|
1
|
Emerging Trends and Challenges in Cybersecurity |

|
In today's rapidly evolving digital landscape, emerging trends and challenges in cybersecurity are of great concern. Together, we'll explore these trends and challenges, arming you with the knowledge to protect your digital assets. This article will ...
Author: Newton Waweru |
|
|
|
|
2
|
How To Protect Children from Predators and Online Grooming |

|
As a caring parent, guardian, or educator, ensuring children's safety, especially from online predators and grooming, is a pressing concern. We understand your worries, and you're not alone. In this article, we're exploring key strategies to protect ...
Author: Newton Waweru |
|
|
|
|
3
|
How Does Malware Work Malware Definition Types and Protection |

|
I understand how troubling it can be to deal with the mysteries of cyber threats like malware. Fear not, as I've delved into the subject to help simplify it for you. In this article, we'll untangle the intricacies of malware, how it works, and its im...
Author: Newton Waweru |
|
|
|
|
4
|
What are the 3 Main Pillars of Cybersecurity Internet Safety |

|
I understand cybersecurity can be complex and daunting, but don't worry - I'm here to help. As someone who has researched this topic extensively, I'll share the three main pillars of cybersecurity clearly and concisely, ensuring you gain a solid unde...
Author: Newton Waweru |
|
|
|
|
5
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
6
|
The Danger of Mixing Cyberwarfare with Cyber Espionage |

|
Are you concerned about the potential hazards of combining cyber warfare and cyber espionage? You're not alone. As someone who has delved deep into this critical issue, I understand your concerns and am here to help. This article will explore the ris...
Author: Newton Waweru |
|
|
|
|
7
|
Types of Intrusion Detection Systems Host and Network |

|
You've come to the right place to learn about the various types of Intrusion Detection Systems (IDS). This article will provide a comprehensive overview of the different IDS types, ensuring you're well-equipped to make an informed decision.
In total...
Author: Newton Waweru |
|
|
|
|
8
|
How Can an Intrusion Detection System Protect Your Company |

|
Concerned about your company's cybersecurity? An Intrusion Detection System (IDS) might be your perfect solution. I understand how critical it is to protect sensitive data, and I've delved into the topic to provide the guidance you need.
An intrusi...
Author: Newton Waweru |
|
|
|
|
9
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
10
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
11
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
12
|
What Does a Computer Repair Topeka KS Technicians Do |

|
Computer Repair Topeka, KS technicians perform all the necessary steps to repair the malfunctioning computer software and hardware. Upon calling a technician, they will first diagnose the issues with your computer system and ensure all are returned t...
Author: Tithi Raha |
|
|
|
|
13
|
Where's the 'Task Manager' on a Mac? |

|
Where's the 'Task Manager' on a Mac?
When it comes to running and managing applications on your Mac, the Task Manager is a tool that will help you. Like Windows Task Manager, this Mac Task Manager will help you monitor processes in progress, check s...
Author: James Fleming |
|
|
|
|
14
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
15
|
How Can I Tell If Cloud Computing Is Right For My Company? |

|
Cloud computing is right for you if your company needs support with data storage, infrastructure scaling, big data analytics, networking, backup service strategies, and application development. A business looking to boost productivity, create room fo...
Author: Eunice Njuguna |
|
|
|
|
16
|
Understanding the Service Host Process (svchost.exe) and Why there are Are Multiple Instances of Svc |

|
Service Host Process (svchost.exe) handles many essential functions in our computers, and serves an invaluable purpose in their correct operation. Without svchost.exe, computers would not be able to operate multiple services or programs at once or ...
Author: James Fleming |
|
|
|
|
17
|
IOS CarPlay: How to Turn It Off |
|
IOS CarPlay: How to Turn It Off
Do you want to turn off iPhone support for Apple CarPlay? If that's the case, you're at the correct spot! This guide will show you how to disable CarPlay on your iPhone by providing detailed methods. We'll also go thr...
Author: James Fleming |
|
|
|
|
18
|
What Is An Example of Smart Home Automation? |

|
When it comes to the future of the home, many people think of smart homes. A smart home is a residence equipped with advanced automation features, making it more intelligent and efficient.
There are many different types of smart home automation, so...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Things You Should Know Before Buying a Smart Home Device |

|
Do you want to be able to control your lights and appliances from your phone? Or maybe you're looking for a more efficient way to heat and cool your home. If so, then you may be considering purchasing a smart home device.
There are some things you s...
Author: Faith Cheruiyot |
|
|
|
|
20
|
What To Be Amazing At Monitor Screen Repair? Here's How |

|
Are you interested in getting into the monitor screen repair business? It's a great way to make some extra money and help people when needed. But how do you become amazing at screen repair?
There are a few tips to get you started: First, practice m...
Author: Faith Cheruiyot |
|
|
|
|
21
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
22
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
23
|
What Download & Upload Testing Utilities Are There? |

|
Imagining a day without a stable internet connection can seem like a nightmare to most of us. Isn't it? Everything starting from our online communication, and entertainment to our everyday work, relies on a stable internet connection. Therefore, it'...
Author: Tithi Raha |
|
|
|
|
24
|
What are the 5 Computer Problems and Their Solution? |

