|
1
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
2
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
3
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
4
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
5
|
Where Is Binary Code Used? Exploring Binary Code |

|
Many individuals ponder the utilization of binary in everyday life, and it is a common inquiry. I have conducted research and obtained knowledge on the diverse applications of binary, and I am happy to share my understanding and provide useful inform...
Author: Newton Waweru |
|
|
|
|
6
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
7
|
The Need For iMessages, When And How to Turn Off iMessages on Mac |
|
The Need For iMessage, When And How to Turn Off iMessage on Mac
Introduction
The need for iMessage on Mac is becoming increasingly apparent as the uses of Macs expand, and with it, so does our dependence on communication both in work and leisure. W...
Author: James Fleming |
|
|
|
|
8
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
9
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
10
|
How to Configure Email Client To Send Mail Through My Own SMTP Server? |

|
SMTP is the internet standard for sending and receiving emails. Email clients use SMTP to send messages to a mail server, while email servers use it to forward messages to their recipients. You need to enter your SMTP settings to use the email from a...
Author: Faith Cheruiyot |
|
|
|
|
11
|
Email Setup: How To Set Up a Mail Server On Windows or Mac OS X |

|
Do you want to send and receive emails with your windows or Mac OS X and connect to it using a smartphone or PC? This guide is for you.
There are several ways you can set up a mail server on Mac OS X. For example, you can use server setting prefere...
Author: Faith Cheruiyot |
|
|
|
|
12
|
What Are The Precautions To Consider When Backing Up Your Data? |

|
Did you know that backing up your data is essential to protect yourself from losing critical files? Backing up your data means making copies of your data and storing them in a safe place.
There are many ways to back up your data, and your best metho...
Author: Faith Cheruiyot |
|
|
|
|
13
|
What Are The Modern Rules of Backup Services? |

|
Did you know there are modern rules for backup services? Backing up data is vital to maintain computer function and avoid data loss.
There are many rules in the backup services, including always backing up your data, automating your backups, and con...
Author: Faith Cheruiyot |
|
|
|
|
14
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
15
|
Why Is My Internet So Slow At Night & How To Improve It? |

|
Nothing could be more annoying than coming home to continue your online activity, only to find out that your speed is lagging. If you notice, you'll see that mostly this lag happens at night. As everyone starts to use the internet, it leads to networ...
Author: Tithi Raha |
|
|
|
|
16
|
What is Internet Protocol Address 192.168.1.1 For? |

|
IP 192.168.1.1 or 10.10.0.1 or 172.168.0.1 or whatever is an address that recognizes your unique device connected to a computer network. Basically, there are hundreds of devices connected to a computer network whether it's a local area network or a w...
Author: Tithi Raha |
|
|
|
|
17
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
18
|
How to setup virtual machine on Windows 11 and Windows 10 |

|
Did you know you have access to two operating systems on one computer? It is possible to install Windows 11 on your Windows 10 PC, even if your computer doesn't meet the requirement. Well, I have compiled the best guide to set up a virtual machine (V...
Author: Berts Njoroge |
|
|
|
|
19
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
20
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
21
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
22
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
23
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
24
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
25
|
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
26
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
27
|
How do Wi-Fi Hotspots Work |

