|
1
|
The Range and Scope of Internet Ethics A Comprehensive Guide |

|
Diving into the complex world of Internet Ethics? You're not alone! I've explored the range and scope of this topic to help you navigate these ethical dilemmas. This article will provide insights and guidance, ensuring you make informed decisions onl...
Author: Newton Waweru |
|
|
|
|
2
|
What are the 10 Commandments of Computer Ethics |

|
Navigating the digital world with respect and integrity is essential. As an expert in computer ethics, I've delved into the 10 Commandments of Computer Ethics, the cornerstone of responsible digital behavior. This article aims to help you better und...
Author: Newton Waweru |
|
|
|
|
3
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
4
|
What is the Importance of Internet Ethics Responsible Online Behavior |

|
Navigating the digital world, internet ethics is a vital topic you're not alone in exploring. I've got you covered. I empathize with your quest for guidance, and in this article, I'll discuss the importance of ethical conduct online, privacy, and sec...
Author: Newton Waweru |
|
|
|
|
5
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
6
|
The Danger of Mixing Cyberwarfare with Cyber Espionage |

|
Are you concerned about the potential hazards of combining cyber warfare and cyber espionage? You're not alone. As someone who has delved deep into this critical issue, I understand your concerns and am here to help. This article will explore the ris...
Author: Newton Waweru |
|
|
|
|
7
|
How Can an Intrusion Detection System Protect Your Company |

|
Concerned about your company's cybersecurity? An Intrusion Detection System (IDS) might be your perfect solution. I understand how critical it is to protect sensitive data, and I've delved into the topic to provide the guidance you need.
An intrusi...
Author: Newton Waweru |
|
|
|
|
8
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
9
|
How do I remove write protection from my SanDisk? |

|
How do I remove write protection from my SanDisk?
While working on computers using external storage devices, they may be write-protected, which means that no operation can be done on them. A write-protected disk only allows the user to read data fro...
Author: James Fleming |
|
|
|
|
10
|
Essential Tips for Smart Home From Experts |

|
In the market for a new home? You might be considering buying a smart home. While there are many benefits to owning one of these homes, there are also some things to keep in mind.
There are essential tips from experts that can help you make the most...
Author: Faith Cheruiyot |
|
|
|
|
11
|
What Is An Example of Smart Home Automation? |

|
When it comes to the future of the home, many people think of smart homes. A smart home is a residence equipped with advanced automation features, making it more intelligent and efficient.
There are many different types of smart home automation, so...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Smart Security System: Protecting Your Home From Burglars |

|
Like most people, you probably think of your home as your sanctuary. It's where you feel safe and secure, and it's a refuge from the hustle and bustle of the outside world. But what happens when a burglary shatters that sense of safety? A smart secur...
Author: Faith Cheruiyot |
|
|
|
|
13
|
How to Fix a Trackpad Problem on a Macbook, iMac, or MacBook Pro |

|
We use the trackpad to interact with different parts of the graphical user interface. They help in improving accessibility where there are no keyboard shortcuts. When it faces challenges, many users will feel useless as they like interacting with the...
Author: Faith Cheruiyot |
|
|
|
|
14
|
What Are The Modern Rules of In-home Computer Service? |

|
In the olden days, if your computer crashed or stopped working, you had to take it in for servicing. But now, with so many people working remotely and relying on their computers, there are new rules for when and how you should get your computer servi...
Author: Faith Cheruiyot |
|
|
|
|
15
|
How to Recover Deleted Files from Hard Drive |

|
Do you want to recover some deleted files from your hard drive, or do you want to start a data recovery business? When you want to restore data from a hard drive, it's not that hard. You need to follow several steps after knowing the cause of the dat...
Author: Faith Cheruiyot |
|
|
|
|
16
|
What Are The Basic Rules to Design a Theater? |

|
Designing a theatre comes with its own set of unique challenges and considerations. From the size and shape of the space to the type of seating, there are many factors to consider when creating a theatre.
There are some basic rules in designing a th...
Author: Faith Cheruiyot |
|
|
|
|
17
|
What to do when CCTV cameras power supply stop working? |

|
It has been a major issue among people when it comes to how to handle CCTV cameras. The major puzzle is how to tell if the power supply is the issue and what to do, how to detect the problem, why you are getting uncolored pictures, why your footage a...
Author: Janet Kathalu |
|
|
|
|
18
|
Unlock PDF: How to Remove a Password From a PDF File |

|
The greatest frustration is when you want to access or print a PDF document, only to find out it has restrictions, and you are clueless about its original password. I am about to make you rest easy and enjoy removing the permission passwords from you...
Author: Fay Kokri |
|
|
|
|
19
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
20
|
What Are Ethical and Unethical Practices Related to Internet Use? |
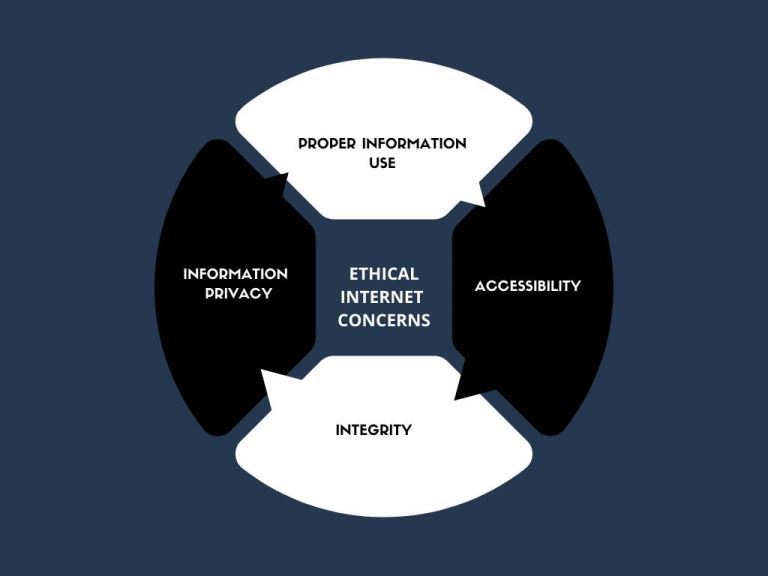
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
21
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
22
|
Do I Really Need To Care About My Privacy Online? |
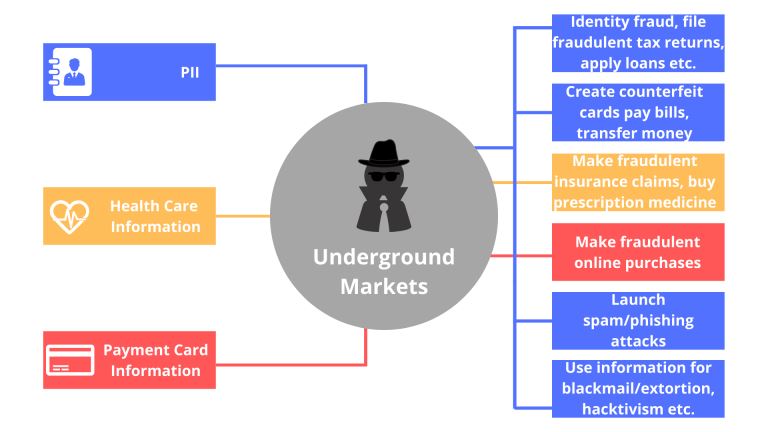
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|