|
1
|
What are the Challenges Faced in Cybersecurity Risks and Solutions |

|
Cybersecurity is a growing concern, and navigating its challenges can be daunting. You're not alone in seeking help; I'm here to provide the guidance you need. This article dives into the key obstacles faced in cybersecurity, offering practical insig...
Author: Newton Waweru |
|
|
|
|
2
|
The Range and Scope of Internet Ethics A Comprehensive Guide |

|
Diving into the complex world of Internet Ethics? You're not alone! I've explored the range and scope of this topic to help you navigate these ethical dilemmas. This article will provide insights and guidance, ensuring you make informed decisions onl...
Author: Newton Waweru |
|
|
|
|
3
|
What are the 10 Commandments of Computer Ethics |

|
Navigating the digital world with respect and integrity is essential. As an expert in computer ethics, I've delved into the 10 Commandments of Computer Ethics, the cornerstone of responsible digital behavior. This article aims to help you better und...
Author: Newton Waweru |
|
|
|
|
4
|
What is a Possible Effect of Malicious Code |

|
Navigating the digital world can feel like a labyrinth, especially when malicious code lurks in the shadows. It's alarming, I know. But fear not; I've delved into this complex issue to help guide you. In this article, we'll illuminate the potential e...
Author: Newton Waweru |
|
|
|
|
5
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
6
|
What is the Controversy that Destroyed Net Neutrality |

|
Hey there, you're curious about the controversy that led to the destruction of net neutrality. I can relate, as it's a complex topic with many opinions. I've thoroughly researched and am confident I can help clarify things for you. This article will ...
Author: Newton Waweru |
|
|
|
|
7
|
The Biggest Cybersecurity Attacks Recorded |

|
Curious about the world of cybersecurity? To keep you informed, I have delved into the most massive cyber attacks ever recorded. Let's explore the critical incidents, their impact, and ways to stay protected together. By the end of this article, you'...
Author: Newton Waweru |
|
|
|
|
8
|
Ways you Could Be Exposing Yourself to a Cybersecurity Attack |

|
Are you concerned about cybersecurity? You're not alone! As we increasingly rely on technology, protecting ourselves from cyber threats is crucial. I've researched this topic extensively, so I'm here to help. In this article, I'll explore ways you mi...
Author: Newton Waweru |
|
|
|
|
9
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
10
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
11
|
The Danger of Mixing Cyberwarfare with Cyber Espionage |

|
Are you concerned about the potential hazards of combining cyber warfare and cyber espionage? You're not alone. As someone who has delved deep into this critical issue, I understand your concerns and am here to help. This article will explore the ris...
Author: Newton Waweru |
|
|
|
|
12
|
How Can an Intrusion Detection System Protect Your Company |

|
Concerned about your company's cybersecurity? An Intrusion Detection System (IDS) might be your perfect solution. I understand how critical it is to protect sensitive data, and I've delved into the topic to provide the guidance you need.
An intrusi...
Author: Newton Waweru |
|
|
|
|
13
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
14
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
15
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
16
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
17
|
The Next Big Thing in Cyber Security Discover Innovative Solutions |

|
Ready to uncover the Next Big Thing in Cyber Security? You're not alone! As cyber threats evolve, so should our defenses. Fear not, I've delved deep into this crucial issue to help you stay informed and prepared. Join me in this article as we explore...
Author: Newton Waweru |
|
|
|
|
18
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
19
|
How to Select The Best Computer Repair Shop in Topeka, KS |

|
When you're dealing with computer issues requiring a professional's help, it's essential to make sure that you choose the ideal Computer Repair in Topeka, Kansas, or any other area to avoid major damages or unfavorable situations. Hiring the wrong re...
Author: Tithi Raha |
|
|
|
|
20
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
21
|
How to Develop a Cloud Strategy | A step-by-step Guide |

|
When developing a cloud strategy, it's important to outline the best services and tools for a cloud solution. Your cloud strategy should include leveraging the company's IT capabilities with business needs that yield the most benefit from cloud compu...
Author: Eunice Njuguna |
|
|
|
|
22
|
What Workloads Can be Moved to The Cloud? |

|
The migration of workloads involves the transfer of virtual machines, software, or databases to the cloud. The migration characterizes the selection of existing workloads, changing them, and deploying them to a cloud platform. Most businesses move wo...
Author: Eunice Njuguna |
|
|
|
|
23
|
How Can I Tell If Cloud Computing Is Right For My Company? |

|
Cloud computing is right for you if your company needs support with data storage, infrastructure scaling, big data analytics, networking, backup service strategies, and application development. A business looking to boost productivity, create room fo...
Author: Eunice Njuguna |
|
|
|
|
24
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
25
|
Deciphering the World of Computer Acronyms: A Must-Know List |
|
Deciphering the World of Computer Acronyms: A Must-Know List
As technology continues to advance and evolve, it can be overwhelming to keep up with all the diff erent acronyms thrown around in the world of computers. There are so many other terms and...
Author: James Fleming |
|
|
|
|
26
|
Why is Downloading Slower Than Uploading? How Do You Fix It? |

