|
1
|
What Does a Solid Access Control Policy Look Like |

|
Navigating the complexities of creating a robust access control policy can be challenging. This article will delve into the components of a solid access control policy, highlighting its importance in data protection and cybersecurity.
As a whole, a...
Author: Newton Waweru |
|
|
|
|
2
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
3
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
4
|
How to change directories in Command Prompt on Windows 10 and 11 |

|
How to change directories in Command Prompt on Windows 10 and 11
If you are a Windows user, chances are you've heard of Command Prompt. It's an invaluable tool that allows you to interact with the system and perform tasks like running commands, open...
Author: James Fleming |
|
|
|
|
5
|
Casting Your Windows or Android Display to a Windows 11 Computer |

|
Technology has come a long way in recent years and with it, the ability to project our computers or phone screens to a larger format. This can be useful for presentations, meetings, gaming, and more. Windows 11 PCs are capable of hosting these proj...
Author: James Fleming |
|
|
|
|
6
|
What You Need to Know Concerning the Latest Apple iOS Cheat Sheets |

|
What You Need to Know Concerning the Latest Apple iOS Cheat Sheets
Every mobile user wants a phone that works correctly and per their expectations. Every brand has different operating systems that improve phones' performance. For example, iPhone, iP...
Author: James Fleming |
|
|
|
|
7
|
Formatting a hard drive using the Command Prompt in Windows 10 |

|
Formatting a hard drive using the Command Prompt in Windows 10
Introduction:
Formatting a hard drive is deleting all the data and resetting it to a new state, ready to be used again. There are various methods to format a hard drive, and one of them...
Author: James Fleming |
|
|
|
|
8
|
Resolving the USB drive read-only issue in Windows 10/11 |

|
Resolving the USB drive read-only issue in Windows 10/11
Introduction:
Everyday issue users face while accessing their USB drives is the "read-only" error. This error prevents the user from making any changes to the files on the drive, including de...
Author: James Fleming |
|
|
|
|
9
|
6 Proven Ways to Remove Write Protection from USB in Windows 10 and Windows 11 |

|
6 Proven Ways to Remove Write Protection from USB in Windows 10 and Windows 11
How do you remove write protection from USB on Windows 10 or 11? Worry no more! With this simple guide, you can remove write protection from USB on a PC running the lates...
Author: James Fleming |
|
|
|
|
10
|
Reasons Why You May Not Be Able To Delete Files From Your SD |
|
You could occasionally have trouble erasing files from an SD card. And this can be annoying since you might be unable to figure out why you can't remove your files. In this article, we'll look at several potential causes for why you might find it dif...
Author: James Fleming |
|
|
|
|
11
|
What Are Your Strategies To Avoid Being A Victim Of Cybercrime? |

|
Cybercrimes have been on the increase, with many unaware victims. When we hear about cybercrimes, we automatically think about hackers. But cybercrime is not just about hacking. It goes beyond that. Many people today use their devices, such as phones...
Author: James Fleming |
|
|
|
|
12
|
Mac Repair Tips & Tricks That You Need To Know |

|
Mac operating system is reliable and famous among its users. Many people switch from other operating systems like Windows and Linux and would like to learn how to troubleshoot and fix any issues that come along the way.
There are many mac repair ti...
Author: Faith Cheruiyot |
|
|
|
|
13
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
14
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
15
|
How to Disable Notifications on Windows 10 |

|
Notifications popping up any time you are using your PC can be a nagging experience— they hurt your concentration adversely. However, there are ways and tricks you can disable computer notifications on windows 10. This article covers that and more.
...
Author: Fay Kokri |
|
|
|
|
16
|
How to Open the Command Prompt in Windows 10 |

|
If you've ever worked with codes, you're probably familiar with the Command Prompt. The Command Prompt is a program that is installed on all Windows computers and allows you to manage the computer with text commands. However, unlike other apps, the C...
Author: Faith Cheruiyot |
|
|
|
|
17
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
18
|
How to Use Google Docs: The Beginner's Guide to Google Docs |

|
The old way of storing documents on a hard disk is a thing of the past. The cloud-based solution is the new way to handle files. Google Docs is one of the best ways to create, edit and share word documents. You don't have to carry storage devices to ...
Author: Faith Cheruiyot |
|
|
|
|
19
|
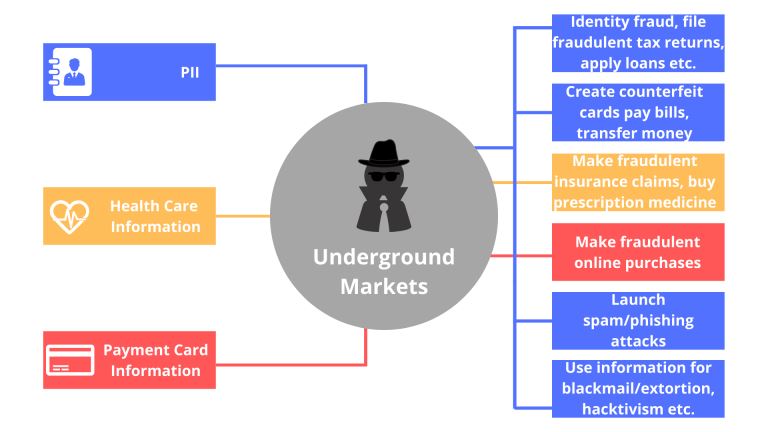
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
20
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
21
|
How to Get Rid of Computer Pop-Ups |

|
If you have had the chance to encounter pop-ups when working with your computer, you understand how frustrating and irritating it can get. They will slow down your device and even create a gateway for other malware to infect your computer. No compute...
Author: Cate Greff |
|
|
|
|
22
|
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
23
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|
|
24
|
What Is Processor Virtualization Technology? |

|
In computing, many things can be made virtual, and there are various types of virtualization: network, desktop, and application virtualization. There are some challenges involved in the virtualization of modern processors (i.e., those built on x86 ar...
Author: Trey Williams |
|
|
|