|
1
|
How to force quit on a mac |

|
How to force quit on a mac
Have you ever felt like smashing your computer into a million pieces just because an app misbehaves and is not responsive? Well, I am sure we all have been there once or twice. Therefore, instead of bashing your expensive ...
Author: James Fleming |
|
|
|
|
2
|
How to Fix My Microphone Doesn’t Work on Windows 11 |

|
How to Fix My Microphone Doesn't Work on Windows 11
Have you ever been on a vital video call and encountered your microphone unexpectedly ceasing to work? It can be incredibly frustrating. Unfortunately, it's an all too common issue with Windows 11;...
Author: James Fleming |
|
|
|
|
3
|
Data Restore: What are the 3 data recovery options? |

|
Data recovery involves different phases. Do you need some help to get your data back, or do you want to know more about data recovery? The recovery options entail different types of backup deployed by the users. It is essential to determine how long ...
Author: Faith Cheruiyot |
|
|
|
|
4
|
What Are The Modern Rules of Backup Services? |

|
Did you know there are modern rules for backup services? Backing up data is vital to maintain computer function and avoid data loss.
There are many rules in the backup services, including always backing up your data, automating your backups, and con...
Author: Faith Cheruiyot |
|
|
|
|
5
|
10 Undeniable Benefits of Remote Assistance |

|
Advancements in technology have led to several changes in how we live and work. One of the most significant changes has been the rise of remote working. With the ability to connect to the internet from anywhere in the world, more and more people are ...
Author: Faith Cheruiyot |
|
|
|
|
6
|
How Real Network Setup Problems Are Solved |

|
Network setups are not always smooth as per the expectations many users have. You encounter several issues which one must know how to fix them. It affects the team, reducing its efficiency and productivity. One must learn how to handle those issues w...
Author: Faith Cheruiyot |
|
|
|
|
7
|
What is the Best Software for Making Video Tutorials? |

|
Are you planning to make video tutorials? Do you want to explain how your products and services function using the software? Video Tutorial software is ideal as it lets you edit, generate, manipulate and enhance videos. Such ensures the corporate and...
Author: Faith Cheruiyot |
|
|
|
|
8
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
9
|
What are the Tips to Create a Video Tutorial Quickly? |

|
Do you want to create quality, professional videos that can excite your audience? Are you wondering how you can create video tutorials quickly and easily? Tutorial videos are useful in teaching a process or giving procedural instructions. They allow ...
Author: Faith Cheruiyot |
|
|
|
|
10
|
What Are The Best Ways To Organize files on a New Computer? |

|
Did you just buy a computer and wonder how to organize your files? While it's not the most glamorous activity, organizing computer files is essential. They often build up without your knowledge until, one day, you turn on your computer to find a des...
Author: Caroline Chebet |
|
|
|
|
11
|
What Android Repair Experts/Technician Want You to Know |

|
When it comes to android repair, with many guides on social media, many people think it's a do-it-yourself task, forgetting they need expert services and advice. It would be great to learn more about android repair from an expert's perspective. This ...
Author: Nancy Museo |
|
|
|
|
12
|
What the Best Game Console Repair Pros Do (and You Should Too) |

|
Are you looking for things that game console repair experts do and wish you could? Here is a full guide to help you get more skills in the console repair industry.
As a whole, game console repair pros do things like cleaning, maintenance, and game c...
Author: Caroline Chebet |
|
|
|
|
13
|
How computers work: why is the processor important? |

|
We have prepared this article with the sole aim of informing you what a processor is, it's components and how they function together in transforming data and instructions into useful information.
,
A CPU or processor is an electronic circuit found ...
Author: Gloria Mutuku |
|
|
|
|
14
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
15
|
How to create an invisible folder on your Windows 10 Computer |

|
How to create an invisible folder on your Windows 10 Computer
Do you have questions on how to create a hidden folder on your Windows 10 computer? Worry no more. With this informative piece, we will be sharing with you a step-by-step guide on this. F...
Author: Gloria Mutuku |
|
|
|
|
16
|
Can You Get a Keylogger Just by Visiting a Website? |

