|
1
|
Can Computer Repair Shops Steal Your Data How to Prevent Them |

|
Regardless of the type of laptop or computer you use, it'll cause you some trouble at some point. Because technical issues may arise with your devices. In that case, you have to take your system to a repair shop for further help. But, a lot of people...
Author: Tithi Raha |
|
|
|
|
2
|
Can Computer Technicians Check Your History How to Prevent It |

|
It's pretty common that occasionally you may run into issues with your computer system. It may break down, malfunction, or be a victim of a ransomware attack. Regardless of the reasons, you're bound to call a repair technician. But, a lot of you doub...
Author: Tithi Raha |
|
|
|
|
3
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
4
|
How to Detect Hidden Surveillance Cameras With Your Phone |

|
How to Detect Hidden Surveillance Cameras With Your Phone
Have you ever suspected that you were being watched but couldn't find any visible surveillance cameras? It's possible that the camera or cameras were hidden, making it difficult to detect the...
Author: James Fleming |
|
|
|
|
5
|
How to Find Your Location History on iPhone or iPad |

|
How to Find Your Location History on iPhone or iPad
Nowadays, every smartphone user is tracking their location and movement. Apple records all your activities, so it's easy to find a record of your past location history. You may wonder how to view y...
Author: James Fleming |
|
|
|
|
6
|
Bluetooth 5 and Its Benefits: Why You Should Care |
|
Bluetooth 5 and Its Benefits: Why You Should Care
Bluetooth 5 is the evolution of the technology that updates and upgrades the previous Bluetooth 4.2 edition. It's not the most recent upgrade, but it's still good and offers multiple benefits over it...
Author: James Fleming |
|
|
|
|
7
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
8
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
9
|
The Easiest Way to Copy Text Messages from One Android Device to Another |

|
The Easiest Way to Copy Text Messages from One Android Device to Another
It's natural to question whether and how text messages may be transferred from one Android smartphone to another in case of a device swap. It takes a few minutes to copy your t...
Author: James Fleming |
|
|
|
|
10
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
11
|
Why is NETFLIX Download Slow On iPhone & Android? |

|
Netflix has been the most popular video streaming application all over the globe. Since its inception, it has grown massively and attracted millions of viewers. Not only it allows you to stream a video but also to download it. But what if the downloa...
Author: Tithi Raha |
|
|
|
|
12
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
13
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
14
|
How to Disable Notifications on Windows 10 |

|
Notifications popping up any time you are using your PC can be a nagging experience— they hurt your concentration adversely. However, there are ways and tricks you can disable computer notifications on windows 10. This article covers that and more.
...
Author: Fay Kokri |
|
|
|
|
15
|
What Is a Burner Phone, and When Should You Use One |

|
I have been wondering how a burner phone can be used or if it is necessary to have one. I am sure I'm not the only one with such questions, so I did my research and wrote this article on burner phones and in which instances they can be helpful to bot...
Author: Janet Kathalu |
|
|
|
|
16
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
17
|
How to Use Google Docs: The Beginner's Guide to Google Docs |

|
The old way of storing documents on a hard disk is a thing of the past. The cloud-based solution is the new way to handle files. Google Docs is one of the best ways to create, edit and share word documents. You don't have to carry storage devices to ...
Author: Faith Cheruiyot |
|
|
|
|
18
|
How to create an invisible folder on your Windows 10 Computer |

|
How to create an invisible folder on your Windows 10 Computer
Do you have questions on how to create a hidden folder on your Windows 10 computer? Worry no more. With this informative piece, we will be sharing with you a step-by-step guide on this. F...
Author: Gloria Mutuku |
|
|
|
|
19
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
20
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
21
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
22
|
How Do Search Engines Work? |

