|
1
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
2
|
System 32 Directory and its Importance |

|
System 32 Directory and its Importance
The average device user can run into problems figuring out which files to delete and which to save. While clearing unnecessary files on the hard drive can improve the speed and performance of your system, some ...
Author: James Fleming |
|
|
|
|
3
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
4
|
Data Restore: What are the 3 data recovery options? |

|
Data recovery involves different phases. Do you need some help to get your data back, or do you want to know more about data recovery? The recovery options entail different types of backup deployed by the users. It is essential to determine how long ...
Author: Faith Cheruiyot |
|
|
|
|
5
|
Theater Size: What's The Average Size of a Theater? |

|
Do you know how big the average theater is? Probably not, because it varies depending on the type of theater. The services cater to a wide range of screen sizes. The standard cinema screen is about 45 to 65 feet wide and as tall as 30 feet.
On avera...
Author: Faith Cheruiyot |
|
|
|
|
6
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
7
|
How to Fix a Tablet That Won't Connect to Wi-Fi |

|
Most WI-FI connection issues result from different issues which are fixable. One must follow several steps and perform different actions to fix the issues. Troubleshooting WIFI issues are common amongst tablet users. If it's a software cause, you can...
Author: Faith Cheruiyot |
|
|
|
|
8
|
What is the Best Software for Making Video Tutorials? |

|
Are you planning to make video tutorials? Do you want to explain how your products and services function using the software? Video Tutorial software is ideal as it lets you edit, generate, manipulate and enhance videos. Such ensures the corporate and...
Author: Faith Cheruiyot |
|
|
|
|
9
|
How Do You Ping a Modem? What's The Importance? |

|
A modem ping usually determines the type of connectivity your device will share with a remote host or with another device. This instantaneous task can be performed manually. But, the process only takes a few minutes and requires you to complete all t...
Author: Tithi Raha |
|
|
|
|
10
|
Will A Better Router Improve Your Ping? What Are Other Benefits? |

|
You have waited so long for your favorite game to release online and now you've downloaded it to play and suddenly you notice aggressive lagging on your PC. Isn't that annoying? In most cases, lagging while playing games occur due to a higher ping. A...
Author: Tithi Raha |
|
|
|
|
11
|
How Do You Locate Someone's IP Address? 4 Ways to Apply! |

|
An IP address is a simple numeric address used for identifying unique devices in a network. You can easily find the IP address of your own, but there are times when you may need to locate someone's IP address. Maybe you want to blacklist them or you ...
Author: Tithi Raha |
|
|
|
|
12
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
13
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
14
|
What is the best location for your home theater |

|
I bet you have walked into some homes and noticed the location of the home theater. It could've been placed in a perfect location, but that's not the case in most instances, so where should a home theater be placed precisely? That gets us to this art...
Author: Nancy Museo |
|
|
|
|
15
|
TV Repair: What Everyone Must Know About TV Repair |

|
TV repairs are common issues in many homes; we deal with them daily. Nothing should stop you from enjoying an excellent family time watching evening movies; in this article, you will be enlightened with several tips on handling minor TV Repairs.
The...
Author: Nancy Museo |
|
|
|
|
16
|
What to do when CCTV cameras power supply stop working? |

|
It has been a major issue among people when it comes to how to handle CCTV cameras. The major puzzle is how to tell if the power supply is the issue and what to do, how to detect the problem, why you are getting uncolored pictures, why your footage a...
Author: Janet Kathalu |
|
|
|
|
17
|
Things You Should Know about EFI System Partition (ESP) |

|
Most people have no idea what EFI system partition is, its components, its importance, or how it functions. In this article, you'll learn and understand everything there is to know about the EFI system partition.
There are four components of the EFI...
Author: Janet Kathalu |
|
|
|
|
18
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
19
|
Digital Storage: How Big Are Gigabytes, Terabytes, and Petabytes? |

|
Have you come across data storage units like Petabytes, Gigabytes, and Terabytes? What do they mean in the real world of data storage? The articles will make you comprehend the complexity of units of data storage and their actual sizes. Let us see ho...
Author: Faith Cheruiyot |
|
|
|
|
20
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
21
|
What Is Overclocking? Beginner's Guide to Speeding up PCs |

|
Overclocking is essentially an act of manually increasing the clock speeds of the CPU, RAM, or GPU. It is common among computer geeks, IT professionals, and heavy computer users like Gamers interested in maximizing their processor's potential. To suc...
Author: Collins Okoth |
|
|
|
|
22
|
Is the Thunderbolt 3 the same as the USB-C? |

|
The Thunderbolt 3 and USB Type C are two distinct technologies that are also quite closely related. These two devices are indistinguishable from the bare eyes except for their logos. However, there are more distinctive features when we examine their ...
Author: |
|
|
|
|
23
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
24
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
25
|
What is the Internet of Things IoT |
|
The Internet of things (IoT) is a general term for the increasing number of electronics that are not conventional computer equipment but connected to the Internet to send information, receive instructions, or both.
Tech analyst company IDC forecasts...
Author: Collins Okoth |
|
|
|
|
26
|
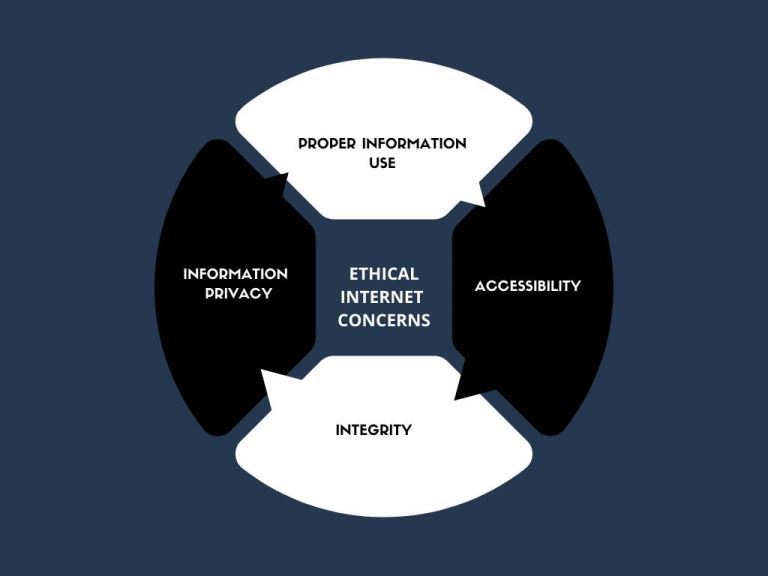
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
27
|
Which Windows Computer is Best? |

|
When you are in the market for a new computer, you will likely be debating whether to purchase a Mac or a Windows computer. However, this is not the end of the deliberating process; if you opt for a Windows computer, you will need to choose from a br...
Author: Collins Okoth |
|
|
|
|
28
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
29
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
30
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
31
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
32
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
33
|
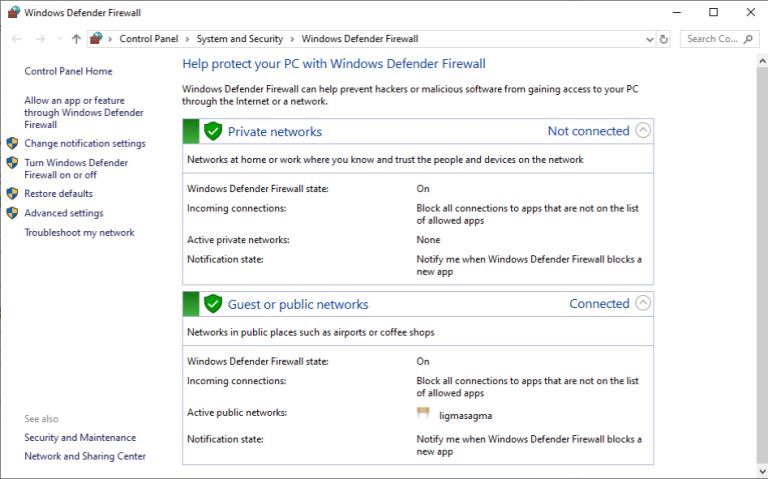
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
34
|
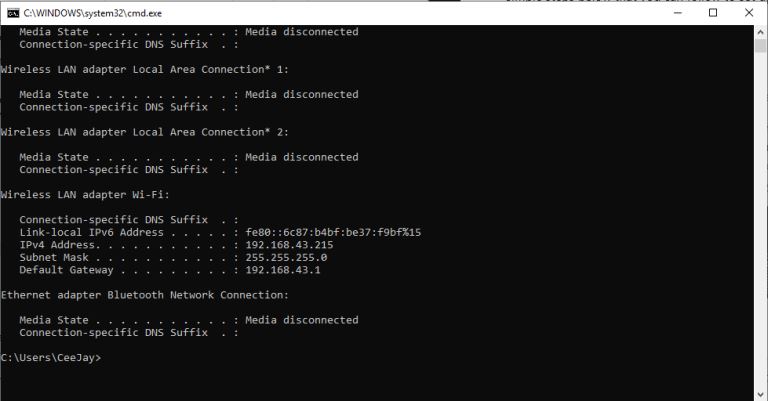
How Do I Find My IP Address |
|
The internet is a worldwide network of unrelated computers yet able to communicate successfully by following a specific set of rules. These rules are commonly known as protocols. A fundamental yet essential tenet of the internet is the Internet Proto...
Author: Collins Okoth |
|
|
|
|
35
|
What Is Processor Virtualization Technology? |

|
In computing, many things can be made virtual, and there are various types of virtualization: network, desktop, and application virtualization. There are some challenges involved in the virtualization of modern processors (i.e., those built on x86 ar...
Author: Trey Williams |
|
|
|