|
1
|
How Does Malware Work Malware Definition Types and Protection |

|
I understand how troubling it can be to deal with the mysteries of cyber threats like malware. Fear not, as I've delved into the subject to help simplify it for you. In this article, we'll untangle the intricacies of malware, how it works, and its im...
Author: Newton Waweru |
|
|
|
|
2
|
What are the 3 Main Pillars of Cybersecurity Internet Safety |

|
I understand cybersecurity can be complex and daunting, but don't worry - I'm here to help. As someone who has researched this topic extensively, I'll share the three main pillars of cybersecurity clearly and concisely, ensuring you gain a solid unde...
Author: Newton Waweru |
|
|
|
|
3
|
Methods You Can Use to Protect Yourself from Social Engineering |

|
With the digital world evolving, the risk of social engineering has become a concern for many. Leveraging our expertise, we can arm you with methods to protect yourself against social engineering threats. This article will detail effective strategies...
Author: Newton Waweru |
|
|
|
|
4
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
5
|
The Biggest Cybersecurity Attacks Recorded |

|
Curious about the world of cybersecurity? To keep you informed, I have delved into the most massive cyber attacks ever recorded. Let's explore the critical incidents, their impact, and ways to stay protected together. By the end of this article, you'...
Author: Newton Waweru |
|
|
|
|
6
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
7
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
8
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
9
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
10
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
11
|
How to Become a Technician For Computer Repair in Topeka, KS? |

|
A computer technician is responsible for repairing and maintaining all the computer equipment. Further, they repair hardware, update software, and troubleshoot any computer networks if required. However, becoming a technician for Computer Repair Tope...
Author: Tithi Raha |
|
|
|
|
12
|
What Is Binary Also Known As? Discover the Different Names for Binary |

|
Uncover the secret of binary and its various names. Delve into the unique labels used to describe binary thoroughly. Embark on an enlightening journey to grasp this concept effortlessly with simple yet comprehensive information. Rely on my extensive ...
Author: Newton Waweru |
|
|
|
|
13
|
Is Binary Worth Learning? Know the Benefits of Learning Binary Code |

|
Are you wondering if learning binary is worth your time and effort? Discover the benefits of binary and see how it can enhance your career opportunities.
As a whole, learning binary can bring a multitude of benefits for individuals looking to en...
Author: Newton Waweru |
|
|
|
|
14
|
Why Was Binary Code Invented? Discover the History of Binary Code |

|
Discover the origin of binary code in this informative article. Have you ever wondered why binary code was invented and how it has revolutionized the way we process and store data?
As a whole, the invention of binary code was born as a solution for ...
Author: Newton Waweru |
|
|
|
|
15
|
Binary Code vs. Bytecode [Understand the Difference] |

|
Are you struggling to understand the difference between binary code and bytecode? This article will break down the key differences and give you a clear understanding of these coding concepts. Get ready to become a coding expert and impress your tech-...
Author: Newton Waweru |
|
|
|
|
16
|
Binary Code vs. Source Code [Know the Difference] |

|
In this article, we'll delve into the differences between binary code and source code and provide examples to assist in understanding the usage and application of each in the realm of computer programming. Whether you're a beginner or an experienced ...
Author: Newton Waweru |
|
|
|
|
17
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
18
|
What is The Annual Salary of Computer Repair Technicians in Topeka KS? |

|
The Computer Repair Topeka, KS technician is deemed responsible for providing preventive maintenance and ongoing support as required. Recently, there has been incredible growth in the use of technology and computers as every business today utilizes c...
Author: Tithi Raha |
|
|
|
|
19
|
Binary Code and Electronics Components “Logic Gates.” |

|
Uncover the mysteries of binary code and electronics components with this comprehensive guide to logic gates. If you're interested in learning about how binary code influences the functioning of electronic devices, you've come to the right place.
...
Author: Newton Waweru |
|
|
|
|
20
|
Binary code vs. Hexadecimal [A Guide to Understand the Differences] |

|
Are you struggling to understand the differences between Binary and Hexadecimal code? This comprehensive guide breaks down the complex concepts into easy-to-understand terms.
As a whole, Binary code and Hexadecimal are two methods of representing i...
Author: Newton Waweru |
|
|
|
|
21
|
Binary Code vs. Machine Language [Master the Difference] |

|
Do you find the distinction between binary code and machine language perplexing? Don't worry; you're not alone. This article will elaborate on the principal distinctions and assist you in undertanding the function of each in computer systems.
As a w...
Author: Newton Waweru |
|
|
|
|
22
|
Can You Code in Binary? A Beginners Guide to Binary Coding |

|
Are you ready to dive into the world of binary coding? It can seem intimidating at first but don't worry. I'm here to help guide you through the process. If you're a beginner, don't worry - we all have to start somewhere. And by the end of this guide...
Author: Newton Waweru |
|
|
|
|
23
|
What is Binary Code Used For? Learn Its Applications and Uses |

|
Explore the use of binary code and its implications in the current technology through this enlightening piece. If you're intrigued by the role of binary code in modern devices, you've arrived at the ideal destination.
As a whole, the binary system i...
Author: Newton Waweru |
|
|
|
|
24
|
Who Invented Binary Code? The Father of Binary Code |

|
George Boole is believed to be the "Father of Binary Code." Are you interested in knowing more about him? In that case, you have arrived at the correct location. I can answer any questions you may have about George Boole's life and legacy.
George B...
Author: Newton Waweru |
|
|
|
|
25
|
When Was Binary Code Invented? The History of Binary Code |

|
The utilization of binary code serves as the foundation of contemporary computing and holds a vital significance in the digital realm that surrounds us in the present time. Nonetheless, the question arises as to how this concept came into existence.
...
Author: Newton Waweru |
|
|
|
|
26
|
Binary Code: Is It Still Used in Modern Computing? |

|
Binary code, also known as machine language, has been a fundamental aspect of computer programming for decades. But with the constant evolution of technology and programming languages, one may wonder: is binary still relevant and used today?
Binary ...
Author: Newton Waweru |
|
|
|
|
27
|
Deciphering the World of Computer Acronyms: A Must-Know List |
|
Deciphering the World of Computer Acronyms: A Must-Know List
As technology continues to advance and evolve, it can be overwhelming to keep up with all the diff erent acronyms thrown around in the world of computers. There are so many other terms and...
Author: James Fleming |
|
|
|
|
28
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
29
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
30
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
31
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
32
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
33
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
34
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
35
|
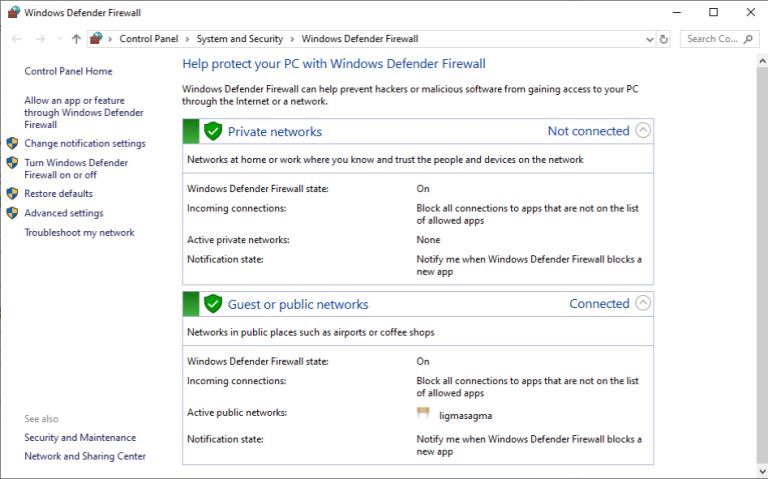
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|