|
1
|
What Are The Duties of a Computer Repair Technician in Topeka KS |

|
From diagnosing initial issues to finding a solution, a computer repair technician in Topeka or any other area is responsible for all phases of the entire repair process. Moreover, the primary duty of a repair technician is to leave your device funct...
Author: Tithi Raha |
|
|
|
|
2
|
Is it Cheaper to Repair or Replace a Computer |

|
It's certain that no computer will last forever. But, to yield the best benefits out of your investment, you would want to stretch the life out as long as possible. And, computer repairs can really help you stretch out the life of your devices. Yet, ...
Author: Tithi Raha |
|
|
|
|
3
|
Is Binary Worth Learning? Know the Benefits of Learning Binary Code |

|
Are you wondering if learning binary is worth your time and effort? Discover the benefits of binary and see how it can enhance your career opportunities.
As a whole, learning binary can bring a multitude of benefits for individuals looking to en...
Author: Newton Waweru |
|
|
|
|
4
|
Complete Guide on How to Upgrade to Windows 10 From Windows 7 for Free |

|
Complete Guide on How to Upgrade to Windows 10 From Windows 7 for Free
Are you using Windows 7 and wondering how to upgrade to Windows 10 for free? Worry no more! Microsoft released a special upgrade offer for users of Windows 7 who want to upgrade ...
Author: James Fleming |
|
|
|
|
5
|
What Are Your Strategies To Avoid Being A Victim Of Cybercrime? |

|
Cybercrimes have been on the increase, with many unaware victims. When we hear about cybercrimes, we automatically think about hackers. But cybercrime is not just about hacking. It goes beyond that. Many people today use their devices, such as phones...
Author: James Fleming |
|
|
|
|
6
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
7
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
8
|
Computer Tune-up Tips: How to Keep Your PC Running Smoothly |

|
There are several benefits one gets when using a fast computer. It can be frustrating when you go through such experiences, but there is no need to worry. All you need to know first is the leading cause of slow performance, then you can see which rec...
Author: Faith Cheruiyot |
|
|
|
|
9
|
What Are The Modern Rules of In-home Computer Service? |

|
In the olden days, if your computer crashed or stopped working, you had to take it in for servicing. But now, with so many people working remotely and relying on their computers, there are new rules for when and how you should get your computer servi...
Author: Faith Cheruiyot |
|
|
|
|
10
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
11
|
How Do You Find Your Router's IP Address? |

|
Without knowing your router's IP address, you can't make any changes to it. Whether you want to create a new password for your Wi-Fi, change the name of your network, or switch to a different channel for boosting your connection, an IP address is a m...
Author: Tithi Raha |
|
|
|
|
12
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
13
|
New Computer Setup: What are the must-have programs on your new PC? |

|
Did you purchase a new PC? Congratulations! To get the most out of it, you need to add must-have programs to your new computer.
There are many must-have apps you need to install during your new computer setup. For Example, typing programs like notep...
Author: Caroline Chebet |
|
|
|
|
14
|
Bluetooth hacks: How to hack a car's Bluetooth? |

|
Bluetooth hacking is one of the most familiar hacks that hackers use. If you are a car owner, you must take precautions to keep your car safe from hackers. I want to keep myself and my car safe; that's why I researched and wrote this article to guide...
Author: Janet Kathalu |
|
|
|
|
15
|
My C Drive Is Full Without Reason, Ways to Solve It |

|
Computers store the system files within the drive C, and there are some instances when your device may give you a warning that this part of your hard drive is filled up. While it can fill up from file storage, in other cases, it could be due to other...
Author: Gloria Mutuku |
|
|
|
|
16
|
What Is a Burner Phone, and When Should You Use One |

|
I have been wondering how a burner phone can be used or if it is necessary to have one. I am sure I'm not the only one with such questions, so I did my research and wrote this article on burner phones and in which instances they can be helpful to bot...
Author: Janet Kathalu |
|
|
|
|
17
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
18
|
Password Security: How to Create a Strong Password (and Remember It) |

|
Have you ever typed a password and the system indicates that it is too weak or you add some symbols or numbers? As common as it is, a strong password saves you from intrusions and cyber attacks. It's hard to create a strong and memorable password wit...
Author: Fay Kokri |
|
|
|
|
19
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
20
|
What is HTTPs, and Why Should I Care about it? |

|
Most people often confuse HTTP and HTTPs, some think they can be used interchangeably, and so on. However, there is a simple and clear difference between HTTP and HTTPs in computer networking. Simply put, HTTPs is an abbreviation for Secure Hypertex...
Author: Collins Okoth |
|
|
|
|
21
|
What Does Airplane Mode Do, and Is It Really Necessary? |

|
If you own a mobile phone or tablet, you are already familiar with the airplane mode feature. You are probably wondering what it is and if it is essential. This article will inform you all you need to know about airplane mode, why it is necessary to ...
Author: Gloria Mutuku |
|
|
|
|
22
|
Computer Repair: How to Detect Crypto Mining Malware |

|
The vast growth of the cryptocurrency market has been something to marvel at over the past few years. However, the concept of anonymous payouts has given cybercriminals a reason to be part of the game. They have developed crypto-mining malware that c...
Author: Ian Musyoka |
|
|
|
|
23
|
Cyberstalking and How to Protect Yourself From Identity Theft |

|
Image: Internet Security
Creating a better online experience in the data and communication field has become a non-negotiable topic. Given the current move into the digital space, advanced data platforms and new communication channels have been cre...
Author: Ian Musyoka |
|
|
|
|
24
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
25
|
What types of cyber-attacks and how to prevent them? |

|
Cyber-attacks are real problems that are here to stay, as long as the internet. It doesn’t matter whether you are an individual, organization, or business. Cybersecurity risks will catch up with you, now or soon. With the spread of connectivity relia...
Author: Faith Cheruiyot |
|
|
|
|
26
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
27
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
28
|
A Detailed Guide to Removing Ransomware in Windows 10 |
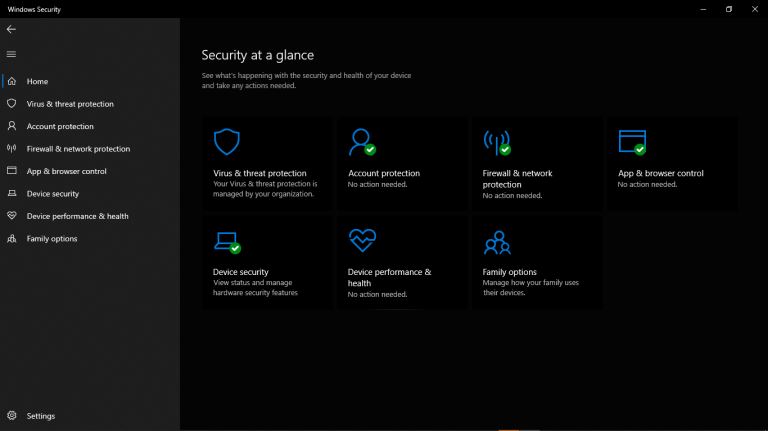
|
One of the main problems faced by internet companies today is Ransomware. For this reason, cybersecurity has continued to grow as an industry in general. Unfortunately, players on both sides can easily be described as the bad guys and the good guys. ...
Author: Collins Okoth |
|
|
|
|
29
|
What is Ransomware How it Works and How to Remove it |

|
Ransomware has grabbed the attention of many internet users, governments, and internet companies in recent years. Although Ransomware has been in existence for a long time, its effects have continued to be felt. Ransomware is short for Ransom Malware...
Author: Collins Okoth |
|
|
|
|
30
|
I Can't Open Email Attachments |

|
Email attachments are the files you receive alongside your email messages. The files come in different formats. The most common and widely used are the .pdf, .doc, .zip, or .html.
There are various other forms, and each requires specific computer p...
Author: Eunice Njuguna |
|
|
|
|
31
|
Computer Maintenance: How Do I Keep My Laptop Battery in Good Health? |

|
Image: A Laptop and Its Battery
The health of all batteries decreases over time with repeated charging and use, but this does not happen at the same speed. If you are given the same brand-new laptop on the exact day as someone else, the battery li...
Author: Ian Musyoka |
|
|
|
|
32
|
Sudden Computer Shutdown or Restart |
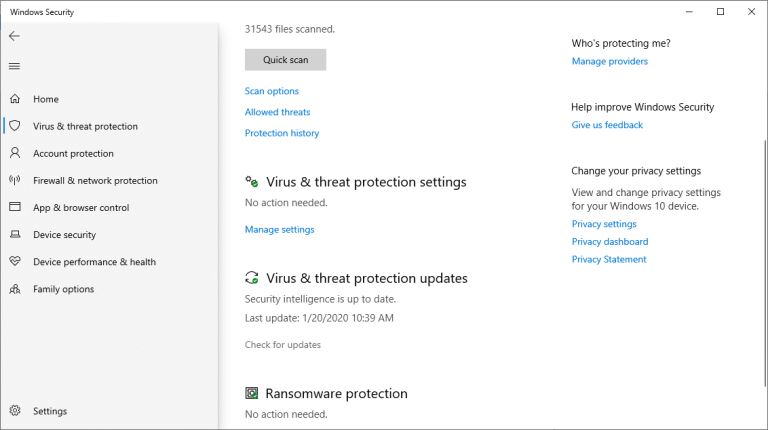
|
One of the most frustrating things you can experience as a computer user is a sudden shutdown or restart of the system. Not only could it lead to the loss of valuable work, but it may also be an indication that your PC is damaged. You may wonder what...
Author: Ian Musyoka |
|
|
|
|
33
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
34
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
35
|
What Does a Firewall Do? |
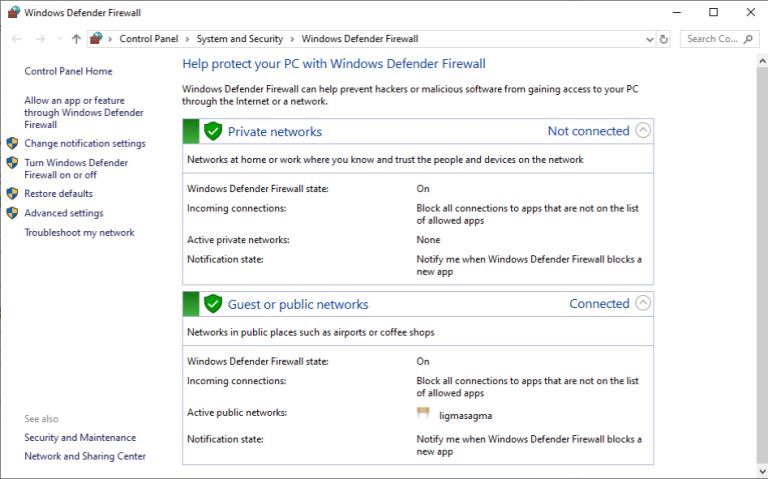
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|