|
1
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
2
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
3
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
4
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
5
|
Why Does My Download Slow on Xbox & How Do You Fix It? |

|
Are you waiting for hours just to finish a game download on your Xbox? Well, you're not the only one suffering from slow download speeds. There are thousands of people facing the same issue and there are countless reasons behind this. So, is there an...
Author: Tithi Raha |
|
|
|
|
6
|
How Do You Locate Someone's IP Address? 4 Ways to Apply! |

|
An IP address is a simple numeric address used for identifying unique devices in a network. You can easily find the IP address of your own, but there are times when you may need to locate someone's IP address. Maybe you want to blacklist them or you ...
Author: Tithi Raha |
|
|
|
|
7
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
8
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
9
|
Who are the Up-Coming Game Console Repair Bloggers You Need to Watch? |

|
If you are in the gaming console repair industry or an enthusiast, you must look up to people ahead of you. Upcoming console repair bloggers can be a great resource.
There are several upcoming game console repair bloggers you need to watch. For exa...
Author: Caroline Chebet |
|
|
|
|
10
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
11
|
How to Use Google Docs: The Beginner's Guide to Google Docs |

|
The old way of storing documents on a hard disk is a thing of the past. The cloud-based solution is the new way to handle files. Google Docs is one of the best ways to create, edit and share word documents. You don't have to carry storage devices to ...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Internet Connection: Why Is My Internet So Slow |

|
We all have experienced slow internet speeds in our homes. I will guide you on the best way you can speed up your home internet, how different factors affect your speeds, and getting the best internet plans for your home or office. I will also guide ...
Author: Faith Cheruiyot |
|
|
|
|
13
|
USB Type-C Explained: What is USB-C and Why You’ll Want it |

|
USBs, also known as (Universal Serial Bus), have existed for quite a while now. This technology has grown, extending its use cases to phones, computers, and laptops, replacing the mouse and keyboard PS/2 ports. Considering the history of this technol...
Author: Collins Okoth |
|
|
|
|
14
|
How to create an invisible folder on your Windows 10 Computer |

|
How to create an invisible folder on your Windows 10 Computer
Do you have questions on how to create a hidden folder on your Windows 10 computer? Worry no more. With this informative piece, we will be sharing with you a step-by-step guide on this. F...
Author: Gloria Mutuku |
|
|
|
|
15
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
16
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
17
|
How Do Search Engines Work? |

|
You’re in the kitchen making your mom’s favorite pizza. To get topping ideas, you open your web browser to perform a search. You type ‘topping ideas’ in the search box, hit ‘Enter,’ and get eighty-nine million results in about half a second. For th...
Author: Ian Musyoka |
|
|
|
|
18
|
How to Check If an Email Is Legit? |

|
“Phishing” is a popular term among hackers and hacking sites. These phishing emails are sent with the primary purpose of stealing valuable information or taking control of your networks.
It’s reported that every day nearly 3.4 billion phishing emai...
Author: Tithi Raha |
|
|
|
|
19
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
20
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
21
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
22
|
Which Windows Computer is Best? |

|
When you are in the market for a new computer, you will likely be debating whether to purchase a Mac or a Windows computer. However, this is not the end of the deliberating process; if you opt for a Windows computer, you will need to choose from a br...
Author: Collins Okoth |
|
|
|
|
23
|
How do Wi-Fi Hotspots Work |

