|
1
|
What Does a Computer Repair Topeka KS Technicians Do |

|
Computer Repair Topeka, KS technicians perform all the necessary steps to repair the malfunctioning computer software and hardware. Upon calling a technician, they will first diagnose the issues with your computer system and ensure all are returned t...
Author: Tithi Raha |
|
|
|
|
2
|
Can Humans Read Binary Code Unlock the Secrets of Binary |

|
Have you ever wondered if humans can read binary code? If you're like many others, you may have encountered binary code in your computer science studies or even in your daily use of technology, but never quite understood how to read it. Well, you're ...
Author: Newton Waweru |
|
|
|
|
3
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
4
|
Binary Code vs. Gray Code [Master the Basics] |

|
Unlock the secrets of digital coding and get ahead with my comprehensive guide to Binary Code vs. Gray Code. I understand your need for clear, concise information and are here to help. Get ready to master the basics and gain confidence in your codin...
Author: Newton Waweru |
|
|
|
|
5
|
How Is Binary Converted to Electrical Signals? |

|
Uncover the mystery of binary code and delve into the conversion process to electrical signals. If you're seeking knowledge on binary-electrical signal conversion, this article offers a comprehensive and user-friendly examination of the topic. Expand...
Author: Newton Waweru |
|
|
|
|
6
|
How Do Computers Recognize Digital Signals? |

|
How do computers translate digital signals? Have you ever wondered how computers can understand and respond to digital signals? My comprehensive article delves deep into the technicalities and highlights the essential components that make computer re...
Author: Newton Waweru |
|
|
|
|
7
|
Binary Code vs. Morse Code: A Head to Head Analysis |

|
Seeking to comprehend the difference between Binary Code and Morse Code? Your search ends here. In this write-up, I will delve into a side by side examination of these two codes and examine their specific features and uses.
As a whole, Binary Code a...
Author: Newton Waweru |
|
|
|
|
8
|
Binary code VS ASCII [Understanding the Differences] |

|
This piece delves into the differences between binary and ASCII coding methodologies. If you're seeking information and a thorough examination of these coding techniques, your search has come to an end. I understand the confusion that comes with comp...
Author: Newton Waweru |
|
|
|
|
9
|
How to Fix My Microphone Doesn’t Work on Windows 11 |

|
How to Fix My Microphone Doesn't Work on Windows 11
Have you ever been on a vital video call and encountered your microphone unexpectedly ceasing to work? It can be incredibly frustrating. Unfortunately, it's an all too common issue with Windows 11;...
Author: James Fleming |
|
|
|
|
10
|
Is Binary Code Read From Right to Left? Learn the Direction of Binary |

|
Are you pondering the direction in which binary code is read? Rest easy, as you are not alone in this inquiry. A plethora of individuals share this curiosity. This piece will dispel any uncertainty and provide a comprehensive understanding of the rea...
Author: Newton Waweru |
|
|
|
|
11
|
Where Was Binary Code Invented? Tracing the Origins of Binary Code |

|
Are you curious about the origins of binary code? Look no further! Let me take you on a journey to uncover the history and inventor of this fundamental concept in computer science. Whether you're a student or simply interested in technology, I'm here...
Author: Newton Waweru |
|
|
|
|
12
|
The Easiest Way to Copy Text Messages from One Android Device to Another |

|
The Easiest Way to Copy Text Messages from One Android Device to Another
It's natural to question whether and how text messages may be transferred from one Android smartphone to another in case of a device swap. It takes a few minutes to copy your t...
Author: James Fleming |
|
|
|
|
13
|
Computer Tune-Up Tip: How To Remove Junk Files From Your Computer |

|
When using your computer to do different tasks, temporary files help you perform various actions and tasks. Once the task is over, the files remain without any deletion. They become useless, and you can't use them again. Most of them accumulate, and ...
Author: Faith Cheruiyot |
|
|
|
|
14
|
What are the Different Types of Tutorials? |

|
Do you always think about where you can learn how to do something? Most people look for tutorials to help them how to do tasks. Watching these videos gives you a deeper understanding and techniques for doing things better. It could be, installing ele...
Author: Faith Cheruiyot |
|
|
|
|
15
|
Why Your Ipad Repair is Missing the Mark (And How You Can Fix It) |

|
It's no secret that iPads have become an integral part of our lives. With so much depending on them, it's crucial to ensure they're in good shape. Unfortunately, many people are missing the mark regarding iPad repairs.
There are a number of reasons ...
Author: Faith Cheruiyot |
|
|
|
|
16
|
Data Restore: What are the 3 data recovery options? |

|
Data recovery involves different phases. Do you need some help to get your data back, or do you want to know more about data recovery? The recovery options entail different types of backup deployed by the users. It is essential to determine how long ...
Author: Faith Cheruiyot |
|
|
|
|
17
|
How To Fix An iPad Or Android Tablet That Won't Charge |

|
Imagine when you are all settled and ready to catch up with a friend or check something on your iPad or tablet, but when you connect it to the socket cant charge. That's a horrible experience, right? I have some good fix ideas that might save your da...
Author: Faith Cheruiyot |
|
|
|
|
18
|
How Can I Hack Someone's Wireless Network? |

|
Wireless networks or Wi-Fi are usually accessible to everyone who is within the transmission radius. You can use the hotspots in public places like restaurants, airports, parks, etc. This makes them more vulnerable to cyber-attacks. In fact, cracking...
Author: Tithi Raha |
|
|
|
|
19
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
20
|
What are the 5 Computer Problems and Their Solution? |

|
Are you experiencing a problem with your computer? Has your computer ever stopped operating abruptly? Fortunately, these issues may only require simple solutions to fix. You do not need an IT expert or engineer to solve them. Try some quick fixes to ...
Author: Faith Cheruiyot |
|
|
|
|
21
|
How to Change the Default System Font on Windows 10 |

|
To personalize your Windows PC, you can change the default Windows user interface font to the desktop element font. This font, called Segoe UI, appears in window titles, application menus, and other parts of the Windows graphical interface. I have a ...
Author: Berts Njoroge |
|
|
|
|
22
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
23
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
24
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
25
|
MS Word:How to Create and Manage a Table of Contents in Microsoft Word |

|
Have you ever tried to go through a numerous-page document that has no Table of Contents? It s such a hectic task to trace specific information that is way far in the paper. I found it essential to guide you through expert steps to create an excellen...
Author: Berts Njoroge |
|
|
|
|
26
|
Computer Tips: How to make my computer run like new? |

|
Do you wish your computer could look and run like the first day you bought it? The first day your computer was booting at a super speed, but in time, it’s so slow down. I will share a few things I picked up to make your computer run like a new one. ...
Author: Faith Cheruiyot |
|
|
|
|
27
|
How to Format PC Without CD? |

|
The most basic way of formatting a computer is by use of the original CD. There are. However, other systems installed ways of formatting a computer without the need for a CD. When you format your computer, you erase all the files installed and s...
Author: Gloria Mutuku |
|
|
|
|
28
|
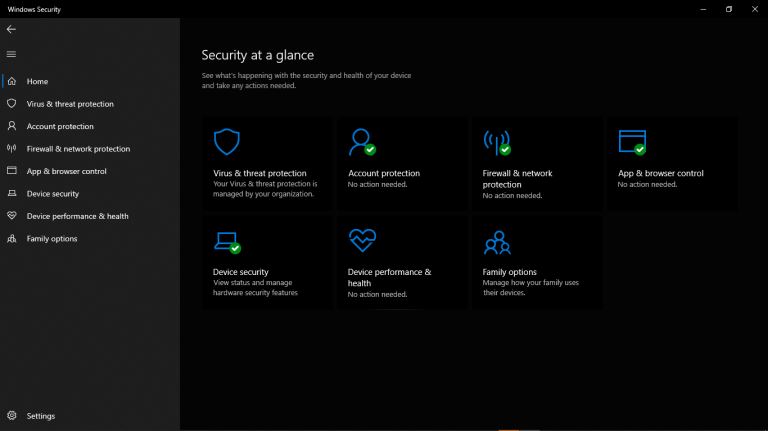
A Detailed Guide to Removing Ransomware in Windows 10 |
|
One of the main problems faced by internet companies today is Ransomware. For this reason, cybersecurity has continued to grow as an industry in general. Unfortunately, players on both sides can easily be described as the bad guys and the good guys. ...
Author: Collins Okoth |
|
|
|
|
29
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
30
|
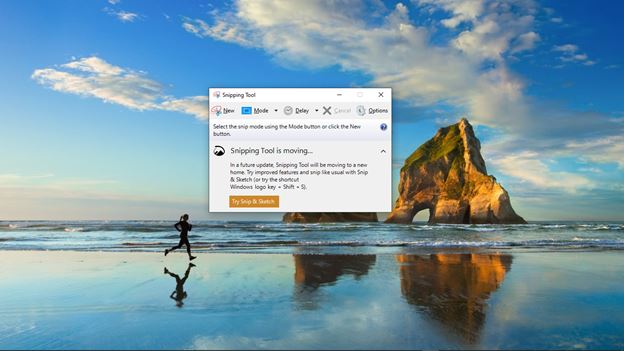
How to Take a Screenshot on a Widows Computer |
|
Taking screenshots has been a common necessity in recent years; it offers device users a unique way of sharing specific information on their screens. Screenshots have particularly been popular among mobile phone users; however, computer users may occ...
Author: Collins Okoth |
|
|
|
|
31
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
32
|
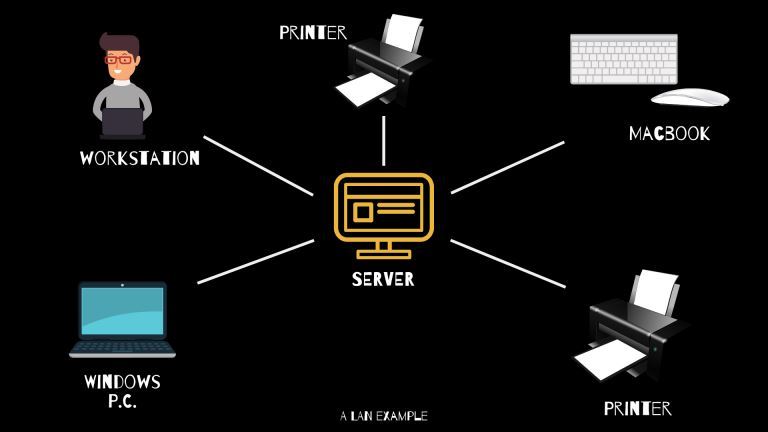
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
33
|
What Is an On-board Video Chipset |

|
A chipset refers to a complex set of components in an integrated circuit. A chipset's main purpose is to manage data flow sequentially between the processor, memory, and all other computer components. Normally, all chipsets are mounted on the motherb...
Author: Collins Okoth |
|
|
|
|
34
|
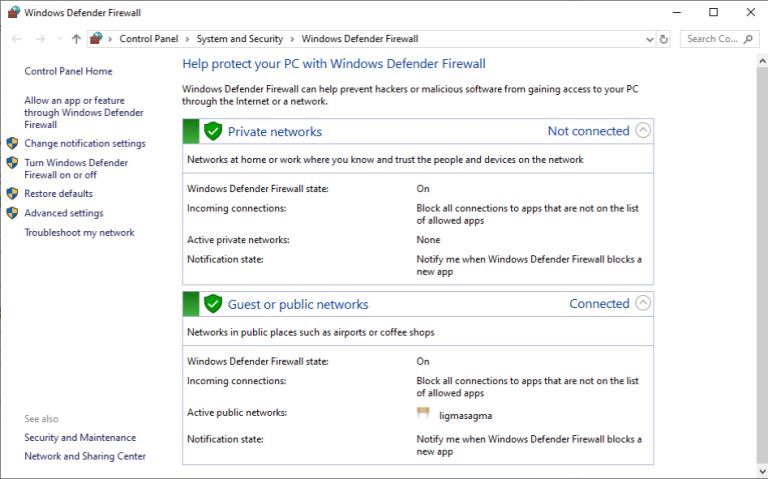
What Does a Firewall Do? |
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
35
|
Quantum Computers Explained Simply |

|
In the 1930s, Alan Turing developed the Turing machine. This machine comprises an unlimited length of tape that was subdivided into small squares. Each one of these little squares could either store a 1 or a 0 or be left blank. Consequently, a read a...
Author: Collins Okoth |
|
|
|