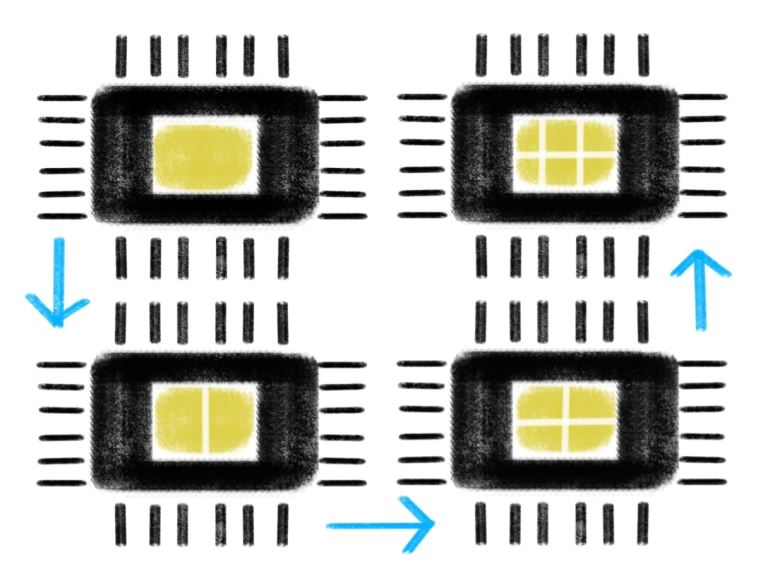
Data is stored in rows and columns within RAM. The CPU accesses the information in each cell by sending electrical signals - or commands - via the Memory Controller. To get to the right information, the Memory Controller must select the correct row,
Wednesday, October 16, 2019