|
1
|
What Does a VPN Do Securing Digital Privacy |

|
Navigating the digital world can feel like walking through a minefield. Leveraging years of research, we'll unravel how VPNs safeguard your online presence, preserving your privacy and security. Brace yourself for an informative journey into what a V...
Author: Newton Waweru |
|
|
|
|
2
|
Why Should You Avoid Public Wifi Protecting Your Online Privacy |

|
Navigating the web safely is more crucial than ever. You might wonder, "What's the harm in using public Wi-Fi?" This article will explore why avoiding public Wi-Fi can significantly enhance online security. Let's delve into the risks and precautions ...
Author: Newton Waweru |
|
|
|
|
3
|
What are the 3 Main Pillars of Cybersecurity Internet Safety |

|
I understand cybersecurity can be complex and daunting, but don't worry - I'm here to help. As someone who has researched this topic extensively, I'll share the three main pillars of cybersecurity clearly and concisely, ensuring you gain a solid unde...
Author: Newton Waweru |
|
|
|
|
4
|
Ways you Could Be Exposing Yourself to a Cybersecurity Attack |

|
Are you concerned about cybersecurity? You're not alone! As we increasingly rely on technology, protecting ourselves from cyber threats is crucial. I've researched this topic extensively, so I'm here to help. In this article, I'll explore ways you mi...
Author: Newton Waweru |
|
|
|
|
5
|
How to Protect Your Company Against Cyber Espionage |

|
Concerned about cyber espionage threatening your business? You're not alone. As an experienced researcher, I understand the need to stay vigilant. In this article, I'll explore practical steps to safeguard your company, providing you with the tools t...
Author: Newton Waweru |
|
|
|
|
6
|
How to Detect Hidden Surveillance Cameras With Your Phone |

|
How to Detect Hidden Surveillance Cameras With Your Phone
Have you ever suspected that you were being watched but couldn't find any visible surveillance cameras? It's possible that the camera or cameras were hidden, making it difficult to detect the...
Author: James Fleming |
|
|
|
|
7
|
Controlling and Viewing devices connected to your Wi-Fi Network |

|
It's worth taking the time to see who is connected to your Wi-Fi network. Your home network security could be compromised if unauthorized users are piggybacking on your connection, slowing down your speeds and using up your data - all without you k...
Author: James Fleming |
|
|
|
|
8
|
Deciphering the World of Computer Acronyms: A Must-Know List |
|
Deciphering the World of Computer Acronyms: A Must-Know List
As technology continues to advance and evolve, it can be overwhelming to keep up with all the diff erent acronyms thrown around in the world of computers. There are so many other terms and...
Author: James Fleming |
|
|
|
|
9
|
Network Setup Tutorial - How to Set up a VPN Connection |

|
A VPN can add an extra layer of security and privacy. It helps you hide your identity so you can browse the internet safely and anonymously. The best thing is that you don't need to be a tech expert to set up your VPN.
There are many ways to set up...
Author: Faith Cheruiyot |
|
|
|
|
10
|
How In-home Computer Service Is Important to You |

|
There's no doubt that having a computer is important in this day and age. However, what happens when your computer breaks? Chances are you might not have the money to take it in for repair, or maybe you don't have the time to wait for it to be fixed....
Author: Faith Cheruiyot |
|
|
|
|
11
|
How To Protect Yourself in an Internet Security Breach |

|
Since the advent of the Internet, online security has been a concern for both individuals and businesses. Unfortunately, despite our best efforts, cyberattacks continue to occur with alarming frequency.
There are several things you can do to safegu...
Author: Faith Cheruiyot |
|
|
|
|
12
|
Network Setup Tutorial - Configuring a Remote Access Server |

|
Many offices have many users and teams with multiple branches. Using remote access servers enables businesses and organizations to let their staff access all the devices remotely. It mainly works in areas where the users cannot access the local area ...
Author: Faith Cheruiyot |
|
|
|
|
13
|
Is It Possible That VPNs Will Slow Down Your Internet? |

|
When your Wi-Fi is running at a snail's pace, nothing can seem more frustrating than that. It's nearly impossible to work, play games, watch videos and even at worst you can't even send messages to your loved ones. This scenario should not be a surpr...
Author: Tithi Raha |
|
|
|
|
14
|
What are the dos and don'ts for a new computer setup? |

|
If you got a new computer and wondering what you should do or not do, you are in the right place. This guide has all the information you need to have a seamless new computer setup
There are several dos and donts when setting up and new computer. Yo...
Author: Caroline Chebet |
|
|
|
|
15
|
Does private browsing actually work? |

|
With today's advanced technology, targeted ads and recommendation algorithms leave no space for privacy online. In line with this, you could expect your 'private' surfing through incognito mode to stay private, whereby you can remain anonymous. Howev...
Author: Collins Okoth |
|
|
|
|
16
|
What Does a VPN Hide? |

|
The more we use the internet, the more susceptible we become to cyber attacks. This makes a virtual private network (VPN) an essential tool to access the freedom of privacy when visiting streaming services, websites, and other places of interest on...
Author: Ian Musyoka |
|
|
|
|
17
|
What are Proxy Server Ports? |
|
Proxy servers are dedicated software systems that run on a computer and are intermediaries between two endpoint devices. These endpoint devices are usually a personal computer and a server. A server is a central computer from which other computers (c...
Author: Collins Okoth |
|
|
|
|
18
|
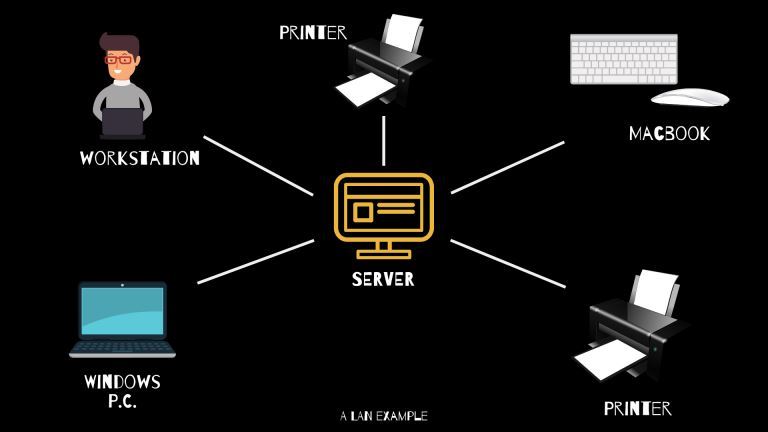
What Is WAN/LAN? |
|
Every day, computer networks grow in size and popularity. As the internet keeps stretching to other parts of the globe, the exchange of information among computers is constantly increasing. Understanding the connections that allow computer networks t...
Author: Ian Musyoka |
|
|
|
|
19
|
What's Wrong With Using Public Wi-Fi? |

|
Picture yourself in your favorite cafe, drinking a hot cup of coffee while taking advantage of the free Wi-Fi to update your feed or keep up with the news. I bet that to some of us, and this already sounds like a very familiar setting. However, did...
Author: Ian Musyoka |
|
|
|
|
20
|
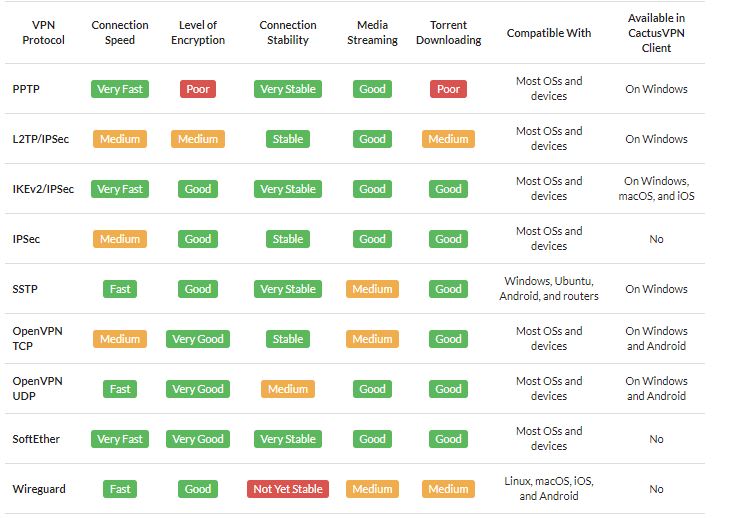
What Is a VPN? |
|
A VPN is short for Virtual Private Network. It is a collection of several networking schemes that allow computers to utilize public internet lines by creating a virtual network. VPNs have no specific standard models; however, it typically uses the pu...
Author: Collins Okoth |
|
|
|