|
Are you experiencing a problem with your computer? Has your computer ever stopped operating abruptly? Fortunately, these issues may only require simple solutions to fix. You do not need an IT expert or engineer to solve them. Try some quick fixes to ...
Author: Faith Cheruiyot |
|
|
|
|
25
|
Bluetooth hacks: How to hack a car's Bluetooth? |

|
Bluetooth hacking is one of the most familiar hacks that hackers use. If you are a car owner, you must take precautions to keep your car safe from hackers. I want to keep myself and my car safe; that's why I researched and wrote this article to guide...
Author: Janet Kathalu |
|
|
|
|
26
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
27
|
What to do when CCTV cameras power supply stop working? |

|
It has been a major issue among people when it comes to how to handle CCTV cameras. The major puzzle is how to tell if the power supply is the issue and what to do, how to detect the problem, why you are getting uncolored pictures, why your footage a...
Author: Janet Kathalu |
|
|
|
|
28
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
29
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
30
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
31
|
What is the Internet of Things IoT |
|
The Internet of things (IoT) is a general term for the increasing number of electronics that are not conventional computer equipment but connected to the Internet to send information, receive instructions, or both.
Tech analyst company IDC forecasts...
Author: Collins Okoth |
|
|
|
|
32
|
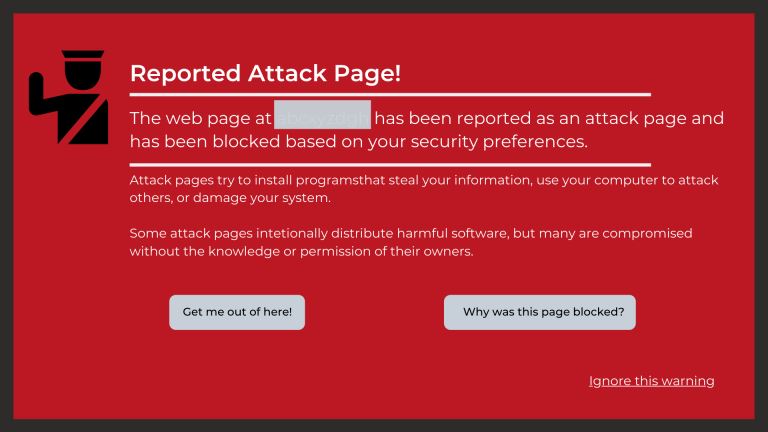
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
33
|
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
34
|
How Do I Find My IP Address |
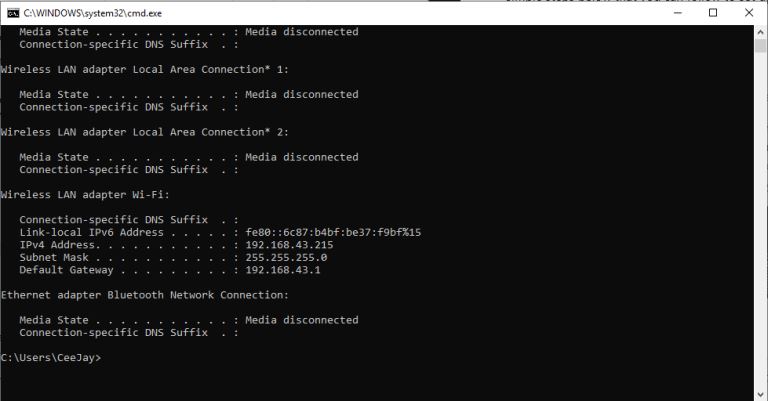
|
The internet is a worldwide network of unrelated computers yet able to communicate successfully by following a specific set of rules. These rules are commonly known as protocols. A fundamental yet essential tenet of the internet is the Internet Proto...
Author: Collins Okoth |
|
|
|
|
35
|
What Is Form Factor on A Motherboard? |
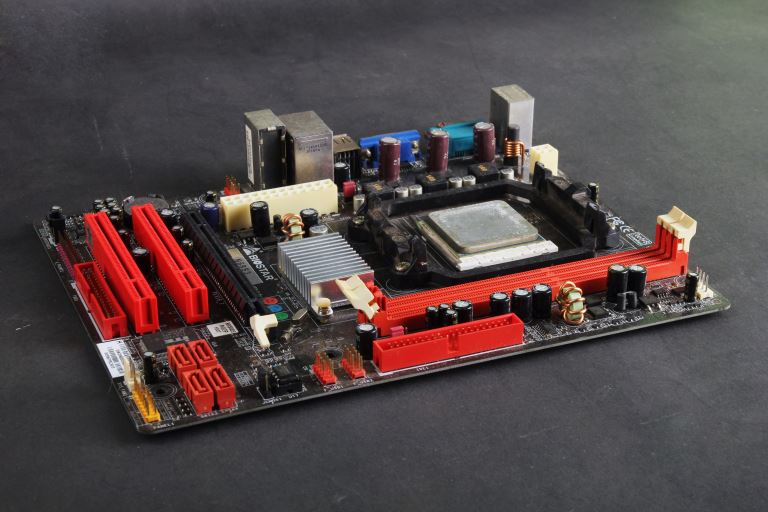
|
When talking about computers, the term 'motherboard' is highly likely to pop up on more than one occasion because it is vital. The primary function of the motherboard is to hold the microprocessor chip and give other parts the ability to connect to t...
Author: Delilah Daut |
|
|
|