|
You took a funny video that caught you off guard, so you wanted to post it online for others to see it. As you began uploading it, you noticed your internet upload speed was a couple of MB per second, while your YouTube video or other file download s...
Author: Tithi Raha |
|
|
|
|
27
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
28
|
How to setup virtual machine on Windows 11 and Windows 10 |

|
Did you know you have access to two operating systems on one computer? It is possible to install Windows 11 on your Windows 10 PC, even if your computer doesn't meet the requirement. Well, I have compiled the best guide to set up a virtual machine (V...
Author: Berts Njoroge |
|
|
|
|
29
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
30
|
What are the backup best practices using the cloud? |

|
Have you ever imagined what you would do if you lost all your crucial data? Of course, you cant imagine. Well, there is only one way to be sure of data safety and longevity- data backup. And the best thing is; cloud backup is here to make it easy to ...
Author: Faith Cheruiyot |
|
|
|
|
31
|
Internet Connection: Why Is My Internet So Slow |

|
We all have experienced slow internet speeds in our homes. I will guide you on the best way you can speed up your home internet, how different factors affect your speeds, and getting the best internet plans for your home or office. I will also guide ...
Author: Faith Cheruiyot |
|
|
|
|
32
|
Computer Repair: How to Detect Crypto Mining Malware |

|
The vast growth of the cryptocurrency market has been something to marvel at over the past few years. However, the concept of anonymous payouts has given cybercriminals a reason to be part of the game. They have developed crypto-mining malware that c...
Author: Ian Musyoka |
|
|
|
|
33
|
What Is WAN/LAN? |
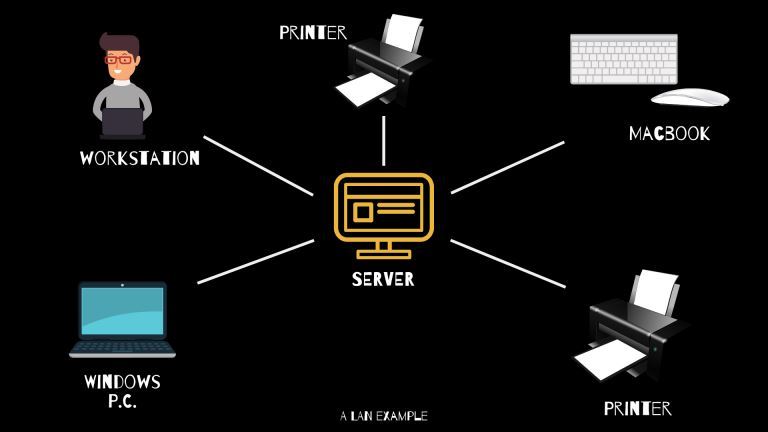
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
34
|
What Is Form Factor on A Motherboard? |
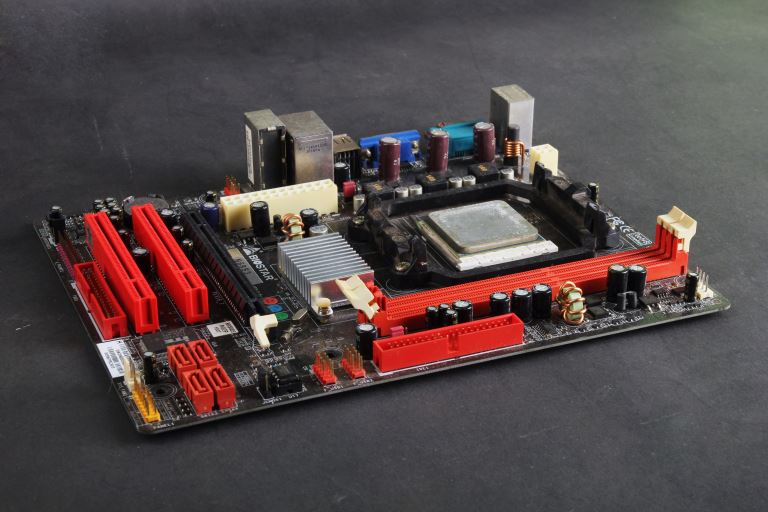
|
When talking about computers, the term 'motherboard' is highly likely to pop up on more than one occasion because it is vital. The primary function of the motherboard is to hold the microprocessor chip and give other parts the ability to connect to t...
Author: Delilah Daut |
|
|
|
|
35
|
What Is SATA 6GB/s |

|
The abbreviation SATA stands for Serial ATA (Advanced Technology Attachment), a modern generation drive interface preceded by the traditional wide and inconvenient Parallel ATA or PATA, also known as IDE. These technologies, PATA and SATA, describe t...
Author: Collins Okoth |
|
|
|