|
1
|
How To Protect Children from Predators and Online Grooming |

|
As a caring parent, guardian, or educator, ensuring children's safety, especially from online predators and grooming, is a pressing concern. We understand your worries, and you're not alone. In this article, we're exploring key strategies to protect ...
Author: Newton Waweru |
|
|
|
|
2
|
Methods You Can Use to Protect Yourself from Social Engineering |

|
With the digital world evolving, the risk of social engineering has become a concern for many. Leveraging our expertise, we can arm you with methods to protect yourself against social engineering threats. This article will detail effective strategies...
Author: Newton Waweru |
|
|
|
|
3
|
How to Protect Yourself from Cyberstalking Stay Safe Online |

|
Are you concerned about cyberstalking and your online safety? You're not alone. As an individual who delved into this issue, I empathize with your worries. In this article, I'll discuss practical steps to protect yourself from cyberstalking, so you c...
Author: Newton Waweru |
|
|
|
|
4
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
5
|
What Are Your Strategies To Avoid Being A Victim Of Cybercrime? |

|
Cybercrimes have been on the increase, with many unaware victims. When we hear about cybercrimes, we automatically think about hackers. But cybercrime is not just about hacking. It goes beyond that. Many people today use their devices, such as phones...
Author: James Fleming |
|
|
|
|
6
|
What is the best way to use cloud storage? |

|
Cloud storage is a data storage service sought by individuals and businesses. If you have large volumes of data that you are concerned about its safety and wish to retrieve whenever needed, cloud storage would be the best option for you. Are you new ...
Author: Gloria Mutuku |
|
|
|
|
7
|
What Is End-to-End Encryption in Messenger? |

|
Messenger has brought about a lot of privacy and safety tools in the past year. Some of these are app locks, disappearing messages, privacy settings, and message forwarding limits. However, the end-to-end encryption feature is still being worked on. ...
Author: Collins Okoth |
|
|
|
|
8
|
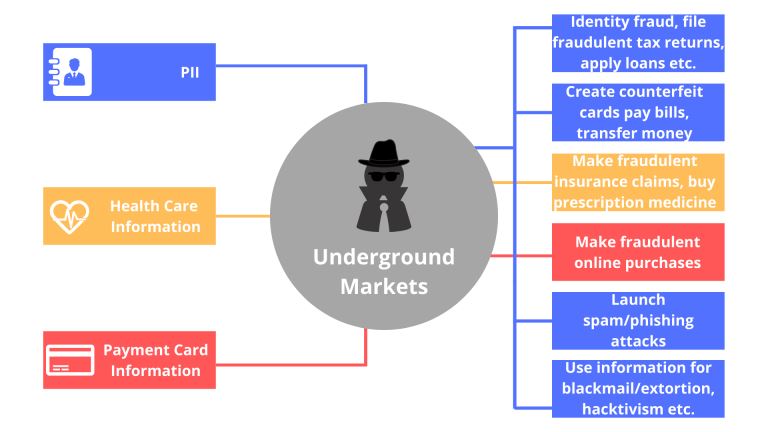
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|