|
1
|
How Much Would it Cost to Fix Your iPhone |

|
It's common for the screen, charging port, or back screen of your iPhone to break. And when this happens, you only have two options; to repair or replace. Purchasing a new iPhone comes with standard prices that are easily verifiable online. But for r...
Author: Eunice Njuguna |
|
|
|
|
2
|
Types of Cybersecurity Threats Identifying Key Risks |

|
Cybersecurity threats are a growing concern in our digital age, and staying informed is essential. As someone who understands your need for help, I've delved into this topic to provide you with valuable insights. This article will cover various cyber...
Author: Newton Waweru |
|
|
|
|
3
|
The Biggest Cybersecurity Attacks Recorded |

|
Curious about the world of cybersecurity? To keep you informed, I have delved into the most massive cyber attacks ever recorded. Let's explore the critical incidents, their impact, and ways to stay protected together. By the end of this article, you'...
Author: Newton Waweru |
|
|
|
|
4
|
Ways you Could Be Exposing Yourself to a Cybersecurity Attack |

|
Are you concerned about cybersecurity? You're not alone! As we increasingly rely on technology, protecting ourselves from cyber threats is crucial. I've researched this topic extensively, so I'm here to help. In this article, I'll explore ways you mi...
Author: Newton Waweru |
|
|
|
|
5
|
How Does Biometrics Change the Face of Security Enhancing Security |

|
Navigating the world of security can seem like a daunting task. With new technologies like biometrics rising, feeling curious and overwhelmed is normal. This article will guide you through how does biometrics change the face of security, providing in...
Author: Newton Waweru |
|
|
|
|
6
|
Cyber Espionage and Information Warfare Threats to National Security |

|
Cyber Espionage & Information Warfare can be daunting, but don't worry - we're here to help. As someone who's delved into this complex topic, I empathize with your need for guidance. This article offers clear, human insights into the critical aspects...
Author: Newton Waweru |
|
|
|
|
7
|
Methods that Employees Can Expose Company Data Accidentally |

|
Concerned about employees accidentally exposing company data? You're not alone. I've delved into this issue, and I'm here to help. In this article, I'll explore standard methods that can lead to unintentional data leaks so that you can take preventiv...
Author: Newton Waweru |
|
|
|
|
8
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
9
|
The Danger of Mixing Cyberwarfare with Cyber Espionage |

|
Are you concerned about the potential hazards of combining cyber warfare and cyber espionage? You're not alone. As someone who has delved deep into this critical issue, I understand your concerns and am here to help. This article will explore the ris...
Author: Newton Waweru |
|
|
|
|
10
|
How to Protect Yourself from Cyberstalking Stay Safe Online |

|
Are you concerned about cyberstalking and your online safety? You're not alone. As an individual who delved into this issue, I empathize with your worries. In this article, I'll discuss practical steps to protect yourself from cyberstalking, so you c...
Author: Newton Waweru |
|
|
|
|
11
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
12
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
13
|
Cybersecurity Expectations vs Reality What You Need to Know |

|
Are you eager to learn about cybersecurity but feel overwhelmed by the jargon and technicalities? You're not alone, as many people find themselves navigating this intricate landscape with high expectations, only to be met with realities that often fe...
Author: Newton Waweru |
|
|
|
|
14
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
15
|
Knowing Your Android Phone Model. |

|
Knowing Your Android Phone Model.
Introduction.
A phone model is a style or design of a smartphone that producers often release in a series; examples may include the Tecno Camon 11 and Tecno Spark 7p.
Why know your phone models?
Every phone rel...
Author: James Fleming |
|
|
|
|
16
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
17
|
What Are Your Strategies To Avoid Being A Victim Of Cybercrime? |

|
Cybercrimes have been on the increase, with many unaware victims. When we hear about cybercrimes, we automatically think about hackers. But cybercrime is not just about hacking. It goes beyond that. Many people today use their devices, such as phones...
Author: James Fleming |
|
|
|
|
18
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
19
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
20
|
What Android Repair Experts/Technician Want You to Know |

|
When it comes to android repair, with many guides on social media, many people think it's a do-it-yourself task, forgetting they need expert services and advice. It would be great to learn more about android repair from an expert's perspective. This ...
Author: Nancy Museo |
|
|
|
|
21
|
How to clear my browser history |

|
Importance of clearing browser historyWhen you visit a website, your browser usually stores some information concerning the place, that is, the location of the site you visited, the file you have been using in running the application, and other downl...
Author: James Fleming |
|
|
|
|
22
|
What are the backup best practices using the cloud? |

|
Have you ever imagined what you would do if you lost all your crucial data? Of course, you cant imagine. Well, there is only one way to be sure of data safety and longevity- data backup. And the best thing is; cloud backup is here to make it easy to ...
Author: Faith Cheruiyot |
|
|
|
|
23
|
What Does a Virus Scan Actually Do: A Definitive Guide |

|
A virus scan runs through a computer system to check malicious threats and remove them. There are two types of protection provided by antivirus software during a virus scan. This includes proactive and reactive protection. The former spots potential ...
Author: Tithi Raha |
|
|
|
|
24
|
What Is a Burner Phone, and When Should You Use One |

|
I have been wondering how a burner phone can be used or if it is necessary to have one. I am sure I'm not the only one with such questions, so I did my research and wrote this article on burner phones and in which instances they can be helpful to bot...
Author: Janet Kathalu |
|
|
|
|
25
|
What to do when CCTV cameras power supply stop working? |

|
It has been a major issue among people when it comes to how to handle CCTV cameras. The major puzzle is how to tell if the power supply is the issue and what to do, how to detect the problem, why you are getting uncolored pictures, why your footage a...
Author: Janet Kathalu |
|
|
|
|
26
|
Digital Storage: How Big Are Gigabytes, Terabytes, and Petabytes? |

|
Have you come across data storage units like Petabytes, Gigabytes, and Terabytes? What do they mean in the real world of data storage? The articles will make you comprehend the complexity of units of data storage and their actual sizes. Let us see ho...
Author: Faith Cheruiyot |
|
|
|
|
27
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
28
|
Is my computer worth fixing? |

|
Constant computer breakdowns can be frustrating, and if you are a frequent visitor to the repair shop you might start thinking of buying a new computer. However, a computer technician can advise you on the condition of your machine and if it is likel...
Author: Gloria Mutuku |
|
|
|
|
29
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
30
|
What Are Ethical and Unethical Practices Related to Internet Use? |
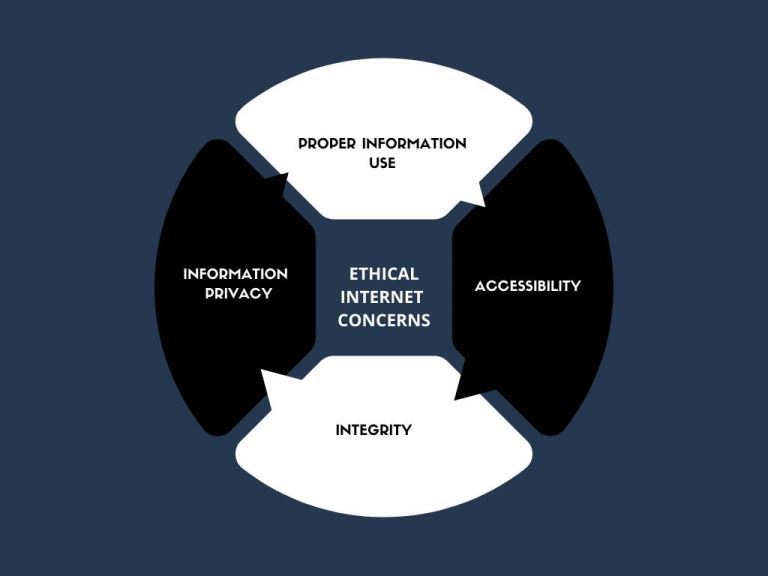
|
Information technology has made the world more accessible than ever in history. Different people from different parts of the world have the ability to access the internet and simultaneously make use of online resources. Do not be deceived that what...
Author: Ian Musyoka |
|
|
|
|
31
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
32
|
Do I need a Desktop PC or a Laptop? |

|
So you are in the market for a computer system, and can't seem to decide if a Desktop PC or a Laptop will serve you better. The computer you need is the one that best meets your particular needs. Get a Laptop if you value portability above all. But i...
Author: Ujunwa Chibuzor |
|
|
|
|
33
|
Do I Really Need To Care About My Privacy Online? |
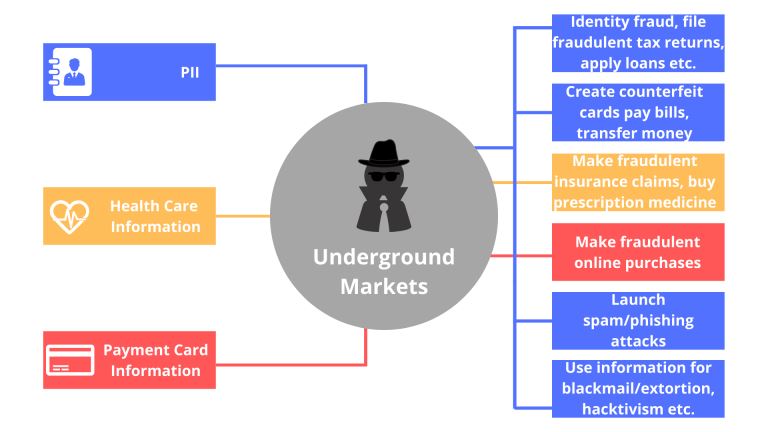
|
Online privacy seems almost non-existence when you factor in this age of likes, shares, tweets, and hashtags. Now more than ever, the activities of our daily lives are shared through social media. The worst part is that we are giving out this informa...
Author: Ian Musyoka |
|
|
|
|
34
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
35
|
How Does Cloud Sharing Work |
|
Whether you are a business dealing with loads of information or an individual saving personal files, data is an integral part of day-to-day activities. Handling data is a standard process, and as you collect, save, and share information, it is essent...
Author: Eunice Njuguna |
|
|
|