|
A hotspot can be described as a locale or area that has an accessible wireless network. Wi-Fi hotspot is commonly used to refer to the available wireless connections in public places such as airports, restaurants, and coffee shops. Depending on your ...
Author: Collins Okoth |
|
|
|
|
28
|
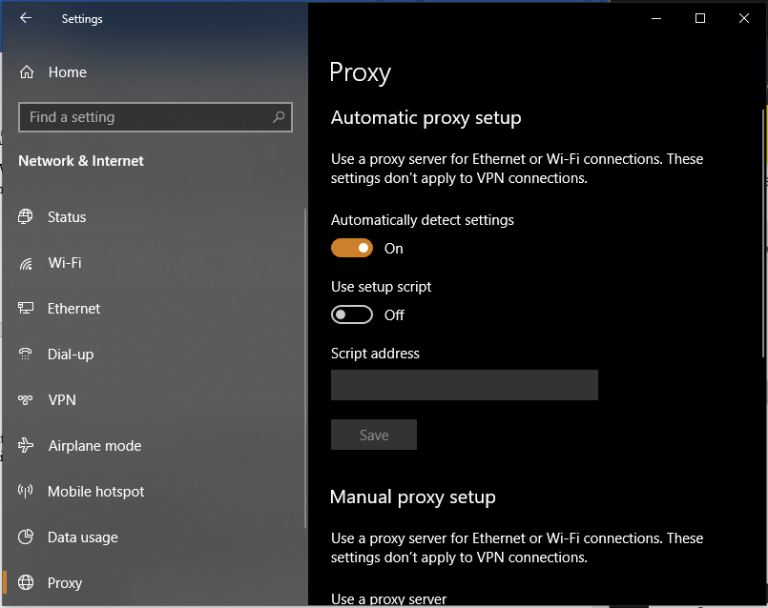
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
29
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
30
|
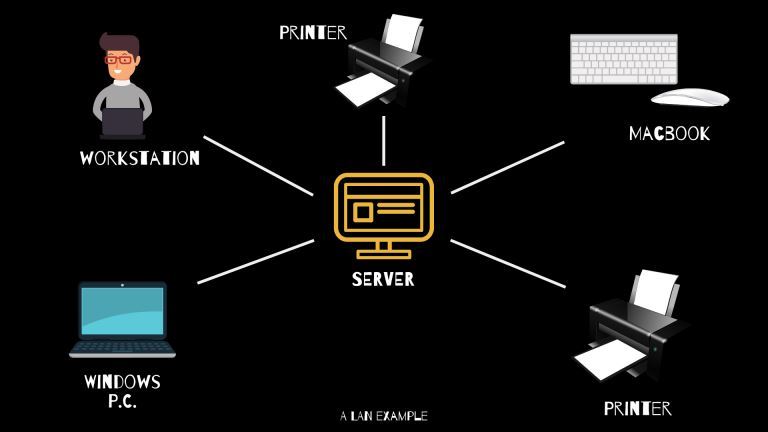
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
31
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
32
|
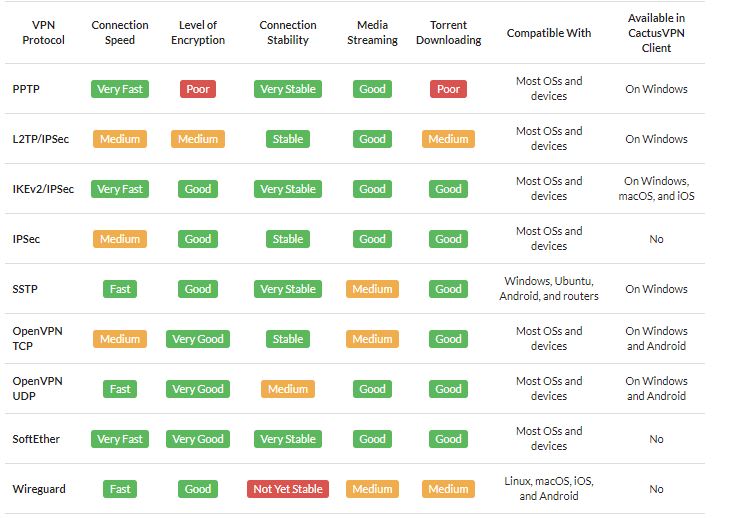
What Is a VPN? |
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|
|
33
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|
|
34
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|
|
35
|
Password Protecting Folders and Files |

|
If you share a computer login, it might be in your best interest to use a password to keep private files safe from prying eyes. Of course, this won't protect you from malware or online security breaches, but it is an easy way to safeguard your privat...
Author: Trey Williams |
|
|
|