|
1
|
What are the 10 Commandments of Computer Ethics |

|
Navigating the digital world with respect and integrity is essential. As an expert in computer ethics, I've delved into the 10 Commandments of Computer Ethics, the cornerstone of responsible digital behavior. This article aims to help you better und...
Author: Newton Waweru |
|
|
|
|
2
|
Methods You Can Use to Protect Yourself from Social Engineering |

|
With the digital world evolving, the risk of social engineering has become a concern for many. Leveraging our expertise, we can arm you with methods to protect yourself against social engineering threats. This article will detail effective strategies...
Author: Newton Waweru |
|
|
|
|
3
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
4
|
Ways you Could Be Exposing Yourself to a Cybersecurity Attack |

|
Are you concerned about cybersecurity? You're not alone! As we increasingly rely on technology, protecting ourselves from cyber threats is crucial. I've researched this topic extensively, so I'm here to help. In this article, I'll explore ways you mi...
Author: Newton Waweru |
|
|
|
|
5
|
How Does Biometrics Change the Face of Security Enhancing Security |

|
Navigating the world of security can seem like a daunting task. With new technologies like biometrics rising, feeling curious and overwhelmed is normal. This article will guide you through how does biometrics change the face of security, providing in...
Author: Newton Waweru |
|
|
|
|
6
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
7
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
8
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
9
|
The Danger of Mixing Cyberwarfare with Cyber Espionage |

|
Are you concerned about the potential hazards of combining cyber warfare and cyber espionage? You're not alone. As someone who has delved deep into this critical issue, I understand your concerns and am here to help. This article will explore the ris...
Author: Newton Waweru |
|
|
|
|
10
|
Types of Intrusion Detection Systems Host and Network |

|
You've come to the right place to learn about the various types of Intrusion Detection Systems (IDS). This article will provide a comprehensive overview of the different IDS types, ensuring you're well-equipped to make an informed decision.
In total...
Author: Newton Waweru |
|
|
|
|
11
|
How Can an Intrusion Detection System Protect Your Company |

|
Concerned about your company's cybersecurity? An Intrusion Detection System (IDS) might be your perfect solution. I understand how critical it is to protect sensitive data, and I've delved into the topic to provide the guidance you need.
An intrusi...
Author: Newton Waweru |
|
|
|
|
12
|
How to Protect Yourself from Cyberstalking Stay Safe Online |

|
Are you concerned about cyberstalking and your online safety? You're not alone. As an individual who delved into this issue, I empathize with your worries. In this article, I'll discuss practical steps to protect yourself from cyberstalking, so you c...
Author: Newton Waweru |
|
|
|
|
13
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
14
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
15
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
16
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
17
|
The Next Big Thing in Cyber Security Discover Innovative Solutions |

|
Ready to uncover the Next Big Thing in Cyber Security? You're not alone! As cyber threats evolve, so should our defenses. Fear not, I've delved deep into this crucial issue to help you stay informed and prepared. Join me in this article as we explore...
Author: Newton Waweru |
|
|
|
|
18
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
19
|
What Are the Five Pillars of Cloud Security |

|
Addressing the security challenges in cloud computing requires an understanding of the pillars. A company needs insight into shared responsibility in managing data, privileges, users, and resources. Cloud security requires frameworks to ensure all po...
Author: Eunice Njuguna |
|
|
|
|
20
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
21
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
22
|
What Security Parameters are Present in the Cloud? |

|
The security parameters present in the cloud are the technologies designed to counter internal and external threats. They include data loss prevention applications, disaster recovery tools, and identity access management systems. Most cloud security ...
Author: Eunice Njuguna |
|
|
|
|
23
|
Understanding the Service Host Process (svchost.exe) and Why there are Are Multiple Instances of Svc |

|
Service Host Process (svchost.exe) handles many essential functions in our computers, and serves an invaluable purpose in their correct operation. Without svchost.exe, computers would not be able to operate multiple services or programs at once or ...
Author: James Fleming |
|
|
|
|
24
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
25
|
How to Unzip RAR Files on Windows for Free |

|
Do you have difficulty opening RAR files? RAR files are a popular form of data compression and can store large amounts of data in a single file. They are often used for software downloads, games, and multimedia. When you've downloaded a RAR file, y...
Author: James Fleming |
|
|
|
|
26
|
How do I remove write protection from my SanDisk? |

|
How do I remove write protection from my SanDisk?
While working on computers using external storage devices, they may be write-protected, which means that no operation can be done on them. A write-protected disk only allows the user to read data fro...
Author: James Fleming |
|
|
|
|
27
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
28
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
29
|
What Should You Do For a Fast TV Repair? |

|
Undoubtedly we all require fast TV repair for our devices; it's really frustrating to know that your TV needs a repair, and unfortunately, there is nothing you can do about it. I'm here to help you out with how you should handle such a situation.
Y...
Author: Nancy Museo |
|
|
|
|
30
|
What Does a Virus Scan Actually Do: A Definitive Guide |

|
A virus scan runs through a computer system to check malicious threats and remove them. There are two types of protection provided by antivirus software during a virus scan. This includes proactive and reactive protection. The former spots potential ...
Author: Tithi Raha |
|
|
|
|
31
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
32
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
33
|
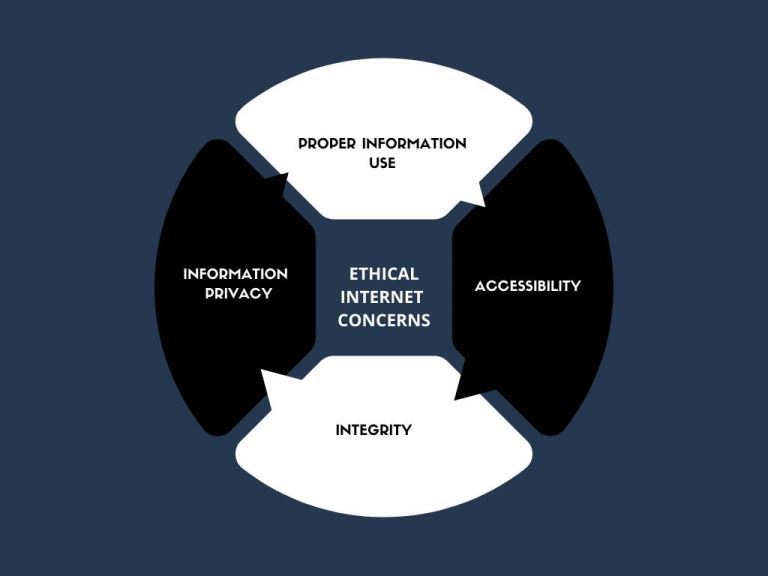
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
34
|
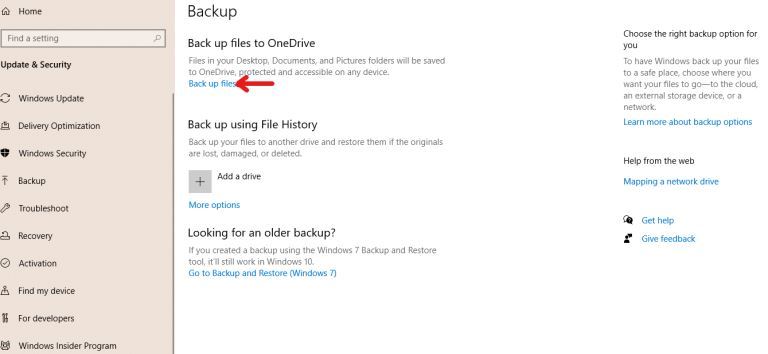
How to Backup Computer Windows 10? |
|
Backing up your computer windows 10 isn’t optional but a necessity.
The process starts by clicking on the “start” button on your Windows 10 system, navigating to the “setting” page, then to the “update & security” section, clicking on “backup,” and...
Author: Tithi Raha |
|
|
|
|
35
|
Password Protecting Folders and Files |

|
If you share a computer login, it might be in your best interest to use a password to keep private files safe from prying eyes. Of course, this won't protect you from malware or online security breaches, but it is an easy way to safeguard your privat...
Author: Trey Williams |
|
|
|