analyst and computer repair Topeka, KS technician, people often need clarification on these two. Regardless of how similar these two sound, they have significant differences. However, both of them are designed to help c...
Author: Tithi Raha |
|
|
|
|
2
|
Will Downloading Slow Down My Internet? How to Fix it? |

|
Your internet speed may slow down when one user on your Wi-Fi connection is downloading large-sized files or downloading multiple files at the same time. The same thing will happen when you upload large files as well. So, you may notice a connection ...
Author: Tithi Raha |
|
|
|
|
3
|
What causes the download to be slow? The Practical Ways to Fix It |

|
Have you ever faced a scenario where you're waiting for an hour just to load your favorite movie on Netflix? If you're having a slow download speed, then it can be pretty common. People wonder about the scenario despite having a decent connection. If...
Author: Tithi Raha |
|
|
|
|
4
|
Why is My Download Time So Slow: Here is A Comprehensive Guide For You |

|
Daily computer usage certainly involves downloading files in some way or the other. A download simply means your computer is receiving data which can be in many forms. You could be watching a video, opening an article in a browser, reading an email, ...
Author: Tithi Raha |
|
|
|
|
5
|
How Can I Fix a Cracked or Broken Screen On My iPad? |

|
If you're like most people, your iPad is a vital part of your life. It's probably your go-to device for checking email, browsing the web, watching videos, and more. So what do you do if your screen cracks or breaks? Don't worry - we'll show you how t...
Author: Faith Cheruiyot |
|
|
|
|
6
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
7
|
What Are The Modern Rules of Backup Services? |

|
Did you know there are modern rules for backup services? Backing up data is vital to maintain computer function and avoid data loss.
There are many rules in the backup services, including always backing up your data, automating your backups, and con...
Author: Faith Cheruiyot |
|
|
|
|
8
|
10 Undeniable Benefits of Remote Assistance |

|
Advancements in technology have led to several changes in how we live and work. One of the most significant changes has been the rise of remote working. With the ability to connect to the internet from anywhere in the world, more and more people are ...
Author: Faith Cheruiyot |
|
|
|
|
9
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
10
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
11
|
What is the Best Software for Making Video Tutorials? |

|
Are you planning to make video tutorials? Do you want to explain how your products and services function using the software? Video Tutorial software is ideal as it lets you edit, generate, manipulate and enhance videos. Such ensures the corporate and...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Will A Better Router Improve Your Ping? What Are Other Benefits? |

|
You have waited so long for your favorite game to release online and now you've downloaded it to play and suddenly you notice aggressive lagging on your PC. Isn't that annoying? In most cases, lagging while playing games occur due to a higher ping. A...
Author: Tithi Raha |
|
|
|
|
13
|
How Do You Locate Someone's IP Address? 4 Ways to Apply! |

|
An IP address is a simple numeric address used for identifying unique devices in a network. You can easily find the IP address of your own, but there are times when you may need to locate someone's IP address. Maybe you want to blacklist them or you ...
Author: Tithi Raha |
|
|
|
|
14
|
How To Turn off Touch Screen Vibration on Android |

|
You are in the right place to learn how to turn off touch screen vibration on Android. Imagine our phone vibrating anytime you interact with it. It's a nuisance, right? This is something that you would love to do away with. However, there are ways to...
Author: Berts Njoroge |
|
|
|
|
15
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
16
|
Is It Worth Repairing a Computer Monitor? |

|
When a computer monitor stops working, it can be tempting to toss it and buy a new one. But is it really worth buying a new monitor when the old one could potentially be repaired?
There are several factors to consider before repairing your computer ...
Author: Faith Cheruiyot |
|
|
|
|
17
|
What Are The Best Ways To Organize files on a New Computer? |

|
Did you just buy a computer and wonder how to organize your files? While it's not the most glamorous activity, organizing computer files is essential. They often build up without your knowledge until, one day, you turn on your computer to find a des...
Author: Caroline Chebet |
|
|
|
|
18
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
19
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
20
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
21
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
22
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
23
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
24
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
25
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
26
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
27
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
28
|
What Are the Signs a Website Has Been Hacked? |
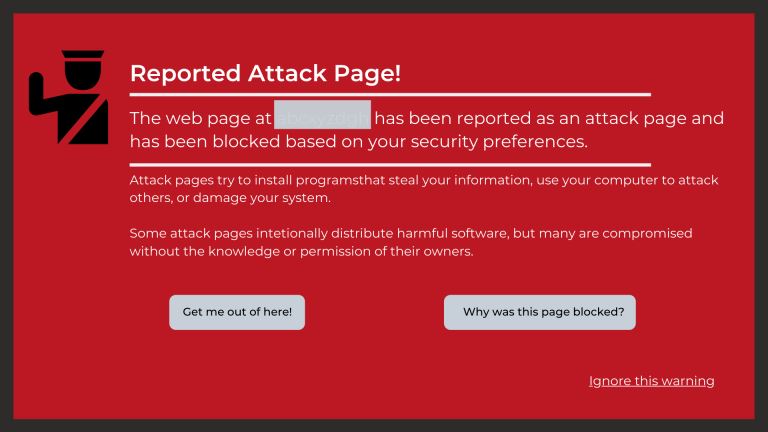
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
29
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
30
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
31
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|
|
32
|
Does Adding RAM Increase Computer Speed? |
|
When purchasing a computer, one of the specifications to look out for is the amount of RAM it possesses. The system memory of your computer consists of two types of memory: virtual memory and physical memory (also called Random Access Memory). Unli...
Author: Ian Musyoka |
|
|
|
|
33
|
How Do You Take A Screenshot in Windows 10 |
|
A screenshot is a snapshot image of whatever is visible on your screen at a given moment. It’s great for sharing real-time information with technical support or saving information on the web that might be subject to change in the future.
Taking scre...
Author: Trey Williams |
|
|
|
|
34
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|