|
1
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
2
|
Data Restore: What are the 3 data recovery options? |

|
Data recovery involves different phases. Do you need some help to get your data back, or do you want to know more about data recovery? The recovery options entail different types of backup deployed by the users. It is essential to determine how long ...
Author: Faith Cheruiyot |
|
|
|
|
3
|
What Are The Modern Rules of Backup Services? |

|
Did you know there are modern rules for backup services? Backing up data is vital to maintain computer function and avoid data loss.
There are many rules in the backup services, including always backing up your data, automating your backups, and con...
Author: Faith Cheruiyot |
|
|
|
|
4
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
5
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
6
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
7
|
What Are The Best Ways To Organize files on a New Computer? |

|
Did you just buy a computer and wonder how to organize your files? While it's not the most glamorous activity, organizing computer files is essential. They often build up without your knowledge until, one day, you turn on your computer to find a des...
Author: Caroline Chebet |
|
|
|
|
8
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
9
|
What the Best Game Console Repair Pros Do (and You Should Too) |

|
Are you looking for things that game console repair experts do and wish you could? Here is a full guide to help you get more skills in the console repair industry.
As a whole, game console repair pros do things like cleaning, maintenance, and game c...
Author: Caroline Chebet |
|
|
|
|
10
|
What Is a Burner Phone, and When Should You Use One |

|
I have been wondering how a burner phone can be used or if it is necessary to have one. I am sure I'm not the only one with such questions, so I did my research and wrote this article on burner phones and in which instances they can be helpful to bot...
Author: Janet Kathalu |
|
|
|
|
11
|
Why is my download speed so slow when I have fast internet? |

|
If your internet connection is fast but your internet download speed is slow, you can follow the workarounds below to resolve the issue.
There are several reasons why the internet may seem slow even if you have a high-speed internet connection. Re...
Author: Fay Kokri |
|
|
|
|
12
|
What to do when CCTV cameras power supply stop working? |

|
It has been a major issue among people when it comes to how to handle CCTV cameras. The major puzzle is how to tell if the power supply is the issue and what to do, how to detect the problem, why you are getting uncolored pictures, why your footage a...
Author: Janet Kathalu |
|
|
|
|
13
|
Things You Should Know about EFI System Partition (ESP) |

|
Most people have no idea what EFI system partition is, its components, its importance, or how it functions. In this article, you'll learn and understand everything there is to know about the EFI system partition.
There are four components of the EFI...
Author: Janet Kathalu |
|
|
|
|
14
|
What is the difference between a wifi extender and a wifi router? |

|
There is confusion on wifi extenders and wifi routers. Some people argue that they are the same, and others don't understand the difference or functions. The truth of the matter is a wifi extender needs a wifi router to function and vice versa, but t...
Author: Janet Kathalu |
|
|
|
|
15
|
What things can you do on the dark web? |

|
Have you always wondered what goes on in the dark web? I understand your curiosity, and I am here to break down all you need to know about the dark. Anything in darkness will be brought to light, literally.
There are a lot of activities that happen...
Author: Berts Njoroge |
|
|
|
|
16
|
Windows 11: What you need to know about windows 11 before upgrading |

|
Windows 11 is out and has many features that are not in other operating systems. If you are eager to know what features, cost, benefits, and how to get windows 11, then you are in the right. There is so much in store for you.
There are several new ...
Author: Faith Cheruiyot |
|
|
|
|
17
|
Why does my computer keep freezing |

|
We all have faced a situation where you are using your computer at work, office, or school, and it happens- your computer randomly freezes. Your computer becomes useless, and you lose all the information on the projects at hand. I will guide you on h...
Author: Berts Njoroge |
|
|
|
|
18
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
19
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
20
|
Why Do We Need Ethics for Internet Users? |

|
With the introduction of computers globally in the 1990s, the entire approach of working, communicating, and storing important information has changed. I mean, who would have thought that a machine can make one convey a message at any corner of the w...
Author: Collins Okoth |
|
|
|
|
21
|
Do I need a Desktop PC or a Laptop? |

|
So you are in the market for a computer system, and can't seem to decide if a Desktop PC or a Laptop will serve you better. The computer you need is the one that best meets your particular needs. Get a Laptop if you value portability above all. But i...
Author: Ujunwa Chibuzor |
|
|
|
|
22
|
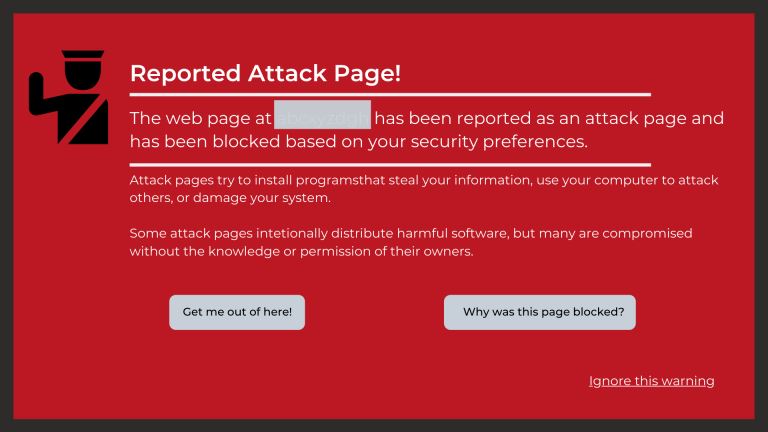
What Are the Signs a Website Has Been Hacked? |
|
If you own a business, you likely depend a lot on your website. From eCommerce to marketing, your website is the backbone of your transactions and everything in between. Without its help, you could face a lot of setbacks. Nevertheless, many business...
Author: Ian Musyoka |
|
|
|
|
23
|
Are Windows Computers better than Mac |

|
In everyday life, we often come across the term PC, which stands for a personal computer. This is the most direct definition of a PC; however, the term is also commonly used to refer to all other computers except Mac. Similarly, in this article, we w...
Author: Collins Okoth |
|
|
|
|
24
|
What Happens When a Site I Use Gets Hacked? |

|
In the Internet’s virtual world, security is very confusing as compared to the real world. Security is messy; difficult to develop and sustain. As much as the Internet is built around a system of protocols, these rules can often be ignored.
When...
Author: Ian Musyoka |
|
|
|
|
25
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
26
|
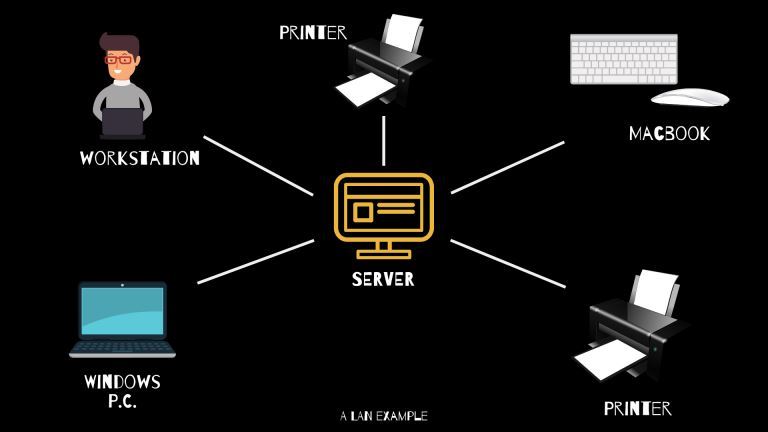
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
27
|
How to Remove Malicious Software |

|
Malware is software designed to damage, gain access to, or disrupt the normal functioning of the computer. Malware is valuable to cybercriminals because they use it to extract sensitive information, prevent access to the device, and steal money. The ...
Author: Delilah Daut |
|
|
|
|
28
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
29
|
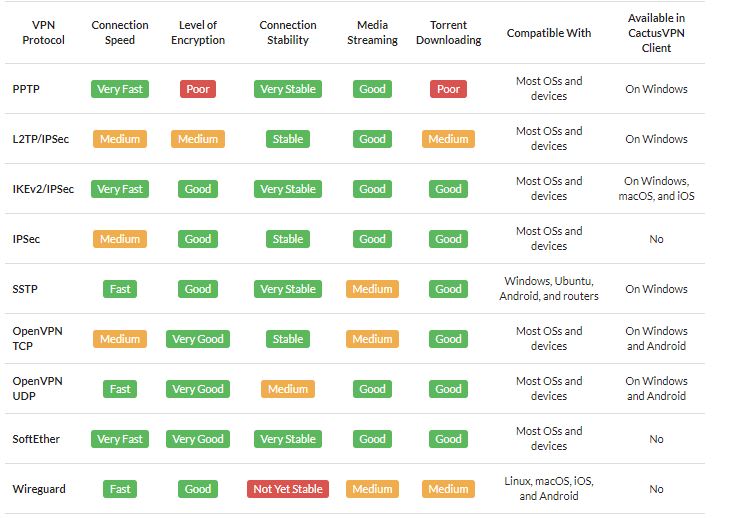
What Is a VPN? |
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|
|
30
|
What is The Darknet? |
|
The US Department of Defense developed an encrypted and anonymized network in the late ‘90s. The intention behind developing this network was to operate a secure and inaccessible network that would offer absolute protection and shielding from US Gove...
Author: Collins Okoth |
|
|
|
|
31
|
Does Adding RAM Increase Computer Speed? |
|
When purchasing a computer, one of the specifications to look out for is the amount of RAM it possesses. The system memory of your computer consists of two types of memory: virtual memory and physical memory (also called Random Access Memory). Unli...
Author: Ian Musyoka |
|
|
|
|
32
|
How Computers Work |
|
In the 1940’s Thomas Watson, the leader at IBM Corporation, famously predicted that the entire world would need about five computers. Surprisingly, six decades later, there are about one billion computers. Computers have changed a great deal over thi...
Author: Collins Okoth |
|
|
|
|
33
|
Password Protecting Folders and Files |

|
If you share a computer login, it might be in your best interest to use a password to keep private files safe from prying eyes. Of course, this won't protect you from malware or online security breaches, but it is an easy way to safeguard your privat...
Author: Trey Williams |
|
|
|
|
34
|
What Is Processor Virtualization Technology? |

|
In computing, many things can be made virtual, and there are various types of virtualization: network, desktop, and application virtualization. There are some challenges involved in the virtualization of modern processors (i.e., those built on x86 ar...
Author: Trey Williams |
|
|
|
|
35
|
What Is a Computer Processor Thread |
|
The brief answer to this question is that, in computer processing, a thread is a short sequence of programmed instructions or code.
But that’s not very helpful all by itself.
So, to properly understand what a computer processor thread is and what ...
Author: Trey Williams |
|
|
|