|
1
|
How to Select The Best Computer Repair Shop in Topeka, KS |

|
When you're dealing with computer issues requiring a professional's help, it's essential to make sure that you choose the ideal Computer Repair in Topeka, Kansas, or any other area to avoid major damages or unfavorable situations. Hiring the wrong re...
Author: Tithi Raha |
|
|
|
|
2
|
Binary Code and Electronics Components “Logic Gates.” |

|
Uncover the mysteries of binary code and electronics components with this comprehensive guide to logic gates. If you're interested in learning about how binary code influences the functioning of electronic devices, you've come to the right place.
...
Author: Newton Waweru |
|
|
|
|
3
|
What Workloads Can be Moved to The Cloud? |

|
The migration of workloads involves the transfer of virtual machines, software, or databases to the cloud. The migration characterizes the selection of existing workloads, changing them, and deploying them to a cloud platform. Most businesses move wo...
Author: Eunice Njuguna |
|
|
|
|
4
|
How To Turn off Touch Screen on Ubuntu [Quick Guide] |

|
Ubuntu is a Linux-based operating system mostly used by software developers, cyber security researchers, and information technologists. They like it since you can modify its code and create other copies that meet your requirements. Despite all these ...
Author: Berts Njoroge |
|
|
|
|
5
|
Email Setup: How To Set Up a Mail Server On Windows or Mac OS X |

|
Do you want to send and receive emails with your windows or Mac OS X and connect to it using a smartphone or PC? This guide is for you.
There are several ways you can set up a mail server on Mac OS X. For example, you can use server setting prefere...
Author: Faith Cheruiyot |
|
|
|
|
6
|
Email Migration Tips: How Does Email Migration Work? |

|
Do you want to migrate your email from one host to another? In the email industry, migration can sometimes be risky and needs a lot of attention to avoid problems. Before starting, knowing what to expect from the email migration process will help you...
Author: Faith Cheruiyot |
|
|
|
|
7
|
Email Migration: How To Migrate From Gmail To Outlook |

|
Are you aspiring to migrate your Gmail account to Outlook or hire someone? To start, you should have basic knowledge of email migration and the basic rules and regulations governing the email industry.
There are several tips, rules, and regulations ...
Author: Faith Cheruiyot |
|
|
|
|
8
|
Email Migration: How To Move Emails From One Host To Another |

|
Want to migrate from one Host to another? Worry not, for there are a lot of easy steps to migrate from one Host to another. Before starting, you must understand the industry's fundamental principles and rules.
There are several reasons why email cli...
Author: Faith Cheruiyot |
|
|
|
|
9
|
What are the Different Types of Tutorials? |

|
Do you always think about where you can learn how to do something? Most people look for tutorials to help them how to do tasks. Watching these videos gives you a deeper understanding and techniques for doing things better. It could be, installing ele...
Author: Faith Cheruiyot |
|
|
|
|
10
|
What Are The Modern Rules of In-home Computer Service? |

|
In the olden days, if your computer crashed or stopped working, you had to take it in for servicing. But now, with so many people working remotely and relying on their computers, there are new rules for when and how you should get your computer servi...
Author: Faith Cheruiyot |
|
|
|
|
11
|
What if I don't see a part I want in the custom Pc Builder? |

|
Want to build your PC or hire someone? Worry less, for there are several ways to learn and build your PC in just a few days. Before you start, it could be wise to understand this industry's basics and principles.
There are rules that a custom PC bui...
Author: Faith Cheruiyot |
|
|
|
|
12
|
What Are The Modern Rules of Backup Services? |

|
Did you know there are modern rules for backup services? Backing up data is vital to maintain computer function and avoid data loss.
There are many rules in the backup services, including always backing up your data, automating your backups, and con...
Author: Faith Cheruiyot |
|
|
|
|
13
|
Custom PC Build: How hard is it to build a PC? |

|
Are you aspiring to build your PC or hire someone? Don't worry; it is never hard, and you only need the skills and assembling of parts. Before starting off, ensure you understand all the rules of assembling a PC to make it easier.
There are many way...
Author: Faith Cheruiyot |
|
|
|
|
14
|
Can You Log Into a WI-FI Network That Does Not Have Internet Access? |

|
Imagine you're working on an important project online that has a strict deadline, and all of a sudden, your internet connection goes off!! How would you feel? Well, we know, it can be one of the most frustrating things to deal with. But, the truth is...
Author: Tithi Raha |
|
|
|
|
15
|
What Are The Basic Rules to Design a Theater? |

|
Designing a theatre comes with its own set of unique challenges and considerations. From the size and shape of the space to the type of seating, there are many factors to consider when creating a theatre.
There are some basic rules in designing a th...
Author: Faith Cheruiyot |
|
|
|
|
16
|
How to Disable Notifications on Windows 10 |

|
Notifications popping up any time you are using your PC can be a nagging experience— they hurt your concentration adversely. However, there are ways and tricks you can disable computer notifications on windows 10. This article covers that and more.
...
Author: Fay Kokri |
|
|
|
|
17
|
How To Add Check Boxes to Word Documents: A Complete Guide |

|
Do you ever look at forms with checkboxes and wonder how they were added? I was in that situation too, and mine was complicated because I was making a questionnaire. I needed to insert checkboxes but didn't know how to do it. Either way, I had to do ...
Author: Janet Kathalu |
|
|
|
|
18
|
What are the backup best practices using the cloud? |

|
Have you ever imagined what you would do if you lost all your crucial data? Of course, you cant imagine. Well, there is only one way to be sure of data safety and longevity- data backup. And the best thing is; cloud backup is here to make it easy to ...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
20
|
What Does Airplane Mode Do, and Is It Really Necessary? |

|
If you own a mobile phone or tablet, you are already familiar with the airplane mode feature. You are probably wondering what it is and if it is essential. This article will inform you all you need to know about airplane mode, why it is necessary to ...
Author: Gloria Mutuku |
|
|
|
|
21
|
How do I get rid of low disk space in Windows 10? |

|
Low disk space warning appears on Windows operating system to warn the user that a specific location of the hard drive is low on storage space. This type of error is persistent and will keep reappearing until you work on it.
There are generally thre...
Author: |
|
|
|
|
22
|
How do I automatically print an email attachment? |

|
In the modern world, getting a reliable automated solution makes work easier and speeds up your workflow.
Have you been wondering how to print your email attachments automatically? In this article, we will guide you through several ways you can achi...
Author: Faith Cheruiyot |
|
|
|
|
23
|
How Do Search Engines Work? |

|
You’re in the kitchen making your mom’s favorite pizza. To get topping ideas, you open your web browser to perform a search. You type ‘topping ideas’ in the search box, hit ‘Enter,’ and get eighty-nine million results in about half a second. For th...
Author: Ian Musyoka |
|
|
|
|
24
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
25
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
26
|
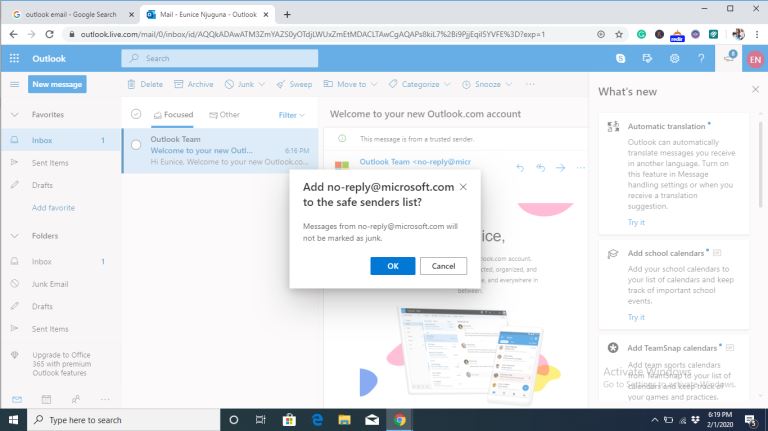
How Do I Stop Emails Going to Spam Folder |
|
Gmail, Yahoo, Hotmail, AOL, and Outlook are all excellent email services. They offer efficient email services by ensuring the proper delivery of emails to the inbox folder. But even with the efficiency in their services, there are negative issues tha...
Author: Eunice Njuguna |
|
|
|
|
27
|
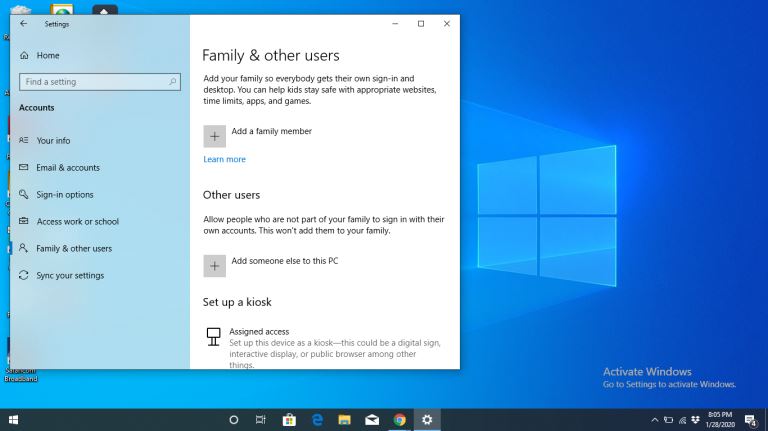
How Do I Set Up a New User on My Computer Windows 10 |
|
When installing Windows 10, the first account you create is an Administrator’s account. An administrator’s account has several privileges, and a common one is the ability to add new users to your computer.
There are several reasons an administrator...
Author: Eunice Njuguna |
|
|
|
|
28
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
29
|
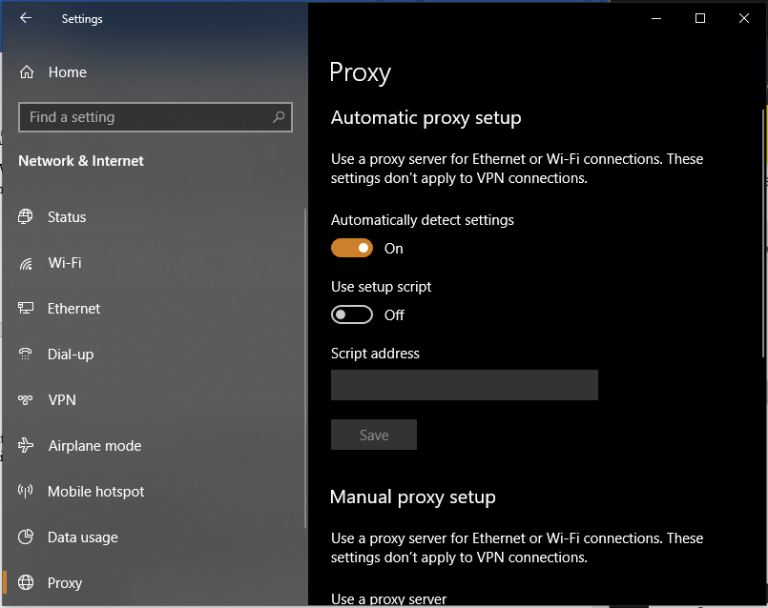
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
30
|
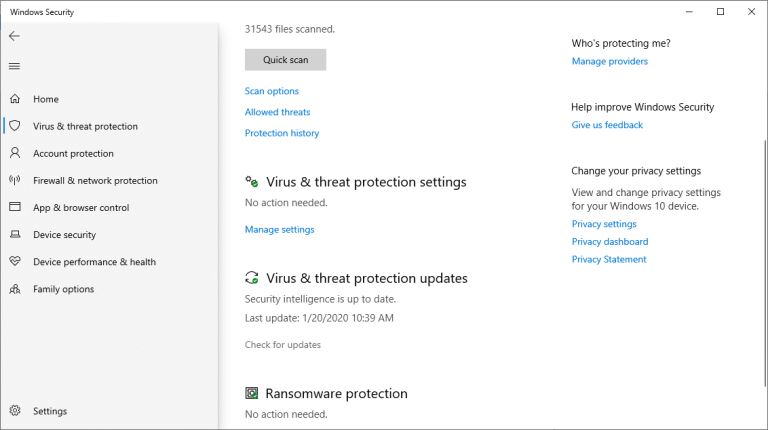
Sudden Computer Shutdown or Restart |
|
One of the most frustrating things you can experience as a computer user is a sudden shutdown or restart of the system. Not only could it lead to the loss of valuable work, but it may also be an indication that your PC is damaged. You may wonder what...
Author: Ian Musyoka |
|
|
|
|
31
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
32
|
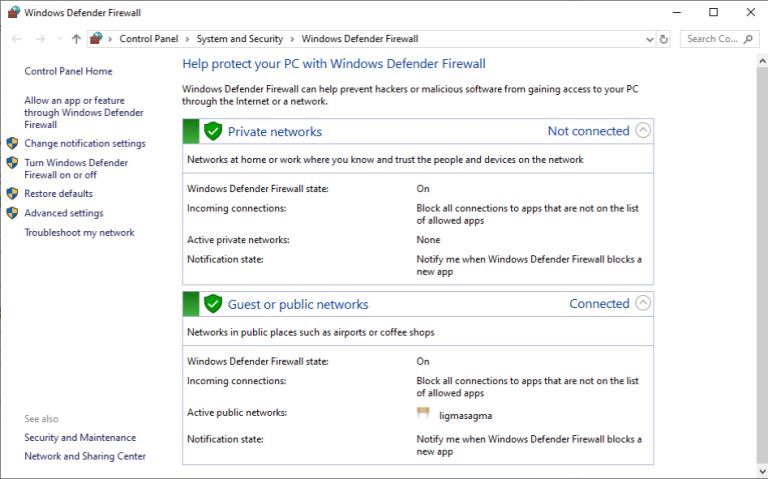
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
33
|
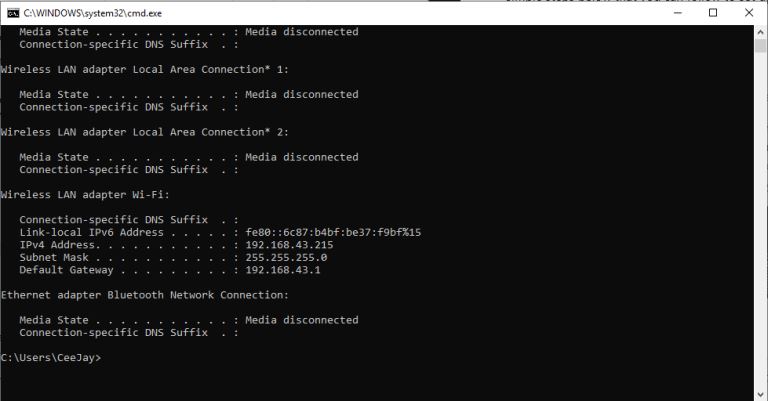
How Do I Find My IP Address |
|
The internet is a worldwide network of unrelated computers yet able to communicate successfully by following a specific set of rules. These rules are commonly known as protocols. A fundamental yet essential tenet of the internet is the Internet Proto...
Author: Collins Okoth |
|
|
|
|
34
|
Optimizing RAM with Multi-Channel Support |

|
Nearly all computing devices require working memory to function properly. Take a look at your favorite device. Whether it's your TV, smartphone, or perhaps even your calculator, chances are it has its own memory module to store temporary data. Your c...
Author: Emman Jemuel |
|
|
|
|
35
|
How To Clear Your Cache |

|
If you've ever struggled to access specific websites or failed to load an image on a webpage, no matter how many times you hit refresh, you've probably been advised to “clear your cache.” In fact, the only phrase more common in the world of IT and te...
Author: Trey Williams |
|
|
|