|
Ever since malware and virus infections have started to increase at a rapid pace, the fear of getting a keylogger just by visiting a website is bothering many people. After all, a majority of internet users access a lot of websites on a daily basis. ...
Author: Tithi Raha |
|
|
|
|
17
|
Is my computer worth fixing? |

|
Constant computer breakdowns can be frustrating, and if you are a frequent visitor to the repair shop you might start thinking of buying a new computer. However, a computer technician can advise you on the condition of your machine and if it is likel...
Author: Gloria Mutuku |
|
|
|
|
18
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
19
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
20
|
How Do Search Engines Work? |

|
You’re in the kitchen making your mom’s favorite pizza. To get topping ideas, you open your web browser to perform a search. You type ‘topping ideas’ in the search box, hit ‘Enter,’ and get eighty-nine million results in about half a second. For th...
Author: Ian Musyoka |
|
|
|
|
21
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
22
|
The Top 10 Browsers for Windows |

|
The internet is a significant part of our daily life today. However, to access it, we need special software tools. Web or Internet browsers are special software programs that have been specifically developed to allow computer users to access the inte...
Author: Collins Okoth |
|
|
|
|
23
|
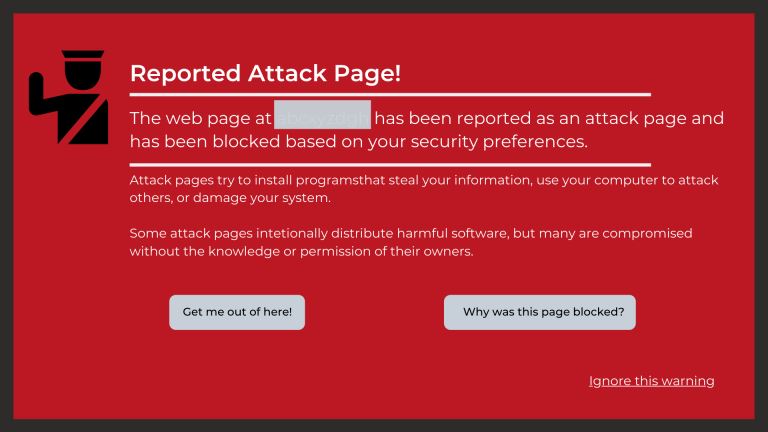
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
24
|
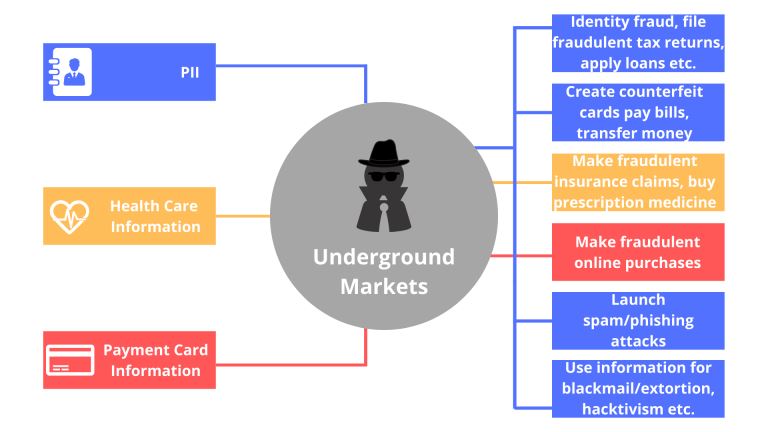
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
25
|
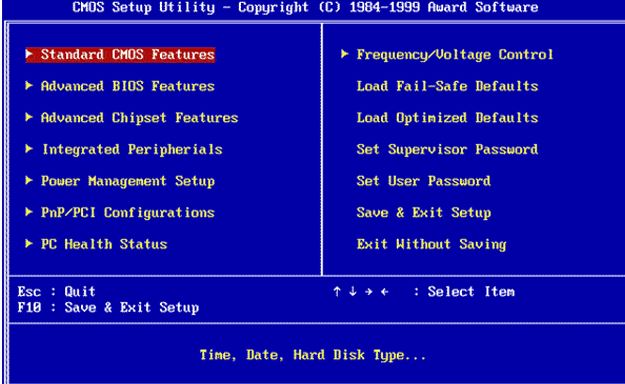
How to Enter the BIOS or the CMOS setup |
|
There is a long list of computing terms that have repeatedly confused novice computer users. Practically, the BIOS's confusion and the CMOS is one of the tops in this list. Unfortunately, I often hear people referring to the BIOS and CMOS interchange...
Author: Collins Okoth |
|
|
|
|
26
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
27
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
28
|