|
A hotspot can be described as a locale or area that has an accessible wireless network. Wi-Fi hotspot is commonly used to refer to the available wireless connections in public places such as airports, restaurants, and coffee shops. Depending on your ...
Author: Collins Okoth |
|
|
|
|
24
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
25
|
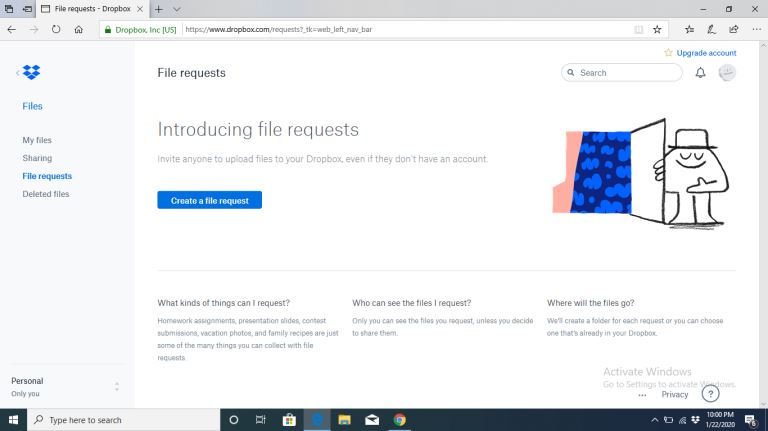
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
26
|
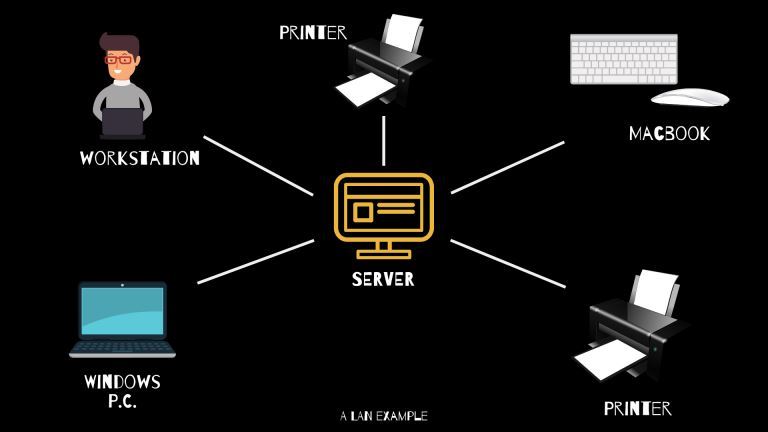
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
27
|
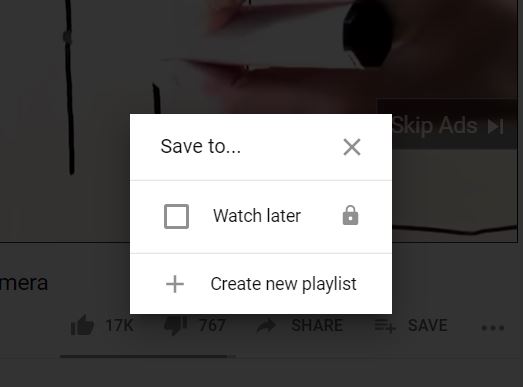
How Do I Download or Save a YouTube Video to My Computer? |
|
The YouTube design is such that users only get the chance to view the videos on their webpage. If you are the type of person who is always on the run or in situations with little or no internet connection, this might not be ideal for you. Many people...
Author: Delilah Daut |
|
|
|
|
28
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
29
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
30
|
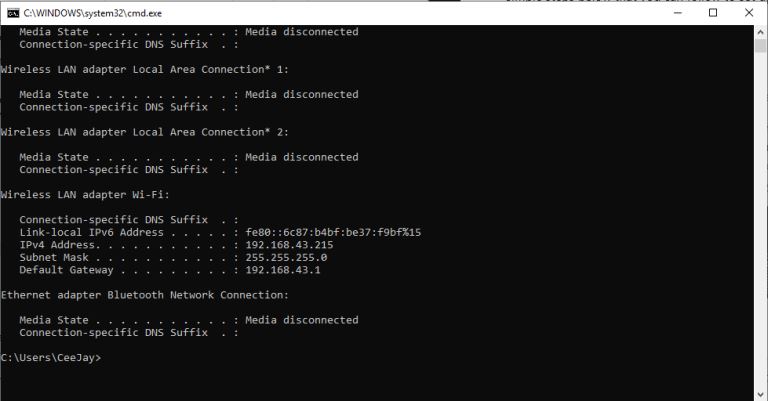
How Do I Find My IP Address |
|
The internet is a worldwide network of unrelated computers yet able to communicate successfully by following a specific set of rules. These rules are commonly known as protocols. A fundamental yet essential tenet of the internet is the Internet Proto...
Author: Collins Okoth |
|
|
|
|
31
|
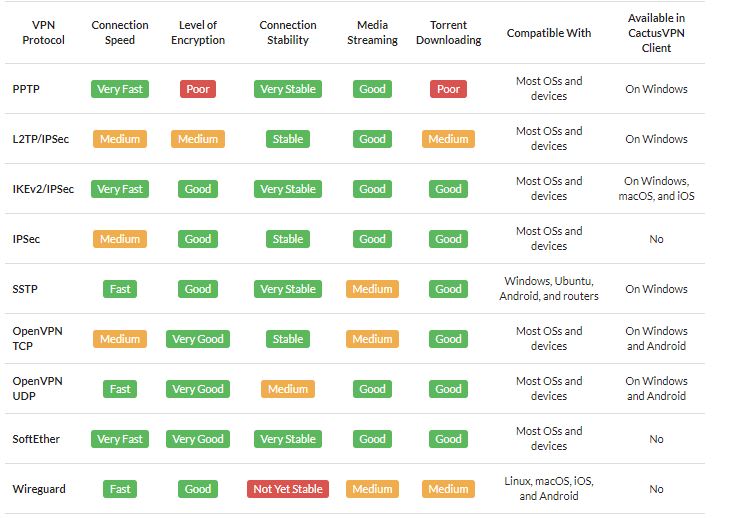
What Is a VPN? |
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|
|
32
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|
|
33
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|
|
34
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|
|
35
|
My Computer Won't Connect To the Internet but Others Will |

|
There's nothing more frustrating than when your device won't connect to the internet, and you don't know why, especially when others don't seem to have a problem! But before you give up and throw it out or spend hours on the phone with your ISP, take...
Author: Trey Williams |
|
|
|