|
1
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
2
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
3
|
What Are The Duties of a Computer Repair Technician in Topeka KS |

|
From diagnosing initial issues to finding a solution, a computer repair technician in Topeka or any other area is responsible for all phases of the entire repair process. Moreover, the primary duty of a repair technician is to leave your device funct...
Author: Tithi Raha |
|
|
|
|
4
|
Is it Cheaper to Repair or Replace a Computer |

|
It's certain that no computer will last forever. But, to yield the best benefits out of your investment, you would want to stretch the life out as long as possible. And, computer repairs can really help you stretch out the life of your devices. Yet, ...
Author: Tithi Raha |
|
|
|
|
5
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
6
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
7
|
How to Develop a Cloud Strategy | A step-by-step Guide |

|
When developing a cloud strategy, it's important to outline the best services and tools for a cloud solution. Your cloud strategy should include leveraging the company's IT capabilities with business needs that yield the most benefit from cloud compu...
Author: Eunice Njuguna |
|
|
|
|
8
|
A Guide on Converting an Image to JPG Format |

|
A Guide on Converting an Image to JPG Format
How do you convert an image to JPG format? What are the best ways to save your images for web use? This comprehensive guide will walk you through converting an image to JPG format and some essential tips ...
Author: James Fleming |
|
|
|
|
9
|
What Workloads Can be Moved to The Cloud? |

|
The migration of workloads involves the transfer of virtual machines, software, or databases to the cloud. The migration characterizes the selection of existing workloads, changing them, and deploying them to a cloud platform. Most businesses move wo...
Author: Eunice Njuguna |
|
|
|
|
10
|
Everything You Need to Know About (Dwm.exe) Desktop Window Manager |

|
Everything You Need to Know About (Dwm.exe) Desktop Window Manager
Introduction
What Is Desktop Window Manager (dwm.exe)? Desktop Window Manager or dwm.exe can be an integral part of Windows OS. These system processes are essential to controlling v...
Author: James Fleming |
|
|
|
|
11
|
How Can I Tell If Cloud Computing Is Right For My Company? |

|
Cloud computing is right for you if your company needs support with data storage, infrastructure scaling, big data analytics, networking, backup service strategies, and application development. A business looking to boost productivity, create room fo...
Author: Eunice Njuguna |
|
|
|
|
12
|
What is Cloud Computing? Everything You Need to Know |

|
Cloud computing covers IT resources delivered over the internet. It comes in various categories including concepts, variances, services, solutions, benefits, and IT infrastructure. Cloud computing typically covers application building, software devel...
Author: Eunice Njuguna |
|
|
|
|
13
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
14
|
Understanding the Service Host Process (svchost.exe) and Why there are Are Multiple Instances of Svc |

|
Service Host Process (svchost.exe) handles many essential functions in our computers, and serves an invaluable purpose in their correct operation. Without svchost.exe, computers would not be able to operate multiple services or programs at once or ...
Author: James Fleming |
|
|
|
|
15
|
Your Comprehensive Guide To The Top 8 Best Free Disk Formatting Utility to Format Hard Drive in Wind |

|
Your Comprehensive Guide To The Top 8 Best Free Disk Formatting Utility to Format Hard Drive in Wind
Are you having problems with your PC's hard drive? Does it seem like it's not performing as well as it used to? If so, you may need to format it.
F...
Author: James Fleming |
|
|
|
|
16
|
How to restore the Registry using Command Prompt in Windows 7, 8.1 10 and 11 |
|
How to restore the Registry using Command Prompt in Windows 7, 8.1 10 and 11
While using your PC, have you ever noted programs freezing or crashing without warning, your system running slowly, and your computer sometimes shutting down for no reason?...
Author: James Fleming |
|
|
|
|
17
|
How Can I Tell If I Need a New Router? Here Are The Signs! |

|
Wi-Fi router plays one of the most crucial roles when creating and sending out Wi-Fi signal across the home. Without having a seamless router, your devices such as your tablet, smartphone, or PC won't be connected to the wireless network setup. Altho...
Author: Tithi Raha |
|
|
|
|
18
|
Email Migration Tips: How Does Email Migration Work? |

|
Do you want to migrate your email from one host to another? In the email industry, migration can sometimes be risky and needs a lot of attention to avoid problems. Before starting, knowing what to expect from the email migration process will help you...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Things You Should Know Before Buying a Smart Home Device |

|
Do you want to be able to control your lights and appliances from your phone? Or maybe you're looking for a more efficient way to heat and cool your home. If so, then you may be considering purchasing a smart home device.
There are some things you s...
Author: Faith Cheruiyot |
|
|
|
|
20
|
Custom PC Build: What tools do I need to build my PC? |

|
Thinking about how to build your pc or hire someone? To build a personal computer, you do not need an expensive toolkit. It is simple and easy to get the tools since they are available in almost any computer store or online.
There are devices alread...
Author: Faith Cheruiyot |
|
|
|
|
21
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
22
|
What the Best Game Console Repair Pros Do (and You Should Too) |

|
Are you looking for things that game console repair experts do and wish you could? Here is a full guide to help you get more skills in the console repair industry.
As a whole, game console repair pros do things like cleaning, maintenance, and game c...
Author: Caroline Chebet |
|
|
|
|
23
|
What Is Overclocking? Beginner's Guide to Speeding up PCs |

|
Overclocking is essentially an act of manually increasing the clock speeds of the CPU, RAM, or GPU. It is common among computer geeks, IT professionals, and heavy computer users like Gamers interested in maximizing their processor's potential. To suc...
Author: Collins Okoth |
|
|
|
|
24
|
What Does Airplane Mode Do, and Is It Really Necessary? |

|
If you own a mobile phone or tablet, you are already familiar with the airplane mode feature. You are probably wondering what it is and if it is essential. This article will inform you all you need to know about airplane mode, why it is necessary to ...
Author: Gloria Mutuku |
|
|
|
|
25
|
Windows 10: How to login to Windows 10 without password? |

|
You won’t want to go through a password recovery process if you lose your password, which can be tiresome and hectic.
We will look at the best four poss
Use Microsoft website to set login preferences
Use advanced password managers- recommended...
Author: Fay Kokri |
|
|
|
|
26
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
27
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
28
|
A Detailed Guide to Removing Ransomware in Windows 10 |
|
One of the main problems faced by internet companies today is Ransomware. For this reason, cybersecurity has continued to grow as an industry in general. Unfortunately, players on both sides can easily be described as the bad guys and the good guys. ...
Author: Collins Okoth |
|
|
|
|
29
|
I Can't Open Email Attachments |

|
Email attachments are the files you receive alongside your email messages. The files come in different formats. The most common and widely used are the .pdf, .doc, .zip, or .html.
There are various other forms, and each requires specific computer p...
Author: Eunice Njuguna |
|
|
|
|
30
|
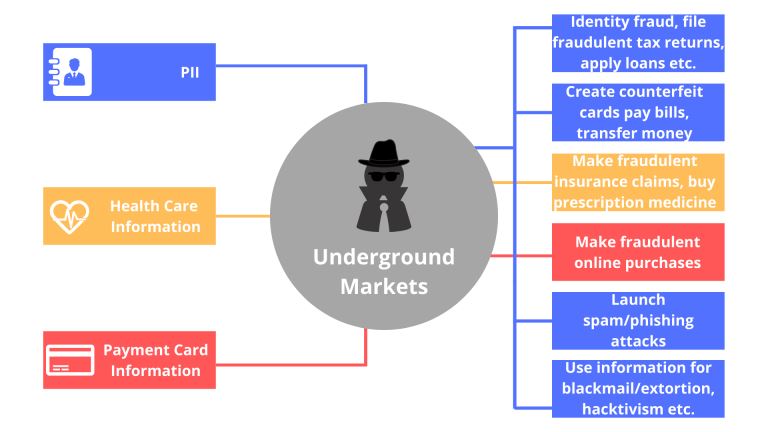
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
31
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
32
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|
|
33
|
How Do I Download or Save a YouTube Video to My Computer? |
|
The YouTube design is such that users only get the chance to view the videos on their webpage. If you are the type of person who is always on the run or in situations with little or no internet connection, this might not be ideal for you. Many people...
Author: Delilah Daut |
|
|
|
|
34
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
35
|
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|