|
You’re in the kitchen making your mom’s favorite pizza. To get topping ideas, you open your web browser to perform a search. You type ‘topping ideas’ in the search box, hit ‘Enter,’ and get eighty-nine million results in about half a second. For th...
Author: Ian Musyoka |
|
|
|
|
23
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
24
|
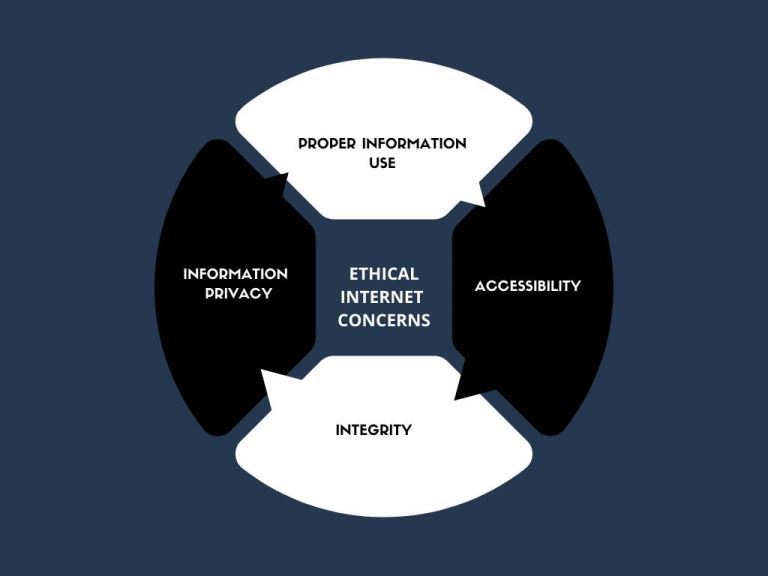
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
25
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
26
|
The Top 10 Browsers for Windows |

|
The internet is a significant part of our daily life today. However, to access it, we need special software tools. Web or Internet browsers are special software programs that have been specifically developed to allow computer users to access the inte...
Author: Collins Okoth |
|
|
|
|
27
|
I Can't Open Email Attachments |

|
Email attachments are the files you receive alongside your email messages. The files come in different formats. The most common and widely used are the .pdf, .doc, .zip, or .html.
There are various other forms, and each requires specific computer p...
Author: Eunice Njuguna |
|
|
|
|
28
|
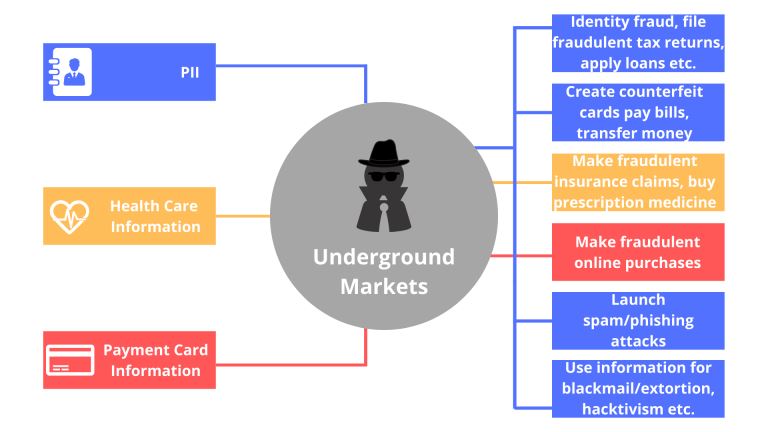
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
29
|
How do Wi-Fi Hotspots Work |

|
A hotspot can be described as a locale or area that has an accessible wireless network. Wi-Fi hotspot is commonly used to refer to the available wireless connections in public places such as airports, restaurants, and coffee shops. Depending on your ...
Author: Collins Okoth |
|
|
|
|
30
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
31
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
32
|
How to Get Rid of Computer Pop-Ups |

|
If you have had the chance to encounter pop-ups when working with your computer, you understand how frustrating and irritating it can get. They will slow down your device and even create a gateway for other malware to infect your computer. No compute...
Author: Cate Greff |
|
|
|
|
33
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|
|
34
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|
|
35
|
How To Wipe a Computer Hard Drive |

|
How safe would you feel to discover your bank account info, old emails, and browser history are accessible to someone else? Of course, it could be the recent buyer of your computer, but still, personal information is not safe unless you or someone yo...
Author: Eunice Njuguna |
|
|
|