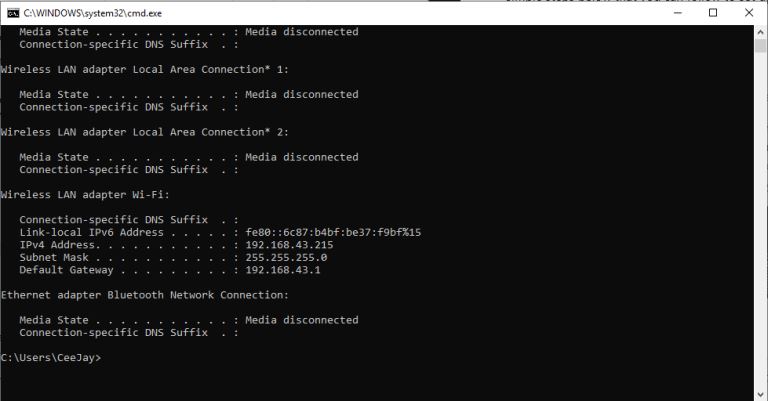
How Do I Find My IP Address |
|
The internet is a worldwide network of unrelated computers yet able to communicate successfully by following a specific set of rules. These rules are commonly known as protocols. A fundamental yet essential tenet of the internet is the Internet Proto...
Author: Collins Okoth |
|
|
|
|
29
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|
|
30
|
My Computer Can't Find the Hard Drive |
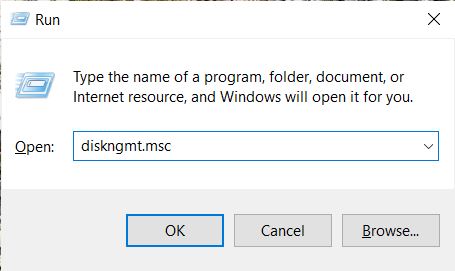
|
A common problem that occurs when operating a computer is the system not detecting a hard drive. It is a common occurrence related to the device not locating the default drive it uses to load in a new, old, internal, or external hard drive. For each ...
Author: Eunice Njuguna |
|
|
|
|
31
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|
|
32
|
Who Invented the Computer? |

|
Who invented the computer? It doesn't seem like such a complicated question. We know who invented the steam engine, the flushing toilet, and many other things that changed the world. Why then is it so difficult to determine who invented the computer?...
Author: Trey Williams |
|
|
|
|
33
|
What Is SATA 6GB/s |

|
The abbreviation SATA stands for Serial ATA (Advanced Technology Attachment), a modern generation drive interface preceded by the traditional wide and inconvenient Parallel ATA or PATA, also known as IDE. These technologies, PATA and SATA, describe t...
Author: Collins Okoth |
|
|
|
|
34
|
Why Do Computers use Binary Numbers? |

|
The binary numbering system is used in computing and electronics because it’s the simplest counting method available. In addition, the binary numbering system is used to code everything from memory to images on the screen. Thus, it is the basis for t...
Author: Trey Williams |
|
|
|
|
35
|
How Do You Take A Screenshot in Windows 10 |
|
A screenshot is a snapshot image of whatever is visible on your screen at a given moment. It’s great for sharing real-time information with technical support or saving information on the web that might be subject to change in the future.
Taking scre...
Author: Trey Williams |
|
|
|