|
1
|
What Does a Solid Access Control Policy Look Like |

|
Navigating the complexities of creating a robust access control policy can be challenging. This article will delve into the components of a solid access control policy, highlighting its importance in data protection and cybersecurity.
As a whole, a...
Author: Newton Waweru |
|
|
|
|
2
|
What Does a VPN Do Securing Digital Privacy |

|
Navigating the digital world can feel like walking through a minefield. Leveraging years of research, we'll unravel how VPNs safeguard your online presence, preserving your privacy and security. Brace yourself for an informative journey into what a V...
Author: Newton Waweru |
|
|
|
|
3
|
What are the Challenges Faced in Cybersecurity Risks and Solutions |

|
Cybersecurity is a growing concern, and navigating its challenges can be daunting. You're not alone in seeking help; I'm here to provide the guidance you need. This article dives into the key obstacles faced in cybersecurity, offering practical insig...
Author: Newton Waweru |
|
|
|
|
4
|
What are the 3 Main Pillars of Cybersecurity Internet Safety |

|
I understand cybersecurity can be complex and daunting, but don't worry - I'm here to help. As someone who has researched this topic extensively, I'll share the three main pillars of cybersecurity clearly and concisely, ensuring you gain a solid unde...
Author: Newton Waweru |
|
|
|
|
5
|
Is Internet Access a Human Right Debate Discussion |

|
I understand how crucial the topic of internet access as a human right is in our digital age. As someone who delved into this issue, I'm here to help you navigate the debate. This article will explore both sides of the argument and provide the insigh...
Author: Newton Waweru |
|
|
|
|
6
|
Types of Intrusion Detection Systems Host and Network |

|
You've come to the right place to learn about the various types of Intrusion Detection Systems (IDS). This article will provide a comprehensive overview of the different IDS types, ensuring you're well-equipped to make an informed decision.
In total...
Author: Newton Waweru |
|
|
|
|
7
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
8
|
Where's the 'Task Manager' on a Mac? |

|
Where's the 'Task Manager' on a Mac?
When it comes to running and managing applications on your Mac, the Task Manager is a tool that will help you. Like Windows Task Manager, this Mac Task Manager will help you monitor processes in progress, check s...
Author: James Fleming |
|
|
|
|
9
|
How to Find Your Location History on iPhone or iPad |

|
How to Find Your Location History on iPhone or iPad
Nowadays, every smartphone user is tracking their location and movement. Apple records all your activities, so it's easy to find a record of your past location history. You may wonder how to view y...
Author: James Fleming |
|
|
|
|
10
|
Email Setup: How To Set Up a Mail Server On Windows or Mac OS X |

|
Do you want to send and receive emails with your windows or Mac OS X and connect to it using a smartphone or PC? This guide is for you.
There are several ways you can set up a mail server on Mac OS X. For example, you can use server setting prefere...
Author: Faith Cheruiyot |
|
|
|
|
11
|
Things You Should Know Before Buying a Smart Home Device |

|
Do you want to be able to control your lights and appliances from your phone? Or maybe you're looking for a more efficient way to heat and cool your home. If so, then you may be considering purchasing a smart home device.
There are some things you s...
Author: Faith Cheruiyot |
|
|
|
|
12
|
How to unlock computer screen Windows 11? |

|
Windows 11 has quite new features that are not in previous Windows versions. Learning how to do simple-to-complicated tasks is mandatory to have an excellent experience on Windows 11. One such task is unlocking Windows 11 screen. This article will di...
Author: Berts Njoroge |
|
|
|
|
13
|
How to Open the Control Panel on Windows 10 |

|
Knowing where to find the Control Panel in Windows 10 gives you access to the majority of the tools you'll need to customize or adjust your computer. I will show you how to open the Control Panel is a very simple task. Each step highlighted in ...
Author: Fay Kokri |
|
|
|
|
14
|
Windows 10 keyboard shortcuts cheat sheet |

|
With all Windows 10 keyboard shortcuts, it is hard to know which one to use where. However, in this article, you will understand all the most common Windows shortcuts that you can use daily. I have simplified them in a table making it easy for you to...
Author: Fay Kokri |
|
|
|
|
15
|
What Is a Burner Phone, and When Should You Use One |

|
I have been wondering how a burner phone can be used or if it is necessary to have one. I am sure I'm not the only one with such questions, so I did my research and wrote this article on burner phones and in which instances they can be helpful to bot...
Author: Janet Kathalu |
|
|
|
|
16
|
Windows 10: How to Boot Into Safe Mode on Windows 10 |

|
Information about booting into safe mode on Windows 10 is scarce and unclear. I have compiled tested and proven methods to help you boot into safe mode.
There are several ways to boot into safe mode on Windows 10. Here are the best steps to follow:
...
Author: Faith Cheruiyot |
|
|
|
|
17
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
18
|
How to install a printer driver manually and from a device |

|
Suppose you want to print documents on your computer and you find out your PC doesn't have printer drivers? It becomes challenging if you don't have the printer installer device at hand. However, as you will discover in this article, it is still poss...
Author: Gloria Mutuku |
|
|
|
|
19
|
Internet:How do you fixing internet connection issues in windows 10? |

|
An unreliable internet connection can cost you a lot, especially if you work from home. When you are attending a zoom meeting or streaming movies or gaming and out of nowhere your internet drops or becomes so slow. This is a situation when you want t...
Author: Berts Njoroge |
|
|
|
|
20
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
21
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
22
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
23
|
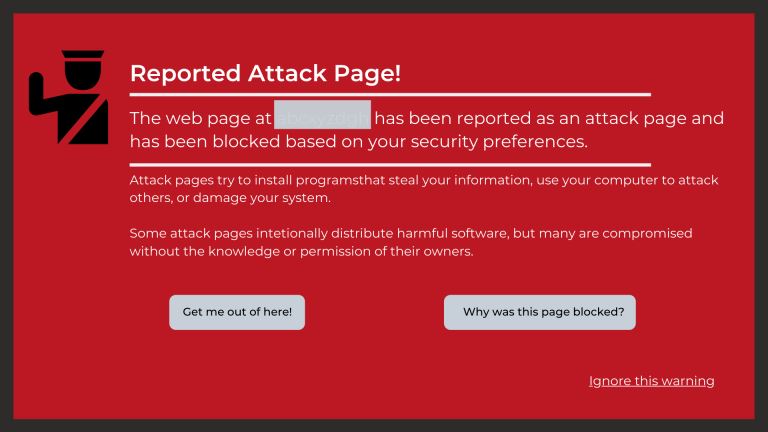
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
24
|
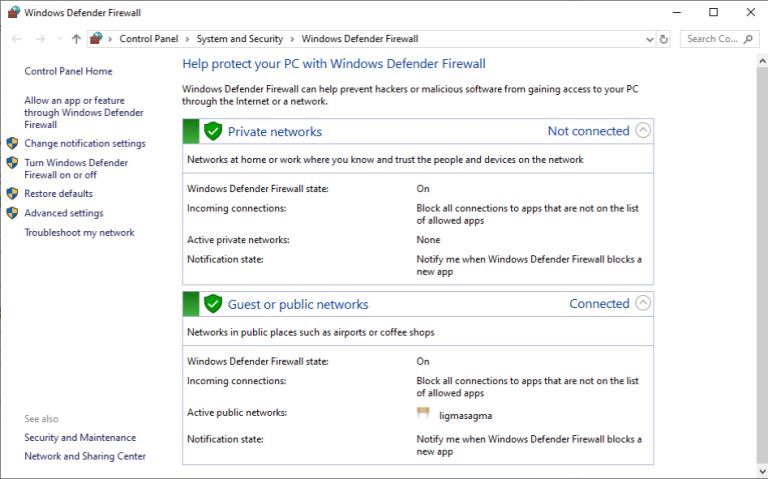
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|