|
1
|
How Can you Protect Yourself from Internet Hoaxes Digital Literacy |

|
Navigating the web can be tricky, with internet hoaxes lurking around. We understand your concern and are here to guide you. Our research will arm you with the knowledge to spot and evade these digital deceptions. This article is all about safeguardi...
Author: Newton Waweru |
|
|
|
|
2
|
What Methods Does HTTPS use that make it more secure than HTTP |

|
Navigating the digital landscape, it's essential to understand web security. Recognizing this, you want to explore HTTPS and its edge over HTTP. With my extensive cybersecurity knowledge, I'll help demystify this complex topic. This article focuses o...
Author: Newton Waweru |
|
|
|
|
3
|
What Is the Importance of Having a Strong Password Digital Protection |

|
Navigating the digital world, you may often wonder, "Why are strong passwords so crucial?" Passwords are your digital keys, guarding personal information and online identities. In this article, we'll delve into the importance of robust passwords to ...
Author: Newton Waweru |
|
|
|
|
4
|
What Does a Solid Access Control Policy Look Like |

|
Navigating the complexities of creating a robust access control policy can be challenging. This article will delve into the components of a solid access control policy, highlighting its importance in data protection and cybersecurity.
As a whole, a...
Author: Newton Waweru |
|
|
|
|
5
|
How Does TwoFactor Authentication 2FA Work |

|
Navigating online security can seem like a maze. I'm here to guide you through it. Let's explore the world of two-factor authentication (2FA), a vital tool for protecting your data. I've delved deep into this topic and promise to break it down in a w...
Author: Newton Waweru |
|
|
|
|
6
|
What Does a VPN Do Securing Digital Privacy |

|
Navigating the digital world can feel like walking through a minefield. Leveraging years of research, we'll unravel how VPNs safeguard your online presence, preserving your privacy and security. Brace yourself for an informative journey into what a V...
Author: Newton Waweru |
|
|
|
|
7
|
Why Should You Avoid Public Wifi Protecting Your Online Privacy |

|
Navigating the web safely is more crucial than ever. You might wonder, "What's the harm in using public Wi-Fi?" This article will explore why avoiding public Wi-Fi can significantly enhance online security. Let's delve into the risks and precautions ...
Author: Newton Waweru |
|
|
|
|
8
|
What are the Challenges Faced in Cybersecurity Risks and Solutions |

|
Cybersecurity is a growing concern, and navigating its challenges can be daunting. You're not alone in seeking help; I'm here to provide the guidance you need. This article dives into the key obstacles faced in cybersecurity, offering practical insig...
Author: Newton Waweru |
|
|
|
|
9
|
What is the Importance of EndUser Education Boosting Security |

|
Navigating the digital realm can be a daunting task. This article will detail how user education aids in maximizing tech usability and boosting security. We're here to help you comprehend and apply this valuable knowledge.
As a whole, the importance...
Author: Newton Waweru |
|
|
|
|
10
|
What are the Types of Cyber Security Types and Threats Defined |

|
Navigating the complex world of cyber security can be challenging, and we understand that. This article is a comprehensive exploration of the various types of cyber security, carefully crafted to equip you with the knowledge to secure your digital li...
Author: Newton Waweru |
|
|
|
|
11
|
What are the 10 Commandments of Computer Ethics |

|
Navigating the digital world with respect and integrity is essential. As an expert in computer ethics, I've delved into the 10 Commandments of Computer Ethics, the cornerstone of responsible digital behavior. This article aims to help you better und...
Author: Newton Waweru |
|
|
|
|
12
|
What is a Possible Effect of Malicious Code |

|
Navigating the digital world can feel like a labyrinth, especially when malicious code lurks in the shadows. It's alarming, I know. But fear not; I've delved into this complex issue to help guide you. In this article, we'll illuminate the potential e...
Author: Newton Waweru |
|
|
|
|
13
|
The Biggest Cybersecurity Attacks Recorded |

|
Curious about the world of cybersecurity? To keep you informed, I have delved into the most massive cyber attacks ever recorded. Let's explore the critical incidents, their impact, and ways to stay protected together. By the end of this article, you'...
Author: Newton Waweru |
|
|
|
|
14
|
What is the Importance of Internet Ethics Responsible Online Behavior |

|
Navigating the digital world, internet ethics is a vital topic you're not alone in exploring. I've got you covered. I empathize with your quest for guidance, and in this article, I'll discuss the importance of ethical conduct online, privacy, and sec...
Author: Newton Waweru |
|
|
|
|
15
|
Is Internet Access a Human Right Debate Discussion |

|
I understand how crucial the topic of internet access as a human right is in our digital age. As someone who delved into this issue, I'm here to help you navigate the debate. This article will explore both sides of the argument and provide the insigh...
Author: Newton Waweru |
|
|
|
|
16
|
How Does Biometrics Change the Face of Security Enhancing Security |

|
Navigating the world of security can seem like a daunting task. With new technologies like biometrics rising, feeling curious and overwhelmed is normal. This article will guide you through how does biometrics change the face of security, providing in...
Author: Newton Waweru |
|
|
|
|
17
|
How is Identity Theft Committed Technology |

|
Navigating the complex world of identity theft and technology can be daunting. Rest assured, I've thoroughly explored this landscape, and I'm here to guide you. This article unpacks how criminals exploit technology to commit identity theft, ensuring ...
Author: Newton Waweru |
|
|
|
|
18
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
19
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
20
|
How to change directories in Command Prompt on Windows 10 and 11 |

|
How to change directories in Command Prompt on Windows 10 and 11
If you are a Windows user, chances are you've heard of Command Prompt. It's an invaluable tool that allows you to interact with the system and perform tasks like running commands, open...
Author: James Fleming |
|
|
|
|
21
|
How to Show or Hide the Bookmarks Bar in Google Chrome |

|
For many of us, the Bookmarks Bar in Google Chrome is an indispensable way to quickly access our favorite websites or bookmarked content. It is a great feature that provides quick access, but it can quickly become cluttered when you save too many i...
Author: James Fleming |
|
|
|
|
22
|
Copying & Pasting On a Mac Computer |

|
Any computer user needs to be able to copy and paste. Copying and pasting make it simpler to move information from one place to another, whether working on a paper or browsing the web. The procedure is significantly easier if you use a Mac. Apple c...
Author: James Fleming |
|
|
|
|
23
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
24
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
25
|
MS Word:How to Create and Manage a Table of Contents in Microsoft Word |

|
Have you ever tried to go through a numerous-page document that has no Table of Contents? It s such a hectic task to trace specific information that is way far in the paper. I found it essential to guide you through expert steps to create an excellen...
Author: Berts Njoroge |
|
|
|
|
26
|
How do I get rid of low disk space in Windows 10? |

|
Low disk space warning appears on Windows operating system to warn the user that a specific location of the hard drive is low on storage space. This type of error is persistent and will keep reappearing until you work on it.
There are generally thre...
Author: |
|
|
|
|
27
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
28
|
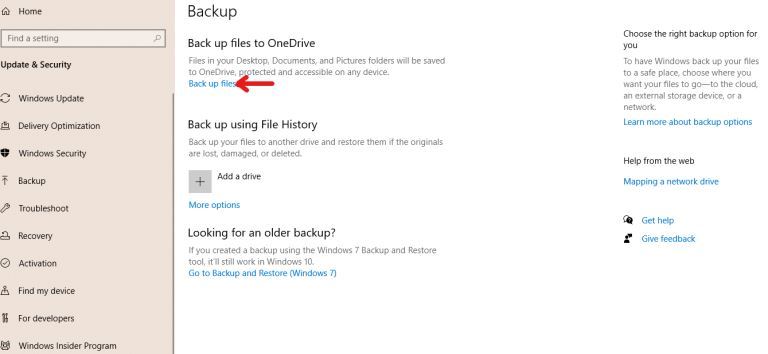
How to Backup Computer Windows 10? |
|
Backing up your computer windows 10 isn’t optional but a necessity.
The process starts by clicking on the “start” button on your Windows 10 system, navigating to the “setting” page, then to the “update & security” section, clicking on “backup,” and...
Author: Tithi Raha |
|
|
|
|
29
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|