|
1
|
The Ultimate Guide to Converting Live Photos into Videos or GIFs on Your iPhone |

|
The Ultimate Guide to Converting Live Photos into Videos or GIFs on Your iPhone
In today's world of visual storytelling, photos are no longer enough. Users crave more interactive content, and Live Photos on the iPhone offer the perfect solution. Liv...
Author: James Fleming |
|
|
|
|
2
|
How Do You Identify The Cause And Fix Slow Download Speeds? |

|
A slow internet connection not only leaves everyone frustrated but also interrupts your work. Since there are so many problems that can cause the slowdown, it becomes difficult to identify the root cause of this disruption. However, you must find out...
Author: Tithi Raha |
|
|
|
|
3
|
Will Downloading Slow Down My Internet? How to Fix it? |

|
Your internet speed may slow down when one user on your Wi-Fi connection is downloading large-sized files or downloading multiple files at the same time. The same thing will happen when you upload large files as well. So, you may notice a connection ...
Author: Tithi Raha |
|
|
|
|
4
|
Is Download Slower Than Upload? Why & How to Fix it? |

|
In today's age, it's inevitable to have a good internet connection not only for gamers but also for ordinary people. So, you opt for a suitable plan from your internet service provider, each offering a variety of upload and download speeds. But, your...
Author: Tithi Raha |
|
|
|
|
5
|
Computer Tune Advice: How To Get Rid Of Viruses On Your Computer |

|
Computer viruses come in different ways and forms. It consists of code designed to interrupt the normal functioning of the computer and invade the computer system, software, and files. Most of them are harmful, and you need to protect your computer f...
Author: Faith Cheruiyot |
|
|
|
|
6
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
7
|
What is the Best Software for Making Video Tutorials? |

|
Are you planning to make video tutorials? Do you want to explain how your products and services function using the software? Video Tutorial software is ideal as it lets you edit, generate, manipulate and enhance videos. Such ensures the corporate and...
Author: Faith Cheruiyot |
|
|
|
|
8
|
Tablet Repair: Common Tablet Problems And Solutions |

|
After spending so much money on your new tablet, the expectations are always high. Many users dont have expectations of getting problems, thats not the reality. Tablet users experience several problems, and there are ways one can fix them.
The are ...
Author: Faith Cheruiyot |
|
|
|
|
9
|
What are the Tips to Create a Video Tutorial Quickly? |

|
Do you want to create quality, professional videos that can excite your audience? Are you wondering how you can create video tutorials quickly and easily? Tutorial videos are useful in teaching a process or giving procedural instructions. They allow ...
Author: Faith Cheruiyot |
|
|
|
|
10
|
How to Secure Your New Computer Against Viruses and Malware |

|
Do you have a new computer at home, at your workplace, or in your business? Are you worried that viruses and malware may attack your setup? You can use several ways to ensure that your new setup is safe from viruses and malware.
There are many cases...
Author: Caroline Chebet |
|
|
|
|
11
|
What Android Repair Experts/Technician Want You to Know |

|
When it comes to android repair, with many guides on social media, many people think it's a do-it-yourself task, forgetting they need expert services and advice. It would be great to learn more about android repair from an expert's perspective. This ...
Author: Nancy Museo |
|
|
|
|
12
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
13
|
Image Files: What Is a GIF, and How Do You Use Them |

|
Have you seen GIFs online or friends sharing them with you on social media platforms and have no idea how to use them? Worry not, GIFs are now part of social life, and it's an awesome idea to know everything there is to know about GIFS and, most impo...
Author: Janet Kathalu |
|
|
|
|
14
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
15
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
16
|
What should you do to a computer before you sell it? |

|
People sell or donate their computers every day, but most don't know what they should do to their computers before selling them. It's not always about backing up your data and selling it. There are so many factors to consider, precautions to take, an...
Author: Janet Kathalu |
|
|
|
|
17
|
Black and Decker DCM90: The Best Small Coffee Maker |

|
If you are like most people, you start your day with a cup of coffee. Coffee is such an appreciated cultural drink. Even in an office setting, coffee makes the list of some of the few accepted beverages. If you run an organization and think of invest...
Author: Ian Musyoka |
|
|
|
|
18
|
What is the difference between a wifi extender and a wifi router? |

|
There is confusion on wifi extenders and wifi routers. Some people argue that they are the same, and others don't understand the difference or functions. The truth of the matter is a wifi extender needs a wifi router to function and vice versa, but t...
Author: Janet Kathalu |
|
|
|
|
19
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
20
|
How not to get ripped off buying a used computer or used parts |

|
When purchasing a used computer for friends, I have unfortunately run into some scams or questionable deals in the past. I want to share a few things I look for to ensure my investment is not a waste of time, energy, and money.
On average, a used...
Author: James Fleming |
|
|
|
|
21
|
What Does Airplane Mode Do, and Is It Really Necessary? |

|
If you own a mobile phone or tablet, you are already familiar with the airplane mode feature. You are probably wondering what it is and if it is essential. This article will inform you all you need to know about airplane mode, why it is necessary to ...
Author: Gloria Mutuku |
|
|
|
|
22
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
23
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
24
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
25
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
26
|
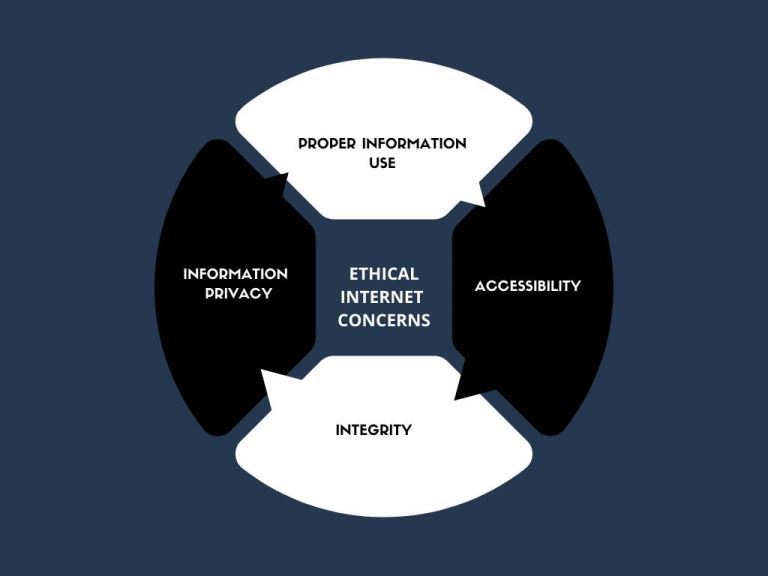
What Are Ethical and Unethical Practices Related to Internet Use? |
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
27
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
28
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
29
|
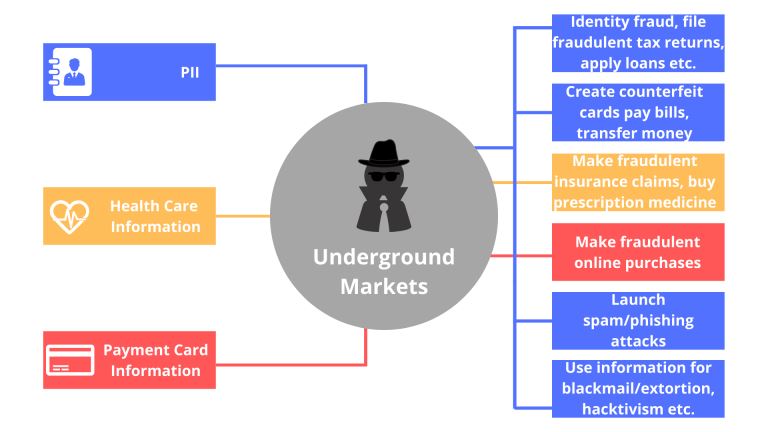
Do I Really Need To Care About My Privacy Online? |
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
30
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
31
|
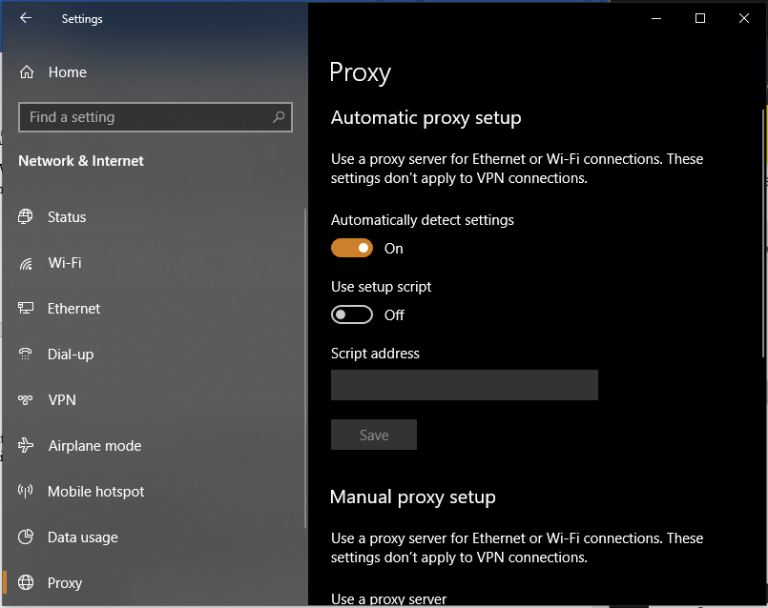
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
32
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
33
|
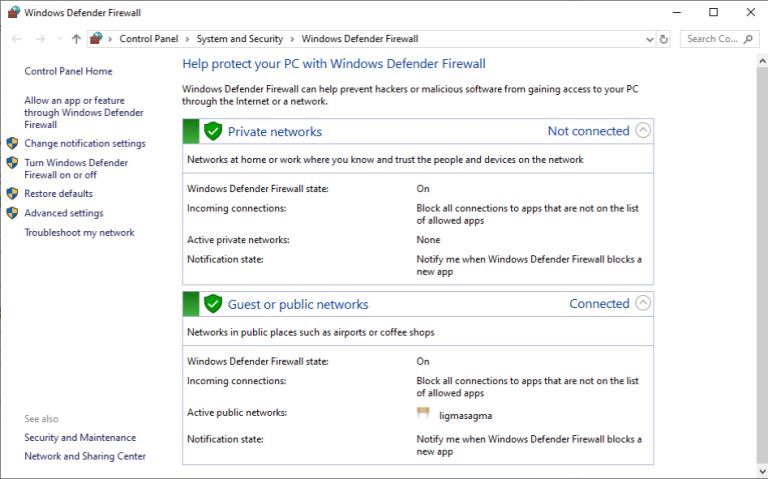
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
34
|
How Do I Destroy a Hard Drive? |

|
You can never be too careful when it comes to protecting your sensitive information, and you wouldn't be alone in thinking that just wiping a hard drive clean might not be taking things far enough. Whatever your reasons for wanting to completely dest...
Author: Trey Williams |
|
|
|
|
35
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|