|
1
|
What is The Difference Between Computer Repair Technicians & Help Desk |

|
When it comes to the help desk analyst and computer repair Topeka, KS technician, people often need clarification on these two. Regardless of how similar these two sound, they have significant differences. However, both of them are designed to help c...
Author: Tithi Raha |
|
|
|
|
2
|
What causes the download to be slow? The Practical Ways to Fix It |

|
Have you ever faced a scenario where you're waiting for an hour just to load your favorite movie on Netflix? If you're having a slow download speed, then it can be pretty common. People wonder about the scenario despite having a decent connection. If...
Author: Tithi Raha |
|
|
|
|
3
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
4
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
5
|
What is the Best Software for Making Video Tutorials? |

|
Are you planning to make video tutorials? Do you want to explain how your products and services function using the software? Video Tutorial software is ideal as it lets you edit, generate, manipulate and enhance videos. Such ensures the corporate and...
Author: Faith Cheruiyot |
|
|
|
|
6
|
Will A Better Router Improve Your Ping? What Are Other Benefits? |

|
You have waited so long for your favorite game to release online and now you've downloaded it to play and suddenly you notice aggressive lagging on your PC. Isn't that annoying? In most cases, lagging while playing games occur due to a higher ping. A...
Author: Tithi Raha |
|
|
|
|
7
|
How To Turn off Touch Screen Vibration on Android |

|
You are in the right place to learn how to turn off touch screen vibration on Android. Imagine our phone vibrating anytime you interact with it. It's a nuisance, right? This is something that you would love to do away with. However, there are ways to...
Author: Berts Njoroge |
|
|
|
|
8
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
9
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
10
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
11
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
12
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
13
|
What Does Airplane Mode Do, and Is It Really Necessary? |

|
If you own a mobile phone or tablet, you are already familiar with the airplane mode feature. You are probably wondering what it is and if it is essential. This article will inform you all you need to know about airplane mode, why it is necessary to ...
Author: Gloria Mutuku |
|
|
|
|
14
|
How to Use Google Docs: The Beginner's Guide to Google Docs |

|
The old way of storing documents on a hard disk is a thing of the past. The cloud-based solution is the new way to handle files. Google Docs is one of the best ways to create, edit and share word documents. You don't have to carry storage devices to ...
Author: Faith Cheruiyot |
|
|
|
|
15
|
How do I automatically print an email attachment? |

|
In the modern world, getting a reliable automated solution makes work easier and speeds up your workflow.
Have you been wondering how to print your email attachments automatically? In this article, we will guide you through several ways you can achi...
Author: Faith Cheruiyot |
|
|
|
|
16
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
17
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
18
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
19
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
20
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
21
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
22
|
Do I need a Desktop PC or a Laptop? |

|
So you are in the market for a computer system, and can't seem to decide if a Desktop PC or a Laptop will serve you better. The computer you need is the one that best meets your particular needs. Get a Laptop if you value portability above all. But i...
Author: Ujunwa Chibuzor |
|
|
|
|
23
|
What are the F1 through F12 keys? |

|
The F Keys have always remained a mystery to many regular computer users. The truth is, several basic computer tasks can be achieved without using these F Keys. However, for a relatively experienced or advanced computer user, these F keys become esse...
Author: Collins Okoth |
|
|
|
|
24
|
I Can't Open Email Attachments |

|
Email attachments are the files you receive alongside your email messages. The files come in different formats. The most common and widely used are the .pdf, .doc, .zip, or .html.
There are various other forms, and each requires specific computer p...
Author: Eunice Njuguna |
|
|
|
|
25
|
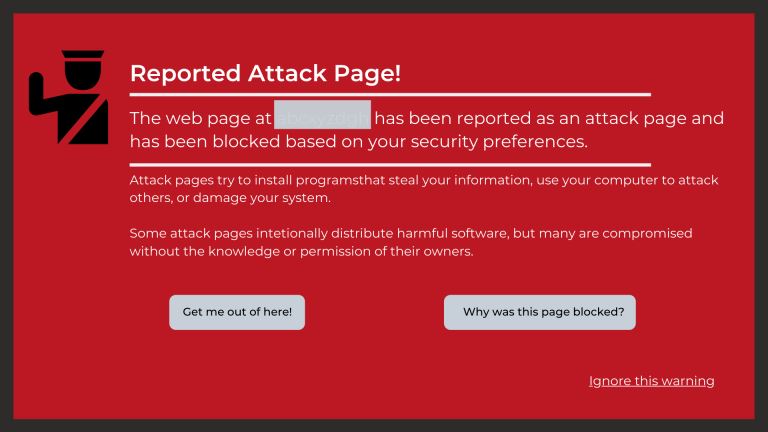
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
26
|
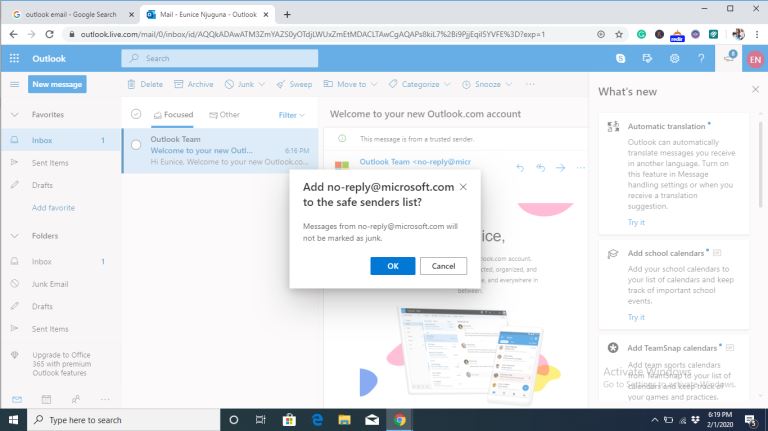
How Do I Stop Emails Going to Spam Folder |
|
Gmail, Yahoo, Hotmail, AOL, and Outlook are all excellent email services. They offer efficient email services by ensuring the proper delivery of emails to the inbox folder. But even with the efficiency in their services, there are negative issues tha...
Author: Eunice Njuguna |
|
|
|
|
27
|
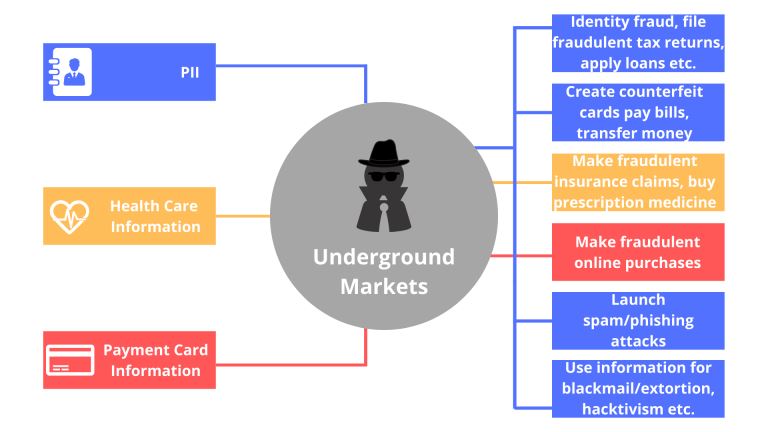
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
28
|
My Computer is Running Slow, What Steps Can I Take to Fix It? |
|
Using a slow computer can make the simplest of jobs feel very irritating and cumbersome. Your files take forever to launch, your browser keeps hanging, words you type do not show up on time, and you keep getting the ‘Not Responding’ error message whe...
Author: Ian Musyoka |
|
|
|
|
29
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
30
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
31
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
32
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|
|
33
|
How To Wipe a Computer Hard Drive |

|
How safe would you feel to discover your bank account info, old emails, and browser history are accessible to someone else? Of course, it could be the recent buyer of your computer, but still, personal information is not safe unless you or someone yo...
Author: Eunice Njuguna |
|
|
|
|
34
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|