|
1
|
The History of Cybersecurity and Hacking A Detailed Guide |

|
I understand your interest in the history of cybersecurity and hacking, as it's a fascinating subject. Rest assured, I've delved deeply into the topic and will guide you. This article will explore key milestones and developments that shaped this ever...
Author: Newton Waweru |
|
|
|
|
2
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
3
|
Things Every Employee Should Know about Cybersecurity Safety Tips |

|
Struggling with cybersecurity at work? You're not alone. As an employee, it's crucial to understand the basics of online safety. I've delved into the topic and can help you navigate this complex world. In this article, I'll explore key cybersecurity ...
Author: Newton Waweru |
|
|
|
|
4
|
Where Will Cyber Security be 10 Years from Now Navigating the Future |

|
As we navigate an increasingly digital world, you might wonder where cyber security will be in 10 years. After researching extensively, I'm confident in sharing valuable insights. This article will explore future cyber security trends and challenges...
Author: Newton Waweru |
|
|
|
|
5
|
The Next Big Thing in Cyber Security Discover Innovative Solutions |

|
Ready to uncover the Next Big Thing in Cyber Security? You're not alone! As cyber threats evolve, so should our defenses. Fear not, I've delved deep into this crucial issue to help you stay informed and prepared. Join me in this article as we explore...
Author: Newton Waweru |
|
|
|
|
6
|
My Account Has Been Hacked What Do I Do Secure Your Information |

|
Facing a hacked account can be a nightmare, and I understand your anxiety. Rest assured, I've delved deep into this issue and am here to help! This article will empathetically walk you through the essential steps to regain control and secure your acc...
Author: Newton Waweru |
|
|
|
|
7
|
How Is the Information Passed Through Wires Key Techniques Revealed |

|
Discover the secrets of information transmission through wires. Are you curious about how data is transmitted across wires? Struggling to understand the technicalities? Don't worry, you're not alone.
As a whole, information is passed through wires u...
Author: Newton Waweru |
|
|
|
|
8
|
Understanding SSID: What Is It and How Does It Work? |

|
Understanding SSID: What Is It and How Does It Work?
Wireless networks have become increasingly popular, enabling people to connect to the Internet and access network resources without the need for wired connections. One of the key components of wir...
Author: James Fleming |
|
|
|
|
9
|
Binary Code vs. Bytecode [Understand the Difference] |

|
Are you struggling to understand the difference between binary code and bytecode? This article will break down the key differences and give you a clear understanding of these coding concepts. Get ready to become a coding expert and impress your tech-...
Author: Newton Waweru |
|
|
|
|
10
|
Can Binary Code Be Used for Hacking? Uncover the Truth |

|
Are you eager to learn about the possibilities of using binary code for hacking? My comprehensive article explores the reality of binary code's capabilities in the realm of hacking.
In general, binary code can be applied as a technique in the field ...
Author: Newton Waweru |
|
|
|
|
11
|
Regaining Access to Your Android Phone: What to Do if You Forget Your PIN, Pattern, or Password |

|
Regaining Access to Your Android Phone: What to Do if You Forget Your PIN, Pattern, or Password
You use your Android phone to enter your PIN, pattern, or password like normal, but it doesn't work. After a few frustrating attempts, you realize you st...
Author: James Fleming |
|
|
|
|
12
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
13
|
NFC Guide: All You Need to Know About Near Field Communication |

|
As technology advances and smartphones become practically ubiquitous, the need for Near Field Communication (NFC) is rapidly increasing. NFC allows two electronic devices to wirelessly communicate with each other when touching or just by being in c...
Author: James Fleming |
|
|
|
|
14
|
Deciphering the World of Computer Acronyms: A Must-Know List |
|
Deciphering the World of Computer Acronyms: A Must-Know List
As technology continues to advance and evolve, it can be overwhelming to keep up with all the diff erent acronyms thrown around in the world of computers. There are so many other terms and...
Author: James Fleming |
|
|
|
|
15
|
How To Prevent Automatic Turning Off Of Your iPhone Screen |

|
iPhones are the most prestigious devices in the technological market today. They mainly symbolize class since only the people with money can afford them. Many people are obsessed with iPhones due to the many features that this phone has that other ...
Author: James Fleming |
|
|
|
|
16
|
6 Proven Ways to Remove Write Protection from USB in Windows 10 and Windows 11 |

|
6 Proven Ways to Remove Write Protection from USB in Windows 10 and Windows 11
How do you remove write protection from USB on Windows 10 or 11? Worry no more! With this simple guide, you can remove write protection from USB on a PC running the lates...
Author: James Fleming |
|
|
|
|
17
|
How To Protect the phone From Hackers Using Smart Security at Home app |

|
Every day, there's a new headline about a major company being hacked. While it's important to keep up with the latest security news, it's also essential to know how to protect your devices from hackers and scammers.
There are many ways hackers can g...
Author: Faith Cheruiyot |
|
|
|
|
18
|
Tips on Securing Your Computer From Hackers |

|
Are you concerned about the security of your computer? You should be, Hackers are becoming increasingly sophisticated, and they can easily steal your data or infect your computer with a virus if you're not careful.
There are different ways of secur...
Author: Faith Cheruiyot |
|
|
|
|
19
|
Step by Step Guide on How to Set up Your Network |

|
Today, almost every small business and home have a local network and an internet connection. The small area network allows several devices to connect to each other and also connect to the internet.
There are numerous ways you can set up your networ...
Author: Faith Cheruiyot |
|
|
|
|
20
|
Tablet Repair: How To Fix A Tablet That Won't Turn On |

|
Aspiring to fix your tablet that did not turn on or hire someone? Before starting, it is good to understand fundamental issues in tablet repair. Knowing that will help you be in a position to understand the fundamentals of repair and maintenance.
Th...
Author: Faith Cheruiyot |
|
|
|
|
21
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
22
|
How to unlock computer screen Windows 11? |

|
Windows 11 has quite new features that are not in previous Windows versions. Learning how to do simple-to-complicated tasks is mandatory to have an excellent experience on Windows 11. One such task is unlocking Windows 11 screen. This article will di...
Author: Berts Njoroge |
|
|
|
|
23
|
What are the backup best practices using the cloud? |

|
Have you ever imagined what you would do if you lost all your crucial data? Of course, you cant imagine. Well, there is only one way to be sure of data safety and longevity- data backup. And the best thing is; cloud backup is here to make it easy to ...
Author: Faith Cheruiyot |
|
|
|
|
24
|
Beginner Guide: How to Become an Ethical Hacker |

|
Dreaming to become an ethical hacker is one thing and becoming one in another one. It is not an easy ride in the park. The challenges and rough rides are part of the ethical hacker's journey. Allow me to take you the best ways to become an ethical ha...
Author: Berts Njoroge |
|
|
|
|
25
|
Windows 11: What you need to know about windows 11 before upgrading |

|
Windows 11 is out and has many features that are not in other operating systems. If you are eager to know what features, cost, benefits, and how to get windows 11, then you are in the right. There is so much in store for you.
There are several new ...
Author: Faith Cheruiyot |
|
|
|
|
26
|
Unlock PDF: How to Remove a Password From a PDF File |

|
The greatest frustration is when you want to access or print a PDF document, only to find out it has restrictions, and you are clueless about its original password. I am about to make you rest easy and enjoy removing the permission passwords from you...
Author: Fay Kokri |
|
|
|
|
27
|
Can My Employer Monitor My Work Computer At Home? |

|
An employer has every right to monitor the work computers of their employees at home. The employer will do so for various reasons: they will need to ensure their employees' productivity. It is also for the protection of the organization's software ...
Author: Gloria Mutuku |
|
|
|
|
28
|
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
29
|
How do Wi-Fi Hotspots Work |

|
A hotspot can be described as a locale or area that has an accessible wireless network. Wi-Fi hotspot is commonly used to refer to the available wireless connections in public places such as airports, restaurants, and coffee shops. Depending on your ...
Author: Collins Okoth |
|
|
|
|
30
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
31
|
What Is WAN/LAN? |
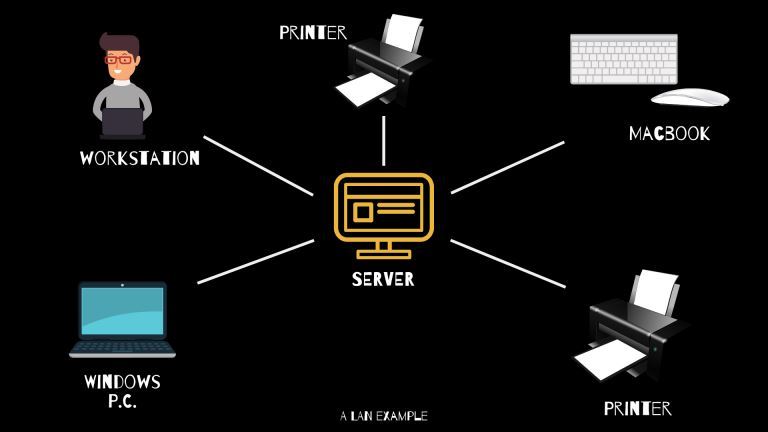
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
32
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
33
|
What Does a Firewall Do? |
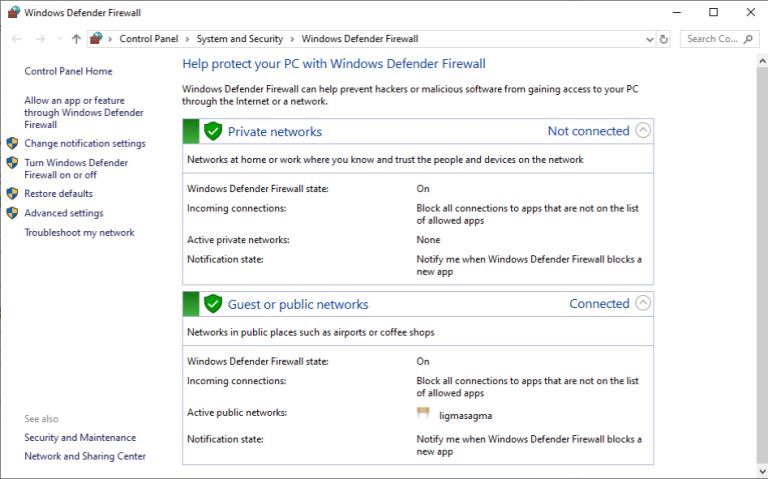
|
Before I started writing this, I thought to myself, “Who really needs a firewall?” But, as it turns out, most of us do. If your personal or company computer is connected to the internet, your network is always exposed to threats and risks. This mea...
Author: Ian Musyoka |
|
|
|
|
34
|
How Do I Know If I Have a Virus on My Laptop or Desktop Computer |

|
Making sure you have up-to-date anti-virus software installed is the easiest way of protecting your computer against viruses. This software is usually the first to notice that something is wrong. But with malware and hackers getting ever more sophist...
Author: Trey Williams |
|
|
|