|
1
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
2
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
3
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
4
|
Types of Intrusion Detection Systems Host and Network |

|
You've come to the right place to learn about the various types of Intrusion Detection Systems (IDS). This article will provide a comprehensive overview of the different IDS types, ensuring you're well-equipped to make an informed decision.
In total...
Author: Newton Waweru |
|
|
|
|
5
|
How Can an Intrusion Detection System Protect Your Company |

|
Concerned about your company's cybersecurity? An Intrusion Detection System (IDS) might be your perfect solution. I understand how critical it is to protect sensitive data, and I've delved into the topic to provide the guidance you need.
An intrusi...
Author: Newton Waweru |
|
|
|
|
6
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
7
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
8
|
Why Do You Need a Computer Repair Technician in Topeka Kansas |

|
For a regular computer user, motherboards, processors, servers, or any other computer parts seem nothing more than just a pile of hardware and wires. However, a technician for Computer Repair Topeka, KS, or any other area can check these parts, diagn...
Author: Tithi Raha |
|
|
|
|
9
|
What Are The Duties of a Computer Repair Technician in Topeka KS |

|
From diagnosing initial issues to finding a solution, a computer repair technician in Topeka or any other area is responsible for all phases of the entire repair process. Moreover, the primary duty of a repair technician is to leave your device funct...
Author: Tithi Raha |
|
|
|
|
10
|
Binary Code vs. Gray Code [Master the Basics] |

|
Unlock the secrets of digital coding and get ahead with my comprehensive guide to Binary Code vs. Gray Code. I understand your need for clear, concise information and are here to help. Get ready to master the basics and gain confidence in your codin...
Author: Newton Waweru |
|
|
|
|
11
|
Is Binary Worth Learning? Know the Benefits of Learning Binary Code |

|
Are you wondering if learning binary is worth your time and effort? Discover the benefits of binary and see how it can enhance your career opportunities.
As a whole, learning binary can bring a multitude of benefits for individuals looking to en...
Author: Newton Waweru |
|
|
|
|
12
|
Knowing Your Android Phone Model. |

|
Knowing Your Android Phone Model.
Introduction.
A phone model is a style or design of a smartphone that producers often release in a series; examples may include the Tecno Camon 11 and Tecno Spark 7p.
Why know your phone models?
Every phone rel...
Author: James Fleming |
|
|
|
|
13
|
Where's the 'Task Manager' on a Mac? |

|
Where's the 'Task Manager' on a Mac?
When it comes to running and managing applications on your Mac, the Task Manager is a tool that will help you. Like Windows Task Manager, this Mac Task Manager will help you monitor processes in progress, check s...
Author: James Fleming |
|
|
|
|
14
|
Binary Code vs. Bytecode [Understand the Difference] |

|
Are you struggling to understand the difference between binary code and bytecode? This article will break down the key differences and give you a clear understanding of these coding concepts. Get ready to become a coding expert and impress your tech-...
Author: Newton Waweru |
|
|
|
|
15
|
Binary Code vs. Source Code [Know the Difference] |

|
In this article, we'll delve into the differences between binary code and source code and provide examples to assist in understanding the usage and application of each in the realm of computer programming. Whether you're a beginner or an experienced ...
Author: Newton Waweru |
|
|
|
|
16
|
How to Develop a Cloud Strategy | A step-by-step Guide |

|
When developing a cloud strategy, it's important to outline the best services and tools for a cloud solution. Your cloud strategy should include leveraging the company's IT capabilities with business needs that yield the most benefit from cloud compu...
Author: Eunice Njuguna |
|
|
|
|
17
|
Everything You Need to Know About (Dwm.exe) Desktop Window Manager |

|
Everything You Need to Know About (Dwm.exe) Desktop Window Manager
Introduction
What Is Desktop Window Manager (dwm.exe)? Desktop Window Manager or dwm.exe can be an integral part of Windows OS. These system processes are essential to controlling v...
Author: James Fleming |
|
|
|
|
18
|
What is The Blue Screen of Death? |

|
What is The Blue Screen of Death?
The dreaded Blue Screen of Death is a common term among gamers and PC users that potentially signal a catastrophic failure of your hardware. The term accurately describes a blue screen that appears on your device wi...
Author: James Fleming |
|
|
|
|
19
|
Searching for a Song by Humming on Google |

|
Finding a song through humming can be challenging, but with the help of Google and other tools, it is possible to identify the song you have in mind.
Here Are Some Steps You Can Follow to Find a Song on Google Through Humming:
Start by humming th...
Author: James Fleming |
|
|
|
|
20
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
21
|
Diagnostic Tips: Why is Computer Diagnostic Important? |

|
Is your computer screen freezing or going blank? Are you experiencing strange noises, slow internet, and abnormal functioning of the operating system? Do not be anxious. Computer problems are normal. However, these issues may be trivial and require q...
Author: Faith Cheruiyot |
|
|
|
|
22
|
Computer Tune-Up Tip: How To Remove Junk Files From Your Computer |

|
When using your computer to do different tasks, temporary files help you perform various actions and tasks. Once the task is over, the files remain without any deletion. They become useless, and you can't use them again. Most of them accumulate, and ...
Author: Faith Cheruiyot |
|
|
|
|
23
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
24
|
Tablet Repair: How To Fix A Tablet That Won't Turn On |

|
Aspiring to fix your tablet that did not turn on or hire someone? Before starting, it is good to understand fundamental issues in tablet repair. Knowing that will help you be in a position to understand the fundamentals of repair and maintenance.
Th...
Author: Faith Cheruiyot |
|
|
|
|
25
|
How Do You Locate Someone's IP Address? 4 Ways to Apply! |

|
An IP address is a simple numeric address used for identifying unique devices in a network. You can easily find the IP address of your own, but there are times when you may need to locate someone's IP address. Maybe you want to blacklist them or you ...
Author: Tithi Raha |
|
|
|
|
26
|
DC Jack Repair: How to Fix a Broken DC Jack |

|
If your laptop is having issues with charging, there's a good chance the DC jack is broken. This repair guide will show you how to fix a broken DC jack on your laptop.
There are a few things you can do to repair a broken DC jack. One of the first th...
Author: Faith Cheruiyot |
|
|
|
|
27
|
What are the 5 Computer Problems and Their Solution? |

|
Are you experiencing a problem with your computer? Has your computer ever stopped operating abruptly? Fortunately, these issues may only require simple solutions to fix. You do not need an IT expert or engineer to solve them. Try some quick fixes to ...
Author: Faith Cheruiyot |
|
|
|
|
28
|
How to Fix a Stereo Receiver That is Not Making Sound |

|
Are you having an issue with your stereo sound receiver? Is the power on, but you are receiving no sound from your speakers? In such a case, a troubleshooting procedure can help fix the problem before tossing off your remote or disconnecting any wire...
Author: Faith Cheruiyot |
|
|
|
|
29
|
What Should You Do For a Fast TV Repair? |

|
Undoubtedly we all require fast TV repair for our devices; it's really frustrating to know that your TV needs a repair, and unfortunately, there is nothing you can do about it. I'm here to help you out with how you should handle such a situation.
Y...
Author: Nancy Museo |
|
|
|
|
30
|
Windows 10 Task Manager: The Complete Guide |

|
Windows task manager is a valuable tool for your PC. However, understanding how it works and when you need it is something else. So, I have compiled a comprehensive guide on Windows 10 task manager that will help you make use of it. Let's get started...
Author: Fay Kokri |
|
|
|
|
31
|
Things You Should Know about EFI System Partition (ESP) |

|
Most people have no idea what EFI system partition is, its components, its importance, or how it functions. In this article, you'll learn and understand everything there is to know about the EFI system partition.
There are four components of the EFI...
Author: Janet Kathalu |
|
|
|
|
32
|
Pros and Cons of Overclocking RAM |

|
Have you ever heard of the term overclocking? Well, if not, I am sure you can take a good guess at what it means. Overclocking can be defined as the act of resetting your computer's Memory or central processing unit (CPU) to operate at a much higher ...
Author: Collins Okoth |
|
|
|
|
33
|
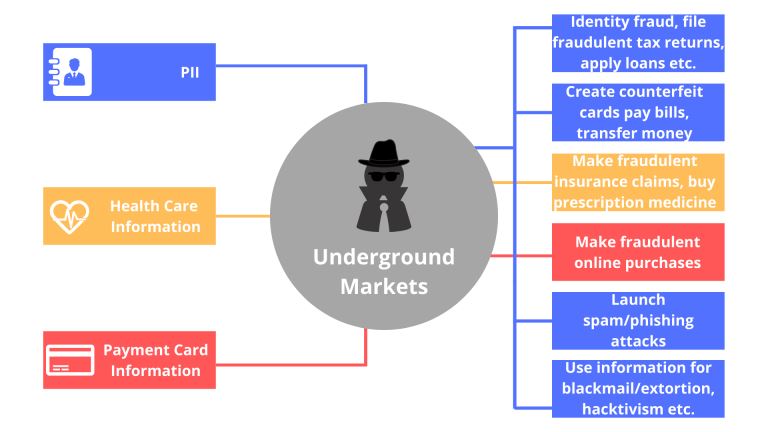
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
34
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
35
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|