|
1
|
What are the Challenges Faced in Cybersecurity Risks and Solutions |

|
Cybersecurity is a growing concern, and navigating its challenges can be daunting. You're not alone in seeking help; I'm here to provide the guidance you need. This article dives into the key obstacles faced in cybersecurity, offering practical insig...
Author: Newton Waweru |
|
|
|
|
2
|
How Does Malware Work Malware Definition Types and Protection |

|
I understand how troubling it can be to deal with the mysteries of cyber threats like malware. Fear not, as I've delved into the subject to help simplify it for you. In this article, we'll untangle the intricacies of malware, how it works, and its im...
Author: Newton Waweru |
|
|
|
|
3
|
What are the Types of Cyber Security Types and Threats Defined |

|
Navigating the complex world of cyber security can be challenging, and we understand that. This article is a comprehensive exploration of the various types of cyber security, carefully crafted to equip you with the knowledge to secure your digital li...
Author: Newton Waweru |
|
|
|
|
4
|
The Range and Scope of Internet Ethics A Comprehensive Guide |

|
Diving into the complex world of Internet Ethics? You're not alone! I've explored the range and scope of this topic to help you navigate these ethical dilemmas. This article will provide insights and guidance, ensuring you make informed decisions onl...
Author: Newton Waweru |
|
|
|
|
5
|
What are the 3 Main Pillars of Cybersecurity Internet Safety |

|
I understand cybersecurity can be complex and daunting, but don't worry - I'm here to help. As someone who has researched this topic extensively, I'll share the three main pillars of cybersecurity clearly and concisely, ensuring you gain a solid unde...
Author: Newton Waweru |
|
|
|
|
6
|
What are the 10 Commandments of Computer Ethics |

|
Navigating the digital world with respect and integrity is essential. As an expert in computer ethics, I've delved into the 10 Commandments of Computer Ethics, the cornerstone of responsible digital behavior. This article aims to help you better und...
Author: Newton Waweru |
|
|
|
|
7
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
8
|
What is the Importance of Internet Ethics Responsible Online Behavior |

|
Navigating the digital world, internet ethics is a vital topic you're not alone in exploring. I've got you covered. I empathize with your quest for guidance, and in this article, I'll discuss the importance of ethical conduct online, privacy, and sec...
Author: Newton Waweru |
|
|
|
|
9
|
How Can you Defend Yourself Against a Ransomware Attack |

|
Facing ransomware attacks can be terrifying, and we understand the anxiety it brings. Don't worry; I am here to help you defend yourself effectively. As someone who has delved into this issue, I've got your back. This article will provide actionable ...
Author: Newton Waweru |
|
|
|
|
10
|
How is Identity Theft Committed Technology |

|
Navigating the complex world of identity theft and technology can be daunting. Rest assured, I've thoroughly explored this landscape, and I'm here to guide you. This article unpacks how criminals exploit technology to commit identity theft, ensuring ...
Author: Newton Waweru |
|
|
|
|
11
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
12
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
13
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
14
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
15
|
Why Should You Hire a Qualified Computer Repair Technician |

|
When you run into an issue with your computer system, it's of utmost importance that you avoid the temptation of handling the situation all by yourself, especially without technical knowledge and education. Also, you should avoid handing over the iss...
Author: Tithi Raha |
|
|
|
|
16
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
17
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
18
|
What To Be Amazing At Monitor Screen Repair? Here's How |

|
Are you interested in getting into the monitor screen repair business? It's a great way to make some extra money and help people when needed. But how do you become amazing at screen repair?
There are a few tips to get you started: First, practice m...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
20
|
What Is about:blank, and How Do You Remove It? |

|
What Is about:blank, and How Do You Remove It?. As one uses about:blank together with address bar web browser, you will get to view the empty page that has been built with the aid of a web browser. They entail part of Internet Explorer, Microsoft Edg...
Author: James Fleming |
|
|
|
|
21
|
The 10 Best Web Browsers for Windows in 2022 |

|
Today's web is a constantly moving target, and the web browsers we use to navigate it have changed. Browsers come and go pretty regularly, and each new release typically brings a host of new and exciting features that set it apart from its predecesso...
Author: James Fleming |
|
|
|
|
22
|
Computer Repair: How to Detect Crypto Mining Malware |

|
The vast growth of the cryptocurrency market has been something to marvel at over the past few years. However, the concept of anonymous payouts has given cybercriminals a reason to be part of the game. They have developed crypto-mining malware that c...
Author: Ian Musyoka |
|
|
|
|
23
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
24
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
25
|
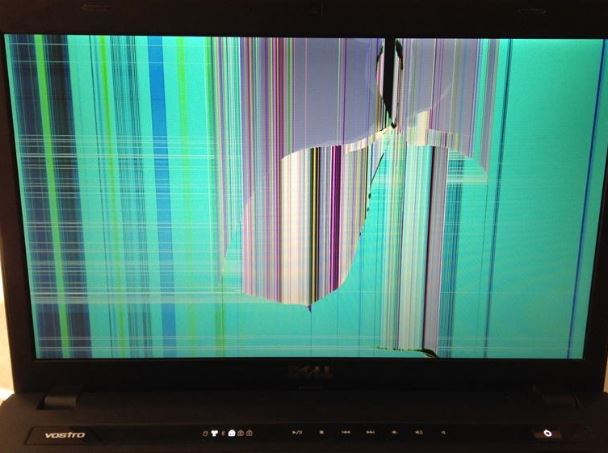
How To Replace a Broken Laptop Screen |
|
A laptop screen is a delicate part of a computer. Having a broken laptop screen can be catastrophic to the user. Any operation that's taking place in the computer system is not going to be visible. Regardless of whether you are amazingly cautious wit...
Author: Delilah Daut |
|
|
|