|
1
|
How Can you Protect Yourself from Internet Hoaxes Digital Literacy |

|
Navigating the web can be tricky, with internet hoaxes lurking around. We understand your concern and are here to guide you. Our research will arm you with the knowledge to spot and evade these digital deceptions. This article is all about safeguardi...
Author: Newton Waweru |
|
|
|
|
2
|
Emerging Trends and Challenges in Cybersecurity |

|
In today's rapidly evolving digital landscape, emerging trends and challenges in cybersecurity are of great concern. Together, we'll explore these trends and challenges, arming you with the knowledge to protect your digital assets. This article will ...
Author: Newton Waweru |
|
|
|
|
3
|
How To Protect Children from Predators and Online Grooming |

|
As a caring parent, guardian, or educator, ensuring children's safety, especially from online predators and grooming, is a pressing concern. We understand your worries, and you're not alone. In this article, we're exploring key strategies to protect ...
Author: Newton Waweru |
|
|
|
|
4
|
What are the Challenges Faced in Cybersecurity Risks and Solutions |

|
Cybersecurity is a growing concern, and navigating its challenges can be daunting. You're not alone in seeking help; I'm here to provide the guidance you need. This article dives into the key obstacles faced in cybersecurity, offering practical insig...
Author: Newton Waweru |
|
|
|
|
5
|
The Biggest Cybersecurity Attacks Recorded |

|
Curious about the world of cybersecurity? To keep you informed, I have delved into the most massive cyber attacks ever recorded. Let's explore the critical incidents, their impact, and ways to stay protected together. By the end of this article, you'...
Author: Newton Waweru |
|
|
|
|
6
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
7
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
8
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
9
|
The Next Big Thing in Cyber Security Discover Innovative Solutions |

|
Ready to uncover the Next Big Thing in Cyber Security? You're not alone! As cyber threats evolve, so should our defenses. Fear not, I've delved deep into this crucial issue to help you stay informed and prepared. Join me in this article as we explore...
Author: Newton Waweru |
|
|
|
|
10
|
Binary code vs. Hexadecimal [A Guide to Understand the Differences] |

|
Are you struggling to understand the differences between Binary and Hexadecimal code? This comprehensive guide breaks down the complex concepts into easy-to-understand terms.
As a whole, Binary code and Hexadecimal are two methods of representing i...
Author: Newton Waweru |
|
|
|
|
11
|
6 Things You Need to Know About Vtube and the Creation of Your Own Avatar |

|
6 Things You Need to Know About Vtube and the Creation of Your Avatar
Introduction
Today, there are many different things online that people can do to earn money. For example, from starting a blog to talk about putting on make-up properly to runnin...
Author: James Fleming |
|
|
|
|
12
|
How Can I Tell If Cloud Computing Is Right For My Company? |

|
Cloud computing is right for you if your company needs support with data storage, infrastructure scaling, big data analytics, networking, backup service strategies, and application development. A business looking to boost productivity, create room fo...
Author: Eunice Njuguna |
|
|
|
|
13
|
What Are The Modern Rules of Backup Services? |

|
Did you know there are modern rules for backup services? Backing up data is vital to maintain computer function and avoid data loss.
There are many rules in the backup services, including always backing up your data, automating your backups, and con...
Author: Faith Cheruiyot |
|
|
|
|
14
|
What Are The Principles of Theatrical Design? |

|
Do you have a performance or a drama that you would like to perform? One follows many things when preparing a stage for a performance. It is difficult as it involves different professionals performing various tasks to ensure success.
There are diffe...
Author: Faith Cheruiyot |
|
|
|
|
15
|
What are the Latest Developments In TV Repair? |

|
Everyone should know about the latest trends in TV repair; as long as you own a TV, it's crucial to stay updated, and this excellent article will make you stay informed on them.
Fast TV repair services, easily accessible TV technicians, easily and r...
Author: Nancy Museo |
|
|
|
|
16
|
What Does a PC's BIOS Do, and When Should I Use It? |

|
BIOS, as a major system component, perform major tasks on computer bootup and beyond. However, knowing how to use it, when, and how to repair it can be a challenge. I have compiled the best tips on what BIOS does and when you need it.
There are sev...
Author: Berts Njoroge |
|
|
|
|
17
|
What are the backup best practices using the cloud? |

|
Have you ever imagined what you would do if you lost all your crucial data? Of course, you cant imagine. Well, there is only one way to be sure of data safety and longevity- data backup. And the best thing is; cloud backup is here to make it easy to ...
Author: Faith Cheruiyot |
|
|
|
|
18
|
Image Files: What Is a GIF, and How Do You Use Them |

|
Have you seen GIFs online or friends sharing them with you on social media platforms and have no idea how to use them? Worry not, GIFs are now part of social life, and it's an awesome idea to know everything there is to know about GIFS and, most impo...
Author: Janet Kathalu |
|
|
|
|
19
|
Computer Numbers: How Computers Generate Random Numbers |

|
Computer random numbers is a complex topic. It consists of 'yeses' and 'nos'. For a couple of years, I have been studying numbers and I am hereby crafting a well-simplified article to make you understand how computers generate random numbers. So, let...
Author: Berts Njoroge |
|
|
|
|
20
|
USB Type-C Explained: What is USB-C and Why You’ll Want it |

|
USBs, also known as (Universal Serial Bus), have existed for quite a while now. This technology has grown, extending its use cases to phones, computers, and laptops, replacing the mouse and keyboard PS/2 ports. Considering the history of this technol...
Author: Collins Okoth |
|
|
|
|
21
|
Computer Repair: How to Detect Crypto Mining Malware |

|
The vast growth of the cryptocurrency market has been something to marvel at over the past few years. However, the concept of anonymous payouts has given cybercriminals a reason to be part of the game. They have developed crypto-mining malware that c...
Author: Ian Musyoka |
|
|
|
|
22
|
How to Format PC Without CD? |

|
The most basic way of formatting a computer is by use of the original CD. There are. However, other systems installed ways of formatting a computer without the need for a CD. When you format your computer, you erase all the files installed and s...
Author: Gloria Mutuku |
|
|
|
|
23
|
What Is USB 3.0 |

|
USB is short for Universal Serial Bus. A USB is a plug-and-play interface that enables a computer to interact or communicate with other devices (Peripheral devices). There exists a wide range of USB-connected devices such as mice, keyboards, flash d...
Author: Collins Okoth |
|
|
|
|
24
|
What Is Form Factor on A Motherboard? |
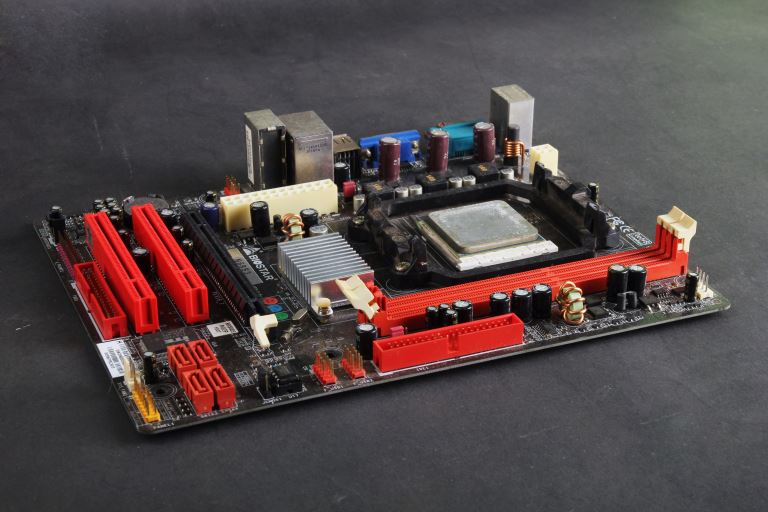
|
When talking about computers, the term 'motherboard' is highly likely to pop up on more than one occasion because it is vital. The primary function of the motherboard is to hold the microprocessor chip and give other parts the ability to connect to t...
Author: Delilah Daut |
|
|
|