|
1
|
Emerging Trends and Challenges in Cybersecurity |

|
In today's rapidly evolving digital landscape, emerging trends and challenges in cybersecurity are of great concern. Together, we'll explore these trends and challenges, arming you with the knowledge to protect your digital assets. This article will ...
Author: Newton Waweru |
|
|
|
|
2
|
How Do Authentication Processes Work Decoding Security |

|
Hello there! The mechanics of digital authentication might seem complex. This is a vast topic, but I'm here to clarify it with my deep understanding. This article will delve into the functioning of authentication processes.
Authentication processes ...
Author: Newton Waweru |
|
|
|
|
3
|
How Does TwoFactor Authentication 2FA Work |

|
Navigating online security can seem like a maze. I'm here to guide you through it. Let's explore the world of two-factor authentication (2FA), a vital tool for protecting your data. I've delved deep into this topic and promise to break it down in a w...
Author: Newton Waweru |
|
|
|
|
4
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
5
|
The Biggest Cybersecurity Attacks Recorded |

|
Curious about the world of cybersecurity? To keep you informed, I have delved into the most massive cyber attacks ever recorded. Let's explore the critical incidents, their impact, and ways to stay protected together. By the end of this article, you'...
Author: Newton Waweru |
|
|
|
|
6
|
Ways you Could Be Exposing Yourself to a Cybersecurity Attack |

|
Are you concerned about cybersecurity? You're not alone! As we increasingly rely on technology, protecting ourselves from cyber threats is crucial. I've researched this topic extensively, so I'm here to help. In this article, I'll explore ways you mi...
Author: Newton Waweru |
|
|
|
|
7
|
How Does Biometrics Change the Face of Security Enhancing Security |

|
Navigating the world of security can seem like a daunting task. With new technologies like biometrics rising, feeling curious and overwhelmed is normal. This article will guide you through how does biometrics change the face of security, providing in...
Author: Newton Waweru |
|
|
|
|
8
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
9
|
The Next Big Thing in Cyber Security Discover Innovative Solutions |

|
Ready to uncover the Next Big Thing in Cyber Security? You're not alone! As cyber threats evolve, so should our defenses. Fear not, I've delved deep into this crucial issue to help you stay informed and prepared. Join me in this article as we explore...
Author: Newton Waweru |
|
|
|
|
10
|
The Top 5 Best Drawing and Animation laptops Under 1000 Dollars |

|
The Top 5 Best Drawing and Animation laptops Under 1000 Dollars
When choosing the best drawing and animation laptop, there are crucial factors to consider for effective work results. These activities are intensive and require a computer with a quick...
Author: James Fleming |
|
|
|
|
11
|
Unlocking the Power of Your iPhone: How to Use It as a Webcam |

|
Unlocking the Power of Your iPhone: How to Use It as a Webcam
You're sitting in front of your computer, ready to video chat with a friend or client. But when you go to start the call, you realize your built-in webcam is nowhere to be found.
Don't w...
Author: James Fleming |
|
|
|
|
12
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
13
|
Tracking a Wi-Fi Password on Your Windows PC or Android Phone |

|
We need to have internet access to our devices, mostly smartphones and computers, to enjoy using them fully. This enables you to browse freely and interact with your friends on social media worldwide. One of the best ways to access the internet is ...
Author: James Fleming |
|
|
|
|
14
|
How to Search within Text Messages on iPhone or iPad |

|
How to Search within Text Messages on iPhone or iPad
Introduction
The iPhone is one of the most popular devices on the market. With its fingerprint scanner, touchscreen interface, and tons of cool apps, there's a reason it has become so popular. Bu...
Author: James Fleming |
|
|
|
|
15
|
iPod Repair tips: How to Repair an iPod Touch |

|
If you're like most people, your iPod Touch is a cherished part of your life. It's there for you when you need music or entertainment, and it's always reliable. But what do you do when something goes wrong with it? Don't worry - we're here to help.
...
Author: Faith Cheruiyot |
|
|
|
|
16
|
How Soon After Damage Can I Get My Iphone Fixed? |

|
iPhone users face different problems when using their phones. It forces them to take them to repair to resolve the issues. The duration taken depends on the level of damage. You must be careful when using your iPhone to prevent issues, as they can lo...
Author: Faith Cheruiyot |
|
|
|
|
17
|
What are the major iPhone issues that need repair? |

|
iPhone users always stand out from the rest due to their excellent performance. That does not mean that they don't face any issues. Luckily, all the issues have solutions, and some people can help you solve them
There are major iPhone issues that th...
Author: Faith Cheruiyot |
|
|
|
|
18
|
What To Be Amazing At Monitor Screen Repair? Here's How |

|
Are you interested in getting into the monitor screen repair business? It's a great way to make some extra money and help people when needed. But how do you become amazing at screen repair?
There are a few tips to get you started: First, practice m...
Author: Faith Cheruiyot |
|
|
|
|
19
|
How To Fix a Broken LCD Screen on Your Computer |

|
You're working on your computer one day when, suddenly, the screen goes black. You panic for a moment before realizing that it's just your LCD screen that's broken - not the whole computer. Phew! But now you're left with a broken LCD screen and don't...
Author: Faith Cheruiyot |
|
|
|
|
20
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
21
|
How to Electronically Sign PDFs Without Printing and Scanning Them |

|
You've been emailed a PDF document, which you must sign and return. You could print the document, sign it, then scan and email it back. However, there is a better, faster way. I'll demonstrate how to quickly add your signature to any PDF document and...
Author: Fay Kokri |
|
|
|
|
22
|
What to Do When You Forget Your Wi-Fi Password |

|
Forgetting WiFi passwords is common. However, tracing them is one hard task. I have detailed proven methods that will work on your device to view the WiFi passwords you forgot. Go through each one of them to see the one will give you the best results...
Author: Berts Njoroge |
|
|
|
|
23
|
How to Unlock Computer Screen Windows 10? |

|
Upon leaving your computer unattended, the windows screen automatically turns off after a while, and you would need to unlock it for further access and resume working. There are several methods to unlock Windows 10 regardless you know the passw...
Author: Tithi Raha |
|
|
|
|
24
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
25
|
Are Windows Computers better than Mac |

|
In everyday life, we often come across the term PC, which stands for a personal computer. This is the most direct definition of a PC; however, the term is also commonly used to refer to all other computers except Mac. Similarly, in this article, we w...
Author: Collins Okoth |
|
|
|
|
26
|
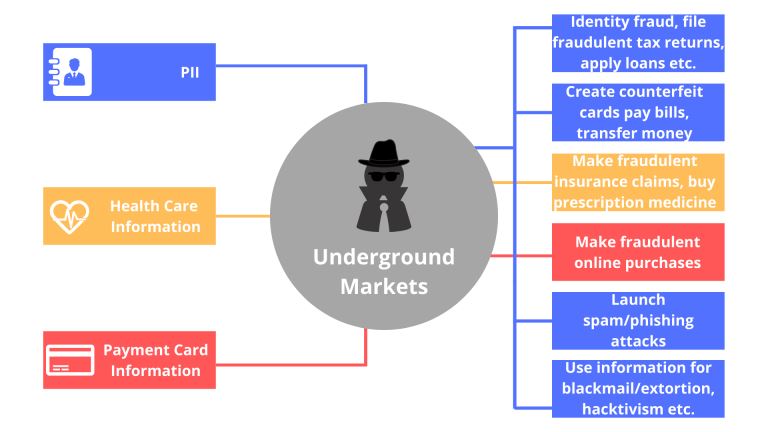
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
27
|
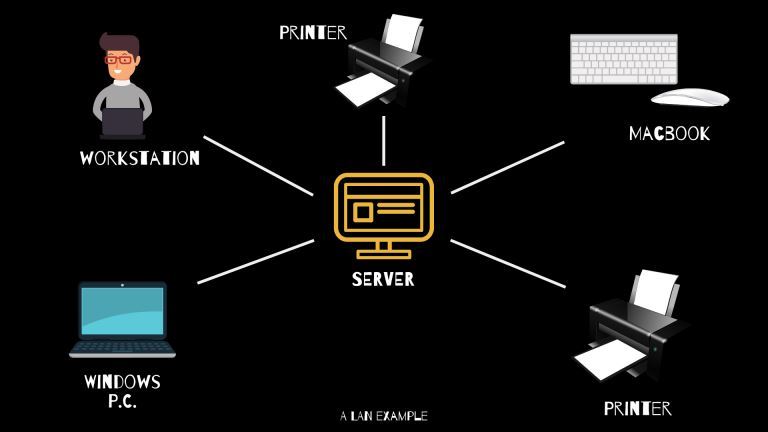
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|