|
1
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
2
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
3
|
Binary code VS ASCII [Understanding the Differences] |

|
This piece delves into the differences between binary and ASCII coding methodologies. If you're seeking information and a thorough examination of these coding techniques, your search has come to an end. I understand the confusion that comes with comp...
Author: Newton Waweru |
|
|
|
|
4
|
The Top 5 Best Drawing and Animation laptops Under 1000 Dollars |

|
The Top 5 Best Drawing and Animation laptops Under 1000 Dollars
When choosing the best drawing and animation laptop, there are crucial factors to consider for effective work results. These activities are intensive and require a computer with a quick...
Author: James Fleming |
|
|
|
|
5
|
What Are The Precautions To Consider When Backing Up Your Data? |

|
Did you know that backing up your data is essential to protect yourself from losing critical files? Backing up your data means making copies of your data and storing them in a safe place.
There are many ways to back up your data, and your best metho...
Author: Faith Cheruiyot |
|
|
|
|
6
|
10 Undeniable Benefits of Remote Assistance |

|
Advancements in technology have led to several changes in how we live and work. One of the most significant changes has been the rise of remote working. With the ability to connect to the internet from anywhere in the world, more and more people are ...
Author: Faith Cheruiyot |
|
|
|
|
7
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
8
|
Why is NETFLIX Download Slow On iPhone & Android? |

|
Netflix has been the most popular video streaming application all over the globe. Since its inception, it has grown massively and attracted millions of viewers. Not only it allows you to stream a video but also to download it. But what if the downloa...
Author: Tithi Raha |
|
|
|
|
9
|
How To Incorporate Theater Elements for a Better Experience |

|
Did you know that theater services can help to improve your experience? There are many reasons why theater is so popular, but one of the main reasons is that it offers an immersive experience that you can rarely find anywhere else.
There are various...
Author: Faith Cheruiyot |
|
|
|
|
10
|
Things You Didn't Know About Backup Services [What Are They?] |

|
A good backup service is crucial for ensuring all your data is safe from hardware failure or accidental deletion. Backup services offer companies and individuals the protection they need to keep their data safe. With backup services, companies can co...
Author: Faith Cheruiyot |
|
|
|
|
11
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
12
|
Is the Thunderbolt 3 the same as the USB-C? |

|
The Thunderbolt 3 and USB Type C are two distinct technologies that are also quite closely related. These two devices are indistinguishable from the bare eyes except for their logos. However, there are more distinctive features when we examine their ...
Author: |
|
|
|
|
13
|
How computers work: why is the processor important? |

|
We have prepared this article with the sole aim of informing you what a processor is, it's components and how they function together in transforming data and instructions into useful information.
,
A CPU or processor is an electronic circuit found ...
Author: Gloria Mutuku |
|
|
|
|
14
|
How to repair windows 10 automatic repair loop? |

|
An automatic repair loop in Windows 10 appears when you try to boot your computer but can’t and having an endless circle to try repair itself. If Windows 10 can’t repair itself, it will reboot and continues with the same circle.
This can be not ver...
Author: Berts Njoroge |
|
|
|
|
15
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
16
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
17
|
How Do Search Engines Work? |

|
You’re in the kitchen making your mom’s favorite pizza. To get topping ideas, you open your web browser to perform a search. You type ‘topping ideas’ in the search box, hit ‘Enter,’ and get eighty-nine million results in about half a second. For th...
Author: Ian Musyoka |
|
|
|
|
18
|
How does Chromecast work technically? |

|
Chromecast is a small disc-shaped device from Google that plugs into the High-Definition Multimedia Interface (HDMI) port of your television. It streams content through the Wi-Fi connection of your mobile device or computer, from streaming services s...
Author: Ujunwa Chibuzor |
|
|
|
|
19
|
How to edit a PDF without Adobe? |

|
Adobe launched the PDF file format in the 90s. At the moment, it’s the most popular format to exchange and send documents in the world. For example, major documents such as CAD drawings, presentations, legal documents, government forms, and invoices ...
Author: Berts Njoroge |
|
|
|
|
20
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
21
|
How to stop a computer from overheating when playing games? |

|
As an avid gamer, you've probably spent thousands of dollars on a high-end gaming rig. So imagine your disappointment when your Desktop PC freezes or even shuts down abruptly mid-game.
The culprit here is most likely to be overheating. While modern ...
Author: Ujunwa Chibuzor |
|
|
|
|
22
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
23
|
How to Take a Screenshot on a Widows Computer |
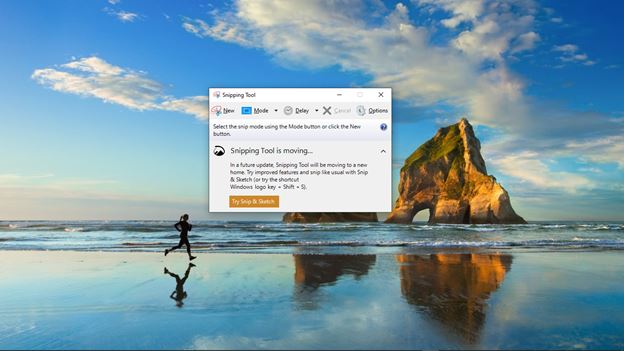
|
Taking screenshots has been a common necessity in recent years; it offers device users a unique way of sharing specific information on their screens. Screenshots have particularly been popular among mobile phone users; however, computer users may occ...
Author: Collins Okoth |
|
|
|
|
24
|
Pros and Cons of Overclocking RAM |

|
Have you ever heard of the term overclocking? Well, if not, I am sure you can take a good guess at what it means. Overclocking can be defined as the act of resetting your computer's Memory or central processing unit (CPU) to operate at a much higher ...
Author: Collins Okoth |
|
|
|
|
25
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
26
|
What Is an On-board Video Chipset |

|
A chipset refers to a complex set of components in an integrated circuit. A chipset's main purpose is to manage data flow sequentially between the processor, memory, and all other computer components. Normally, all chipsets are mounted on the motherb...
Author: Collins Okoth |
|
|
|
|
27
|
What Is a VPN? |
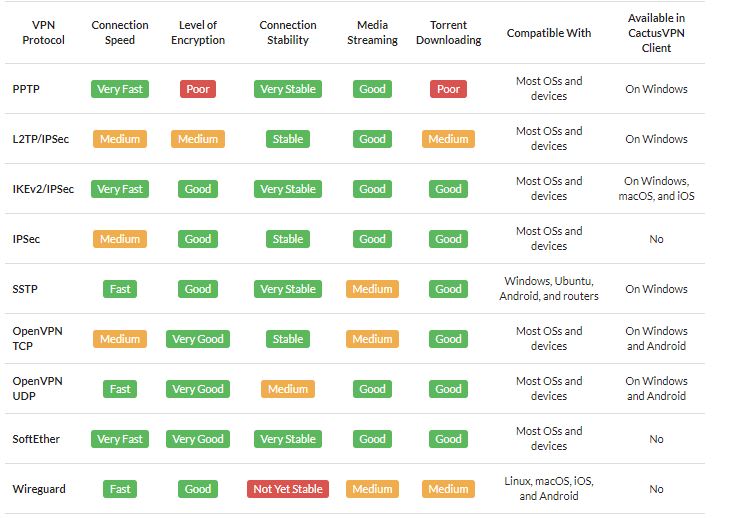
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|
|
28
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|
|
29
|
Optimizing RAM with Multi-Channel Support |

|
Nearly all computing devices require working memory to function properly. Take a look at your favorite device. Whether it's your TV, smartphone, or perhaps even your calculator, chances are it has its own memory module to store temporary data. Your c...
Author: Emman Jemuel |
|
|
|
|
30
|
What Is USB 3.0 |

|
USB is short for Universal Serial Bus. A USB is a plug-and-play interface that enables a computer to interact or communicate with other devices (Peripheral devices). There exists a wide range of USB-connected devices such as mice, keyboards, flash d...
Author: Collins Okoth |
|
|
|
|
31
|
What Is a Computer Hard Drive Used For? |

|
Have you ever turned on your computer only to see a black screen talking about “Imminent hard disk failure”? Maybe you suddenly drop your computer on the floor, then the screen goes black and refuses to turn back on again? If the screen is not the is...
Author: Cate Greff |
|
|
|
|
32
|
What Is Form Factor on A Motherboard? |
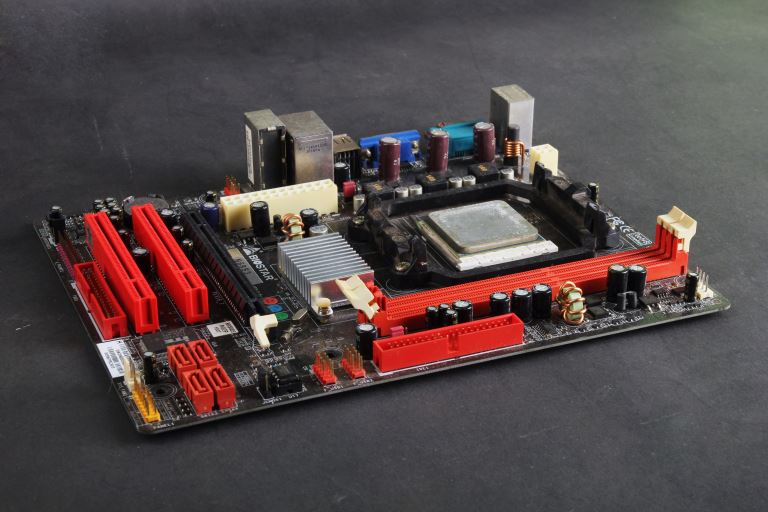
|
When talking about computers, the term 'motherboard' is highly likely to pop up on more than one occasion because it is vital. The primary function of the motherboard is to hold the microprocessor chip and give other parts the ability to connect to t...
Author: Delilah Daut |
|
|
|
|
33
|
How Do Computer Hard Drive Works |

|
A reliable and high-performance hard drive is essential. How? It acts as storage for your documents, videos, music, and more. Not only that. It also allows you to run your operating system, games, and other applications fast.
What you need to know i...
Author: James Fleming |
|
|
|