|
1
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
2
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
3
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
4
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
5
|
Understanding the Service Host Process (svchost.exe) and Why there are Are Multiple Instances of Svc |

|
Service Host Process (svchost.exe) handles many essential functions in our computers, and serves an invaluable purpose in their correct operation. Without svchost.exe, computers would not be able to operate multiple services or programs at once or ...
Author: James Fleming |
|
|
|
|
6
|
Deciphering the World of Computer Acronyms: A Must-Know List |
|
Deciphering the World of Computer Acronyms: A Must-Know List
As technology continues to advance and evolve, it can be overwhelming to keep up with all the diff erent acronyms thrown around in the world of computers. There are so many other terms and...
Author: James Fleming |
|
|
|
|
7
|
A Complete Guide to Disk Errors and How to Repair Them in Windows 10/11 |

|
A Complete Guide to Disk Errors and How to Repair Them in Windows 10/11
Let's face it: everyone has had at least one hard drive error in their lifetime. They're a certainty that we will eventually have to deal with. Fortunately, there are several w...
Author: James Fleming |
|
|
|
|
8
|
Why can't I see other computers on my network Mac? |

|
Why can't I see other computers on my network Mac?
The most challenging aspect of connecting to a network is getting all the computers on the same page. It can be a frustrating experience if you can't see other machines on your Mac network. Fortunat...
Author: James Fleming |
|
|
|
|
9
|
How Do I Check Ping Both In Windows 10 & Mac? |

|
Whether you want to test your computer network or check the internet connection quality, conducting a ping test is certainly necessary. A ping test can indicate whether the problem behind a slow internet is due to your local network issue. Or, your I...
Author: Tithi Raha |
|
|
|
|
10
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
11
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Email Setup: How Can I Use Gmail as An SMTP Server? |

|
Did you know you can use your Gmail as na SMTP server? Well, now you know. One of the little-known freebies Gmail offers is a portable SMTP server that allows users to send mail to any email address from any network. You can use Google's SMTP server...
Author: Faith Cheruiyot |
|
|
|
|
13
|
How to Configure Email Client To Send Mail Through My Own SMTP Server? |

|
SMTP is the internet standard for sending and receiving emails. Email clients use SMTP to send messages to a mail server, while email servers use it to forward messages to their recipients. You need to enter your SMTP settings to use the email from a...
Author: Faith Cheruiyot |
|
|
|
|
14
|
How In-home Computer Service Is Important to You |

|
There's no doubt that having a computer is important in this day and age. However, what happens when your computer breaks? Chances are you might not have the money to take it in for repair, or maybe you don't have the time to wait for it to be fixed....
Author: Faith Cheruiyot |
|
|
|
|
15
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
16
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
17
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
18
|
Why is My Ping So High All Of a Sudden? Check Out The Reasons! |

|
Ping latency is a crucial thing to maintain especially when it comes to gaming that requires fast responsiveness from your end. For any online gaming, you need a lower ping to better experience everything. High ping can negatively alter the gaming ex...
Author: Tithi Raha |
|
|
|
|
19
|
Can You Log Into a WI-FI Network That Does Not Have Internet Access? |

|
Imagine you're working on an important project online that has a strict deadline, and all of a sudden, your internet connection goes off!! How would you feel? Well, we know, it can be one of the most frustrating things to deal with. But, the truth is...
Author: Tithi Raha |
|
|
|
|
20
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
21
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
22
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
23
|
Why can't I open pdf attachments in my email? |

|
Do you experience issues when you are about to open your PDF attachment? It's been a significant problem among us, I included. So I decided to research why this problem occurs. In my research, I am writing this article to aid you in handling PDF atta...
Author: Janet Kathalu |
|
|
|
|
24
|
Windows 10 Task Manager: The Complete Guide |

|
Windows task manager is a valuable tool for your PC. However, understanding how it works and when you need it is something else. So, I have compiled a comprehensive guide on Windows 10 task manager that will help you make use of it. Let's get started...
Author: Fay Kokri |
|
|
|
|
25
|
What Does a Virus Scan Actually Do: A Definitive Guide |

|
A virus scan runs through a computer system to check malicious threats and remove them. There are two types of protection provided by antivirus software during a virus scan. This includes proactive and reactive protection. The former spots potential ...
Author: Tithi Raha |
|
|
|
|
26
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
27
|
Internet:How do you fixing internet connection issues in windows 10? |

|
An unreliable internet connection can cost you a lot, especially if you work from home. When you are attending a zoom meeting or streaming movies or gaming and out of nowhere your internet drops or becomes so slow. This is a situation when you want t...
Author: Berts Njoroge |
|
|
|
|
28
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
29
|
My Computer is Running Slow, What Steps Can I Take to Fix It? |
|
Using a slow computer can make the simplest of jobs feel very irritating and cumbersome. Your files take forever to launch, your browser keeps hanging, words you type do not show up on time, and you keep getting the ‘Not Responding’ error message whe...
Author: Ian Musyoka |
|
|
|
|
30
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
31
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
32
|
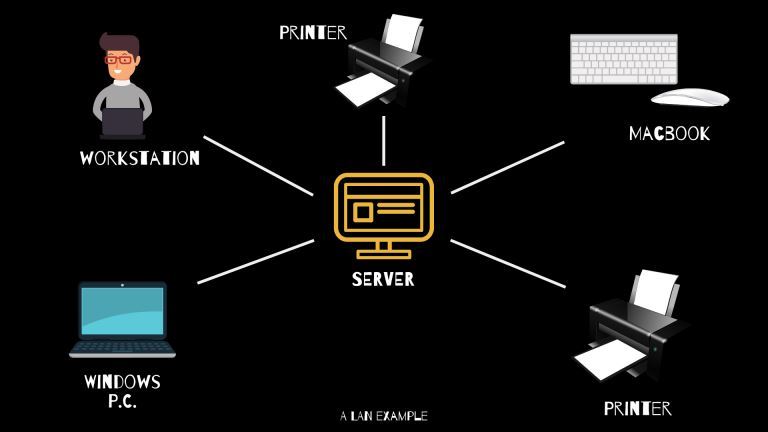
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
33
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
34
|
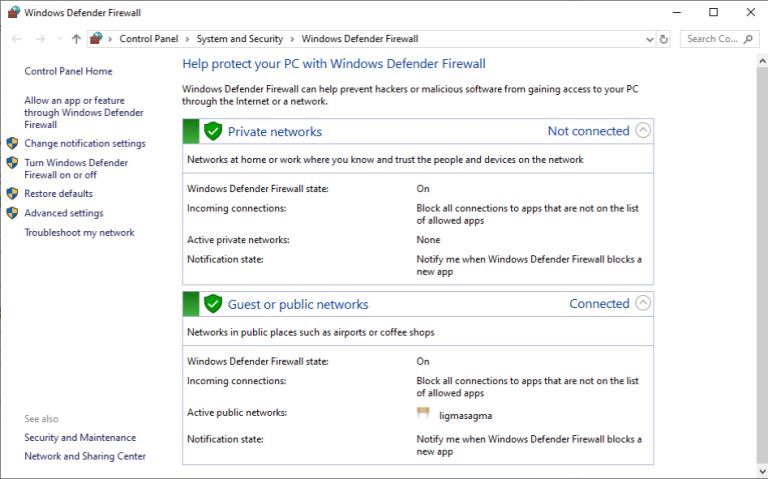
